Netopia R2121 User Manual
Page 181
Security 14-19
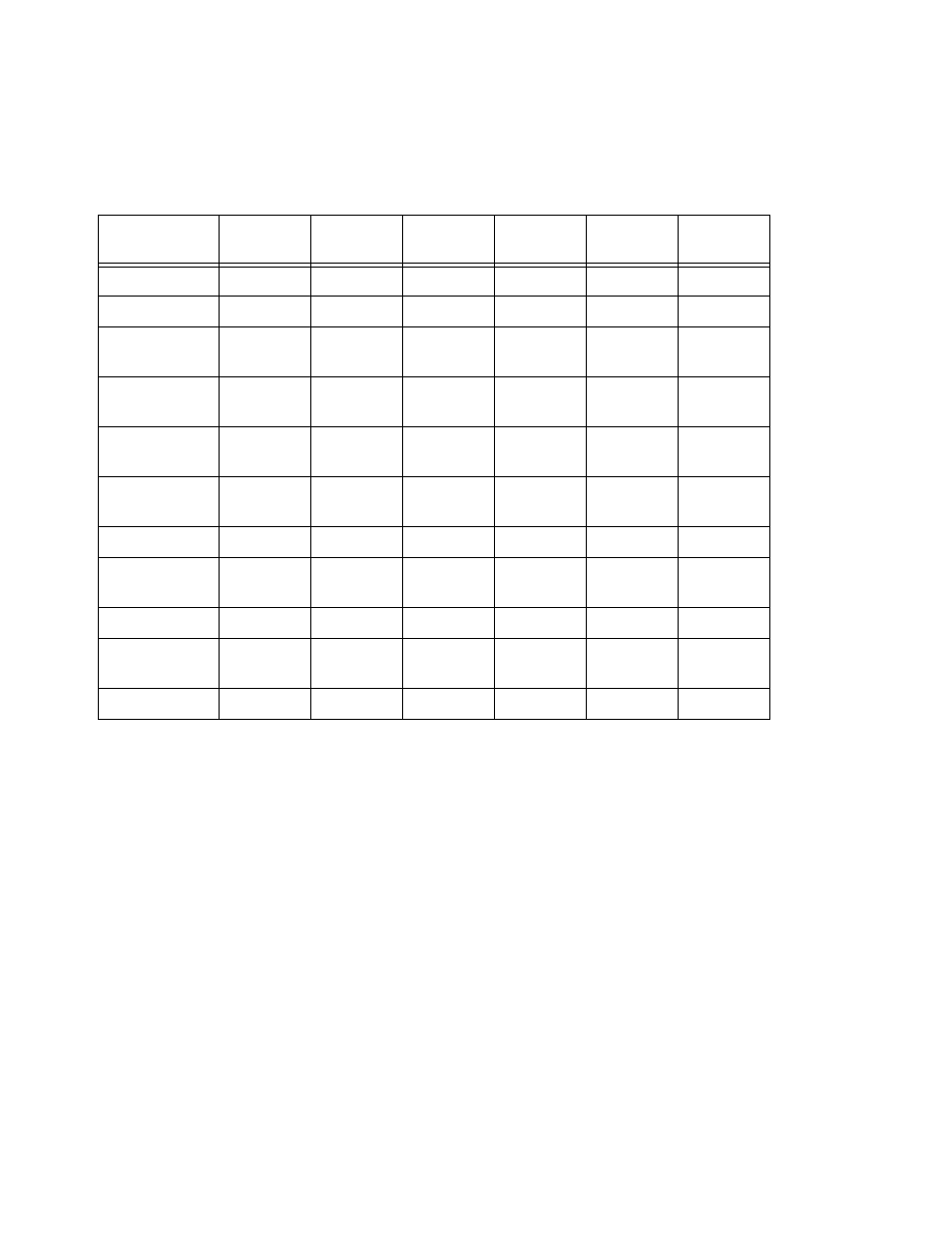
The five input filters and one output filter that make up Basic Firewall are shown in the table below.
Basic Firewall’s filters play the following roles.
Input filters 1 and 2: These block WAN-originated OpenWindows and X-Windows sessions. Ser vice origination
requests for these protocols use por ts 2000 and 6000, respectively. Since these are greater than 1023,
OpenWindows and X-Windows traffic would other wise be allowed by input filter 4. Input filters 1 and 2 must
precede input filter 4; other wise they would have no effect as filter 4 would have already passed OpenWindows
and X-Windows traffic.
Input filter 3: This filter explicitly passes all WAN-originated ICMP traffic to permit devices on the WAN to ping
devices on the LAN. Ping is an Internet ser vice that is useful for diagnostic purposes.
Input filters 4 and 5: These filters pass all TCP and UDP traffic, respectively, when the destination por t is
greater than 1023. This type of traffic generally does not allow a remote host to connect to the LAN using one
of the potentially intrusive Internet ser vices, such as Telnet, FTP, and WWW.
Output filter 1: This filter passes all outgoing traffic to make sure that no outgoing connections from the LAN
are blocked.
Setting
Input filter 1
Input filter 2
Input filter 3
Input filter 4
Input filter 5
Output filter
1
Enabled
Yes
Yes
Yes
Yes
Yes
Yes
For ward
No
No
Yes
Yes
Yes
Yes
Source IP
address
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
Source IP
address mask
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
Dest. IP
address
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
Dest. IP
address mask
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
0.0.0.0
Protocol type
TCP
TCP
ICMP
TCP
UDP
0
Source por t
comparison
No Com-
pare
No Com-
pare
N/A
No Com-
pare
No Com-
pare
N/A
Source por t ID
0
0
N/A
0
0
N/A
Dest. por t
comparison
Equal
Equal
N/A
Greater
Than
Greater
Than
N/A
Dest. por t ID
2000
6000
N/A
1023
1023
N/A
