Security policy configuration, Overview, Configuration tasks – H3C Technologies H3C SecBlade SSL VPN Cards User Manual
Page 73: Creating a security policy
65
Security Policy Configuration
Overview
Insecure terminal access to the internal network may lead to information leakage. Using the host
checking plug-in program, the system can check the operating system version, browser version,
processes, files and security software of the terminal and then determine which resources the terminal
can use.
A security policy specifies the method for evaluating the security of user terminals. It defines the items to
be checked. A security policy can define multiple categories of items to be checked, with each category
containing multiple items. If a terminal satisfies any item of a category, it is considered that the terminal
satisfies the category. Only when a terminal satisfies all the categories, does the terminal satisfy the
security policy.
Configuration Tasks
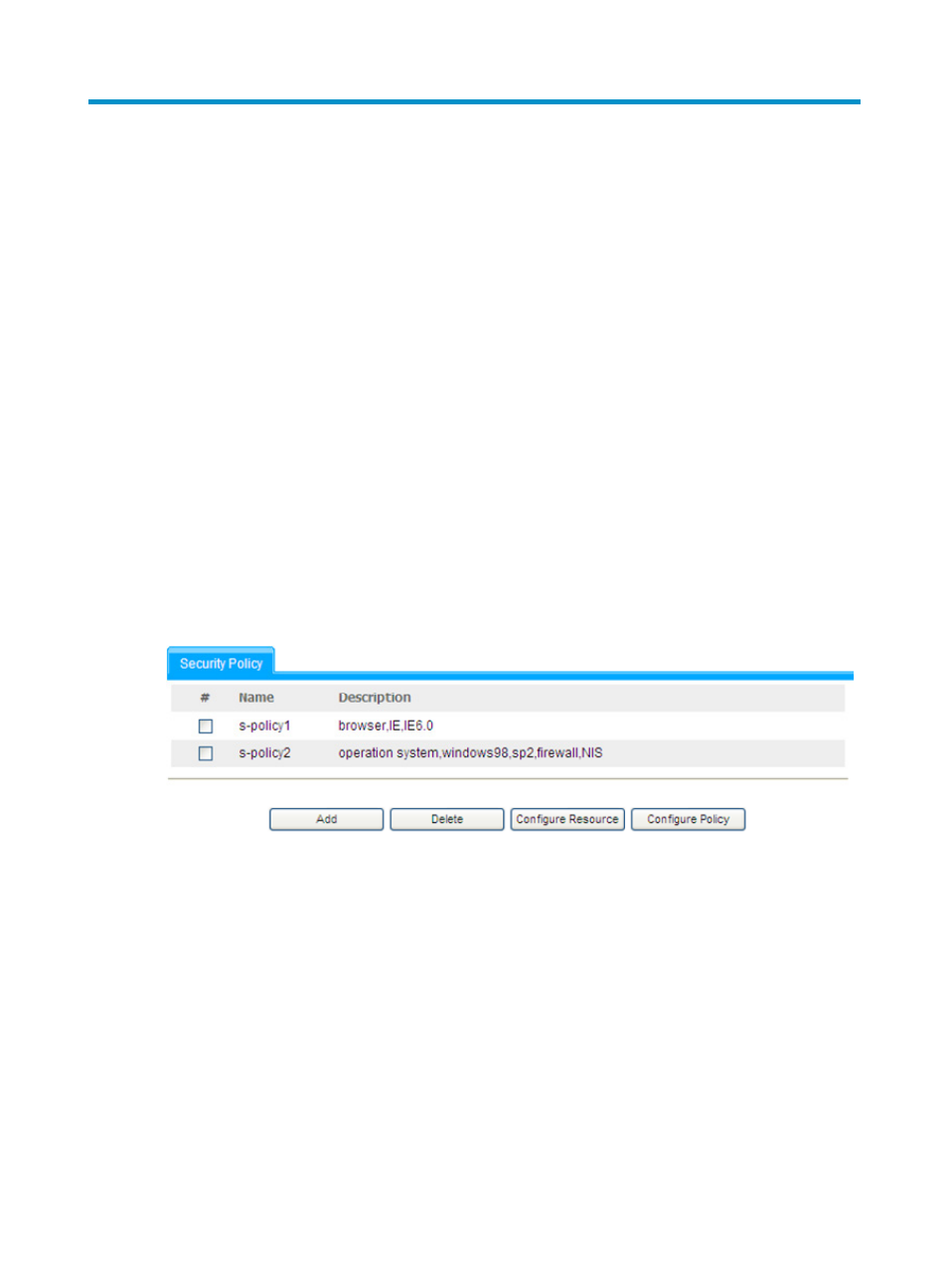
Select Domain > Security Policy from the navigation tree to enter the security policy management page,
Figure 49 Security policy management page
Perform these security policy configuration tasks.
•
•
Configuring Security Policy Resources
•
Creating a Security Policy
Click Add to create a security policy in the page shown in
.
