4 vpn tunnels – Cradlepoint MBR1400LE User Manual
Page 121
CRADLEPOINT
MBR1400| USER MANUAL Firmware ver. 3.4.1
© 2012 CRADLEPOINT, INC. PLEASE VISIT
HTTP://KNOWLEDGEBASE.CRADLEPOINT.COM/
FOR MORE HELP AND RESOURCES
PAGE 119
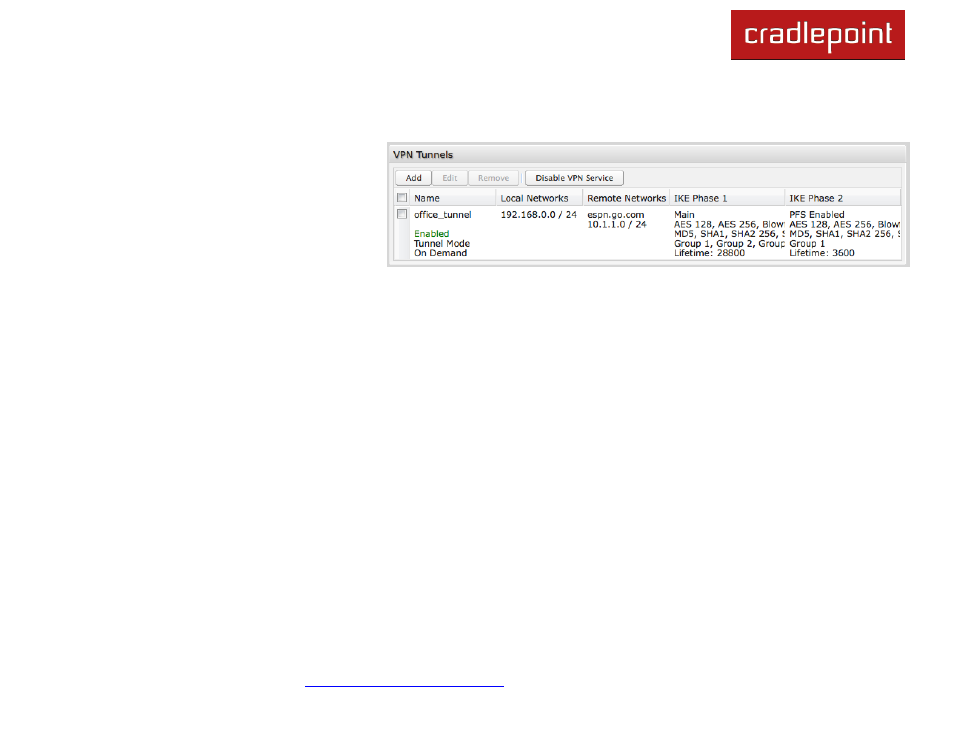
7.4 VPN Tunnels
VPN (virtual private network) tunnels are
used to establish a secure connection to a
remote network over a public network. For
example, VPN tunnels can be used across
the Internet by an individual to connect to an
office network while traveling or by two office
networks to function as one network. The
two networks set up a secure connection
across the (normally) unsecure Internet by assigning VPN encryption protocols.
The MBR1400 uses IPsec (Internet Protocol security) to authenticate and encrypt packets exchanged across the tunnel.
To set up a VPN tunnel with the MBR1400 on one end, there must be another device (usually a router) that also supports
IPsec on the other end.
IKE (Internet Key Exchange) is the security protocol in IPsec. IKE has two phases, Phase 1 and Phase 2. The MBR1400
has several different security protocol options for each phase, but the default selections will be sufficient for most users.
The VPN tunnel status page allows you to view the state of the VPN tunnels. If a tunnel fails to connect to the remote site,
check the System Logs for more information. You may double click on a cell to directly edit that information.
Click Add to configure a new VPN tunnel.
