Rockwell Automation 1771-KA2 Communication Adapter Module User Manual
Page 40
Commands
Chapter 4
4-4
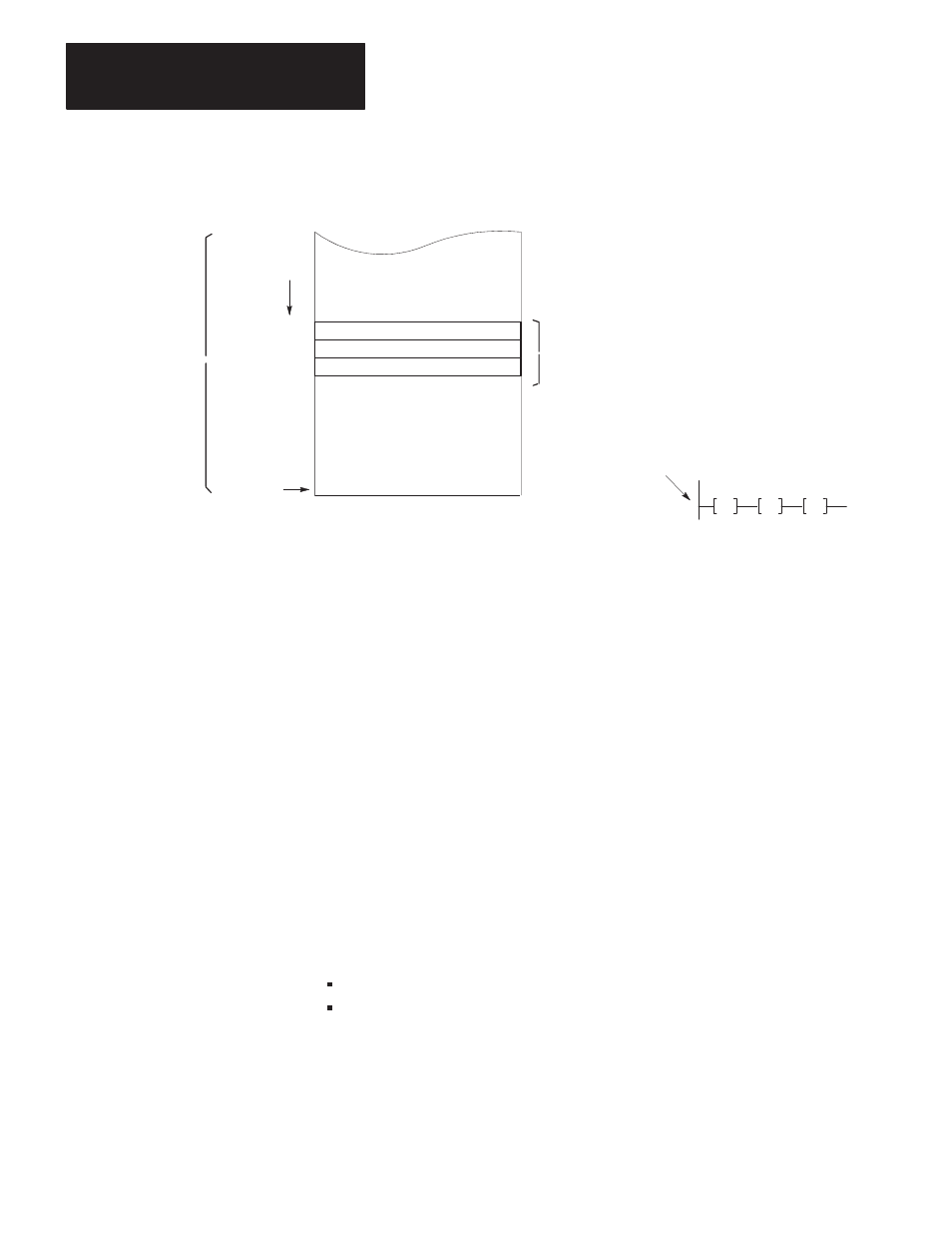
Figure 4.2
Protected/Unprotected Command Distinction
>
010
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
ЙЙЙЙЙЙЙЙЙ
>
Memory
Word
Address
End of
Data
Table
A protected
command can access
only specified
areas (determined
by memory access
rung in receiving
station) of memory
021
022
023
An unprotected
command can
access any area
of data table
memeory at a
receiving station
processor
a. Access Definition
G
G
G
021
023
Branch Start
Instruction
b. Memory Access Branch (typical)
10866-I
NOTE: For most write and bit write operations between station
processors, protected commands should be used. Because memory access
must be allowed by the program at the receiving station processor,
protected commands allow programmed write protection, which gives the
programmer an added degree of control over command execution.
Unprotected commands provide the same functions in transferring data,
but without this write protection at the receiving station.
A write command transfers word data from the local station processor to a
remote station. A single write command can send from 1 to 121
consecutive data table words.
There are 2 types of write commands that can be sent from a station
communication adapter module:
Protected write
Unprotected write
The distinction between these types of commands is their memory access.
Protected write commands are not executed by the receiving station unless
a memory access rung is programmed at that station and switch 1 on write
options is set. Because this allows added control over data transfer, use of
protected commands is recommended.
Write Commands
