Using idm with endpoint integrity systems – HP Identity Driven Manager Software Series User Manual
Page 89
3-35
Using Identity Driven Manager
Defining Access Policy Groups
Using IDM with Endpoint Integrity Systems
You can create access profiles in IDM to work in conjunction with endpoint
integrity (host integrity) applications to verify that systems attempting to
connect to the network meet security requirements. To use the Endpoint
Integrity support options you need to select the Endpoint Integrity option in
the IDM Preferences window (
Tools->Preferences->Identity Management
).
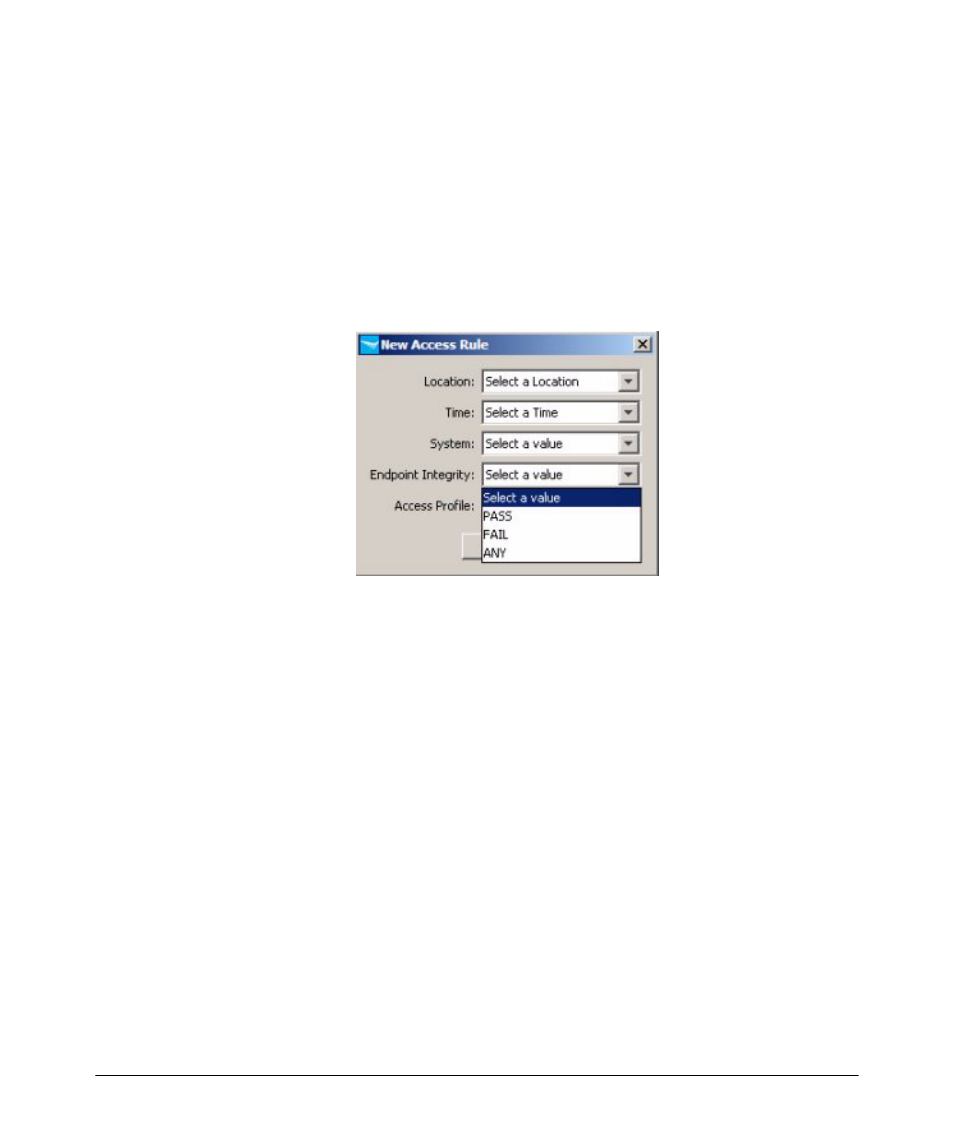
With the Endpoint Integrity preference set, the
Endpoint Integrity
option will
appear in the
Access Rules
windows.
•
Select
PASS to apply the access rule in cases where the system the
user is logged in on passes the endpoint integrity check.
•
Select
FAIL to apply the access rule in cases where the system the user
is logged in on fails the endpoint integrity check.
•
Select
ANY to apply the access rule regardless of the status passed
from the endpoint integrity system.
For example, if you want to restrict access to a specific (remediation) VLAN
when the endpoint integrity check fails, create a Location that specifies the
remediation VLAN, then create an access rule that will put the user on that
Location if the Host Integrity value is
FAIL
.
