2 ipsec architecture, 1 ipsec algorithms, 2 key management – ZyXEL Communications Internet Security Appliance ZyWALL5UTM 4.0 User Manual
Page 300: 3 encapsulation, 1 ipsec algorithms 18.2.2 key management, Figure 144 ipsec architecture
ZyWALL 5/35/70 Series User’s Guide
Chapter 18 Introduction to IPSec
300
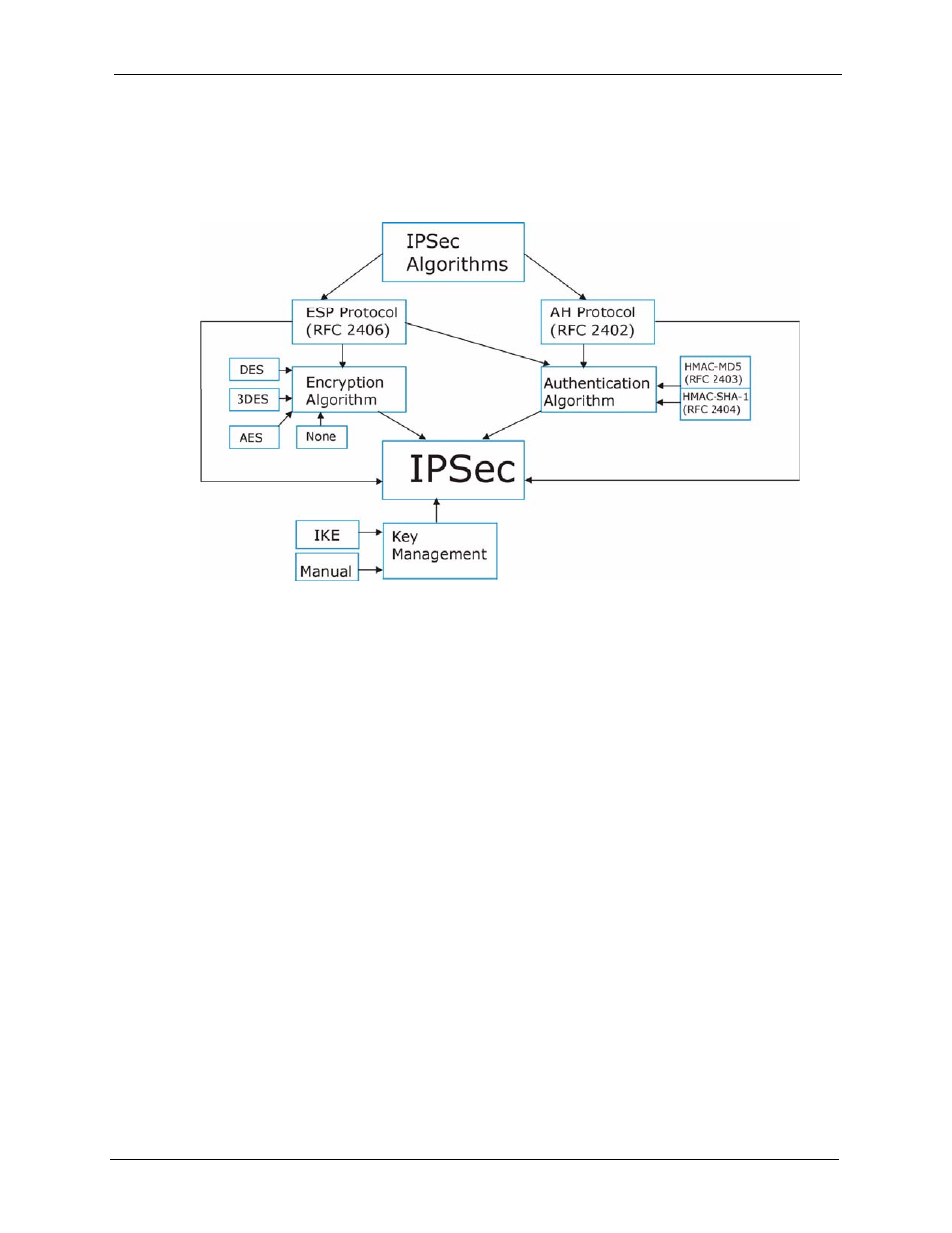
18.2 IPSec Architecture
The overall IPSec architecture is shown as follows.
Figure 144 IPSec Architecture
18.2.1 IPSec Algorithms
The ESP (Encapsulating Security Payload) Protocol (RFC 2406) and AH (Authentication
Header) protocol (RFC 2402) describe the packet formats and the default standards for packet
structure (including implementation algorithms).
The Encryption Algorithm describes the use of encryption techniques such as DES (Data
Encryption Standard), AES (Advanced Encryption Standard) and Triple DES algorithms.
The Authentication Algorithms, HMAC-MD5 (RFC 2403) and HMAC-SHA-1 (RFC 2404,
provide an authentication mechanism for the AH and ESP protocols. Refer to
18.2.2 Key Management
Key management allows you to determine whether to use IKE (ISAKMP) or manual key
configuration in order to set up a VPN.
18.3 Encapsulation
The two modes of operation for IPSec VPNs are Transport mode and Tunnel mode.
