Encryption and authorization algorithm overview – AML MT7570 Vehicle Mount Computer User Manual
Page 68
Encryption & Algorithm Overview
USER’S GUIDE
MT7570 Vehicle Mount Terminal
Encryption and Authorization Algorithm Overview
Before setting up any kind of wireless infrastructure or installing new devices within an existing site, it is a
good idea to fully understand the technology. The following is a brief explanation of wireless security
terms and how they relate to the MT7570 and other AML products.
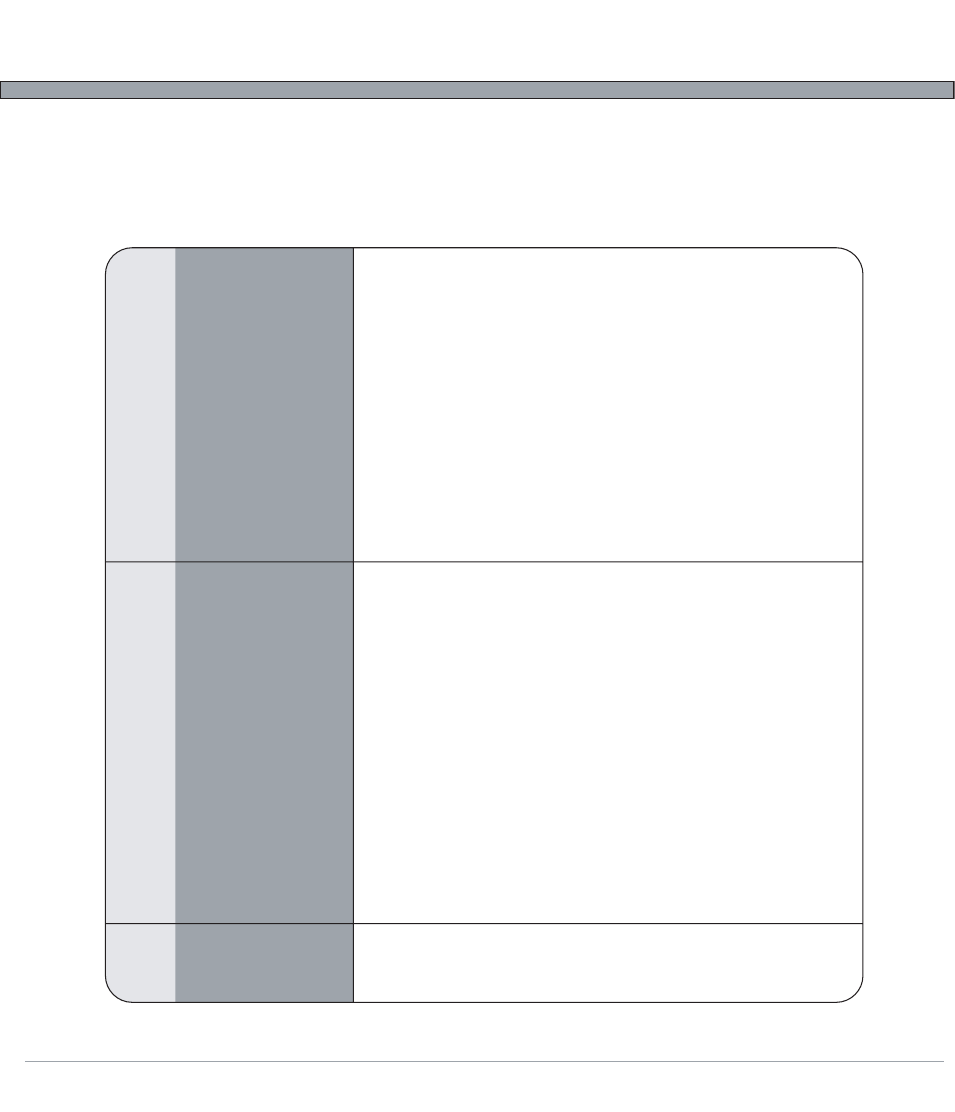
WEP
WPA
WPA2
Wired Equivalent
Privacy
Wifi Protected Access
Wifi Protected Access
Version 2
WEP was initially intended to provide a level of confidentiality on a wireless
network that was comparable to a wired infrastructure. WEP does not allow for
any true authorization (only encryption) and does not protect users or devices
from each other on the network. There are two main WEP types: WEP Open
System (Standard WEP) – All data transmissions are encrypted with the WEP
key. No attempt is made to authorize the client device. WEP Shared Key – In
Shared Key, a very insecure attempt to authorize the device is attempted. The
actual WEP encryption key is sent to the host (usually the access point) to verify
the identity of the device. This exposes the enciphering key to the network, and
should not be used. In a WEP enabled environment, each client holds the
common network encryption keys which can be either a 40-bit key for 64-bit
encryption or a 104-bit key for 128-bit encryption. These keys are common to all
devices on the network and are used to encrypt all data transmissions. Because
each network packet is encrypted with the same key, and because of flaws in the
actual cipher, WEP is no longer considered secure, and an attacker, depending
on network traffic, could determine the network encryption keys by eavesdrop-
ping on the transmissions. It has been demonstrated in a controlled environment
that these attacks can take as little as 10 minutes to determine a 40-bit key.
WPA was created in response to the weaknesses of WEP, and while it imple-
ments the majority of the IEEE 802.11i standard, it is not considered to be fully
compliant. WPA was only intended as a temporary measure to be used in place
of WEP while the final 802.11i standard was being drafted.
WPA was designed to work on all existing 802.11 hardware to provide a consid-
erable amount of protection compared to WEP.
WPA was designed for use with an 802.1x (commonly referred to as RADIUS)
server to provide authentication and to distribute encryption keys to the clients. It
is possible, however, to use WPA in “Personal” Pre-shared key (PSK) mode
which allows the benefits of WPA without the need of the external 802.1x server,
but this is considered to be less secure. Each client in a PSK environment holds
a common passphrase that is used to generate the keys. Weak passphrases are
major concerns when using PSK. One major improvement in WPA over WEP is
the Temporal Key Integrity Protocol (TKIP), which dynamically changes keys as
the system is used. The more often that the encryption key changes, the less
data a potential attacker can get on the key; even if they were to determine the
current key, once a new key was rotated in, they would be de-authenticated
again. WPA also defined the use of EAP for authentication of users, however it
does not define all of the EAP types that are employed in WPA2.
WPA2 contains the following components: 802.1x for authentication (entailing the
use of EAP and an authentication server), RSN (Robust Security Network) for
keeping track of associations, and AES-based CCMP encryption to provide
confidentiality, integrity and origin authentication.
