TROY Group MICR_IRD 3015 Security Printing Solutions User’s Guide User Manual
Page 44
Section 3
System Planning and Implementation
Security Printing Solutions User’s Guide -- 50-
70540-001 Rev. A
3-5
Planning
Worksheet
(cont.)
Determine who will have access rights to the TROY printer – consider assigning individual user names,
and passwords to enhance MICR printing security and to allow audit tracking for each assigned user.
User Name ____________________________________________ Password _______________________
User Name ____________________________________________ Password _______________________
User Name ____________________________________________ Password _______________________
User Name ____________________________________________ Password_____ __________________
User Name ____________________________________________ Password _______________________
User Name ____________________________________________ Password _______________________
User Name ____________________________________________ Password _______________________
Decide if the TROYmark
™
and/or the TROY auditing features will be used – if so, the administrator must
choose the font styles used for capturing the check data for use in the TROYmark
™
background image and/or
the audit report.
Check Date Font ____________________________ Payee Name Font ____________________________
Convenience Amount Font ____________________________ Custom1 ____________________________
Custom 2 __________________________________ Custom 3 ___________________________________
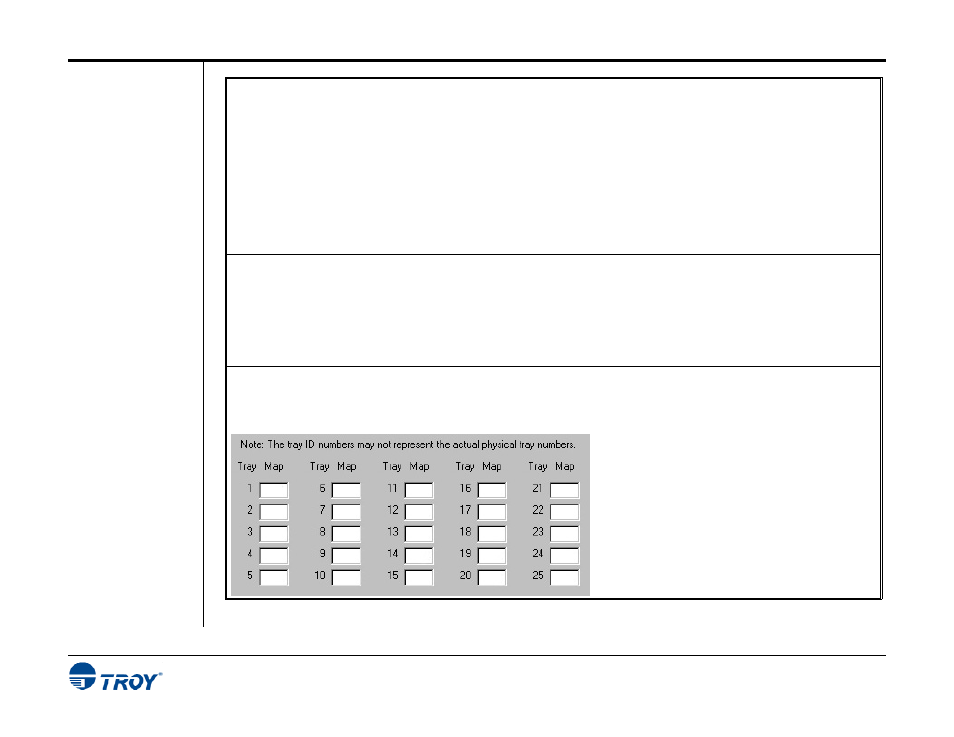
Determine the paper tray mapping assignment requirements – decide if requests for check paper from
any printer paper trays are to be disallowed unless the user provides a valid name and password. If so,
determine the paper tray to be mapped for non-compliant print requests (the paper tray containing standard
white paper).
