0 cisco asa configuration, 1 procedure 1: create new radius server instance, Cisco asa configuration – HID Cisco ASA and 4TRESS AAA Server User Manual
Page 4: Procedure 1: create new radius server instance
ActivIdentity 4TRESS AAA Web Tokens and Cisco ASA | Integration Handbook
P 4
External Use | June 8, 2012 | © 2012 ActivIdentity
2.0 Cisco ASA Configuration
This chapter describes how to manage a Cisco ASA. When a user signs into a Cisco ASA appliance, the Cisco
ASA forwards the user’s credentials to this authentication server to verify the user’s identity. You will create one
authentication server (an ActivIdentity 4TRESS AAA RADIUS Server) to validate the user’s one-time password
generated by a Web soft token.
2.1
Procedure 1: Create New Radius Server Instance
When using an external RADIUS server to authenticate Cisco ASA users, you must configure the server to
recognize the Cisco ASA as a client and specify a shared secret for the RADIUS server to use to authenticate the
client request.
To configure a connection to the RADIUS server on a Cisco ASA SSL VPN appliance and to define the RADIUS
Server instance, perform the following steps.
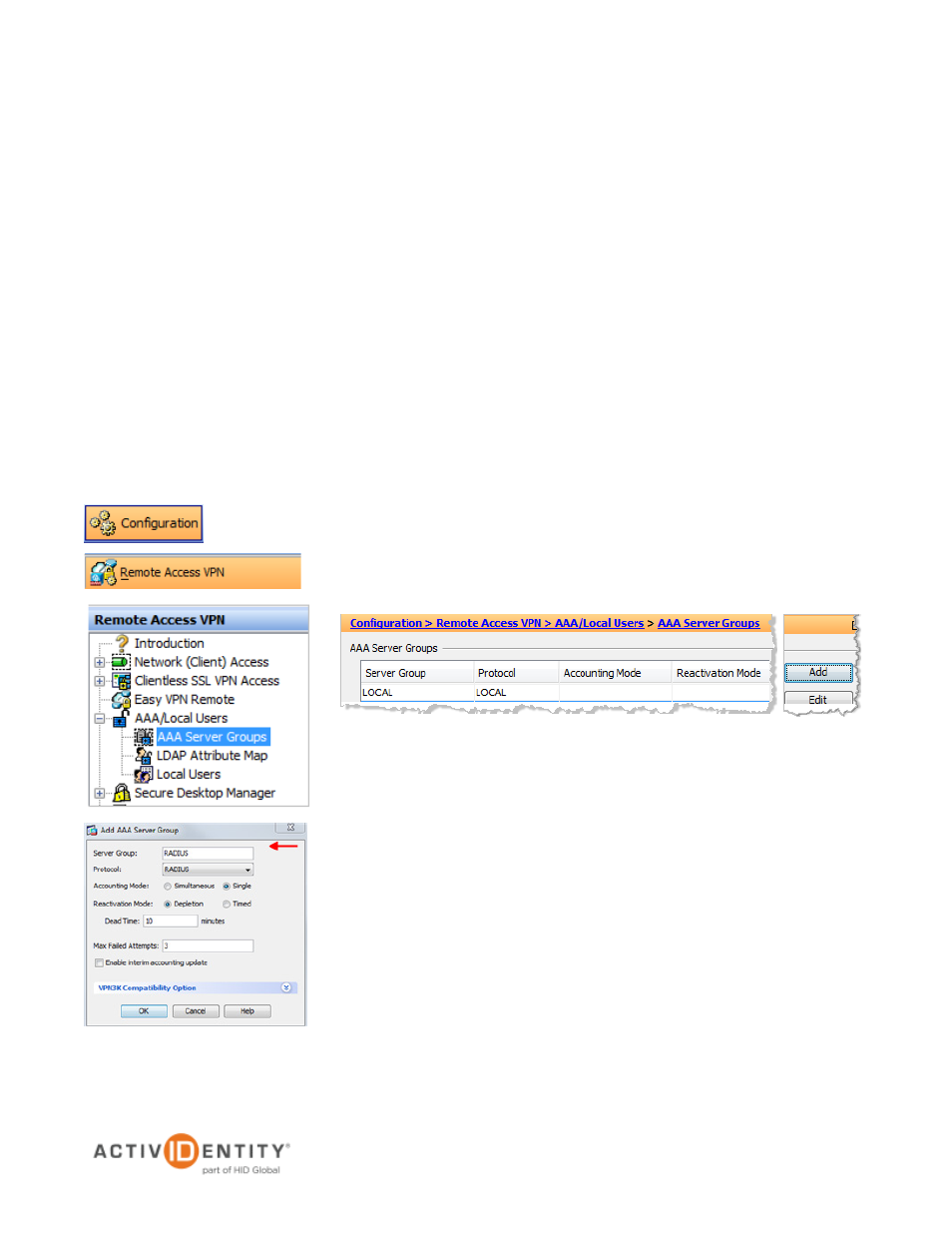
Getting Started
1. In the ASDM console, navigate to
Configuration-> Remote Access
VPN -> AAA/Local User, and then click AAA Server Groups.
2. Click
Add at the far right of the page displayed.
The nearby dialog is displayed.
3. Enter a
Server Group name, and then select RADIUS for the
Protocol.
4. Click
OK.
Repeat the process to add a backup RADIUS server.
