Rainbow Electronics DS2432 User Manual
Page 15
PRELIMINARY
DS2432
15 of 30
Compute Next Secret [33h]
Some applications may require a higher level of security than can be achieved by a single, directly written
secret. For additional security the DS2432 can compute a new secret based on the current secret, the
contents of a selected memory page, and a partial secret that consists of all data in the scratchpad. To
install a computed secret the master issues the Compute Next Secret command, which activates the
512-bit SHA-1 engine, provided that the secret is not write-protected. Table 1 shows how the various data
components involved enter the SHA engine and how a portion of the SHA result is loaded into the
secret's memory location. The SHA computation algorithm itself is explained later in this document. The
Compute Next Secret command can be applied as often as desired to increase the level of security. The
bus master does not need to know the device’s current secret in order to successfully compute a new one
and then overwrite the existing secret.
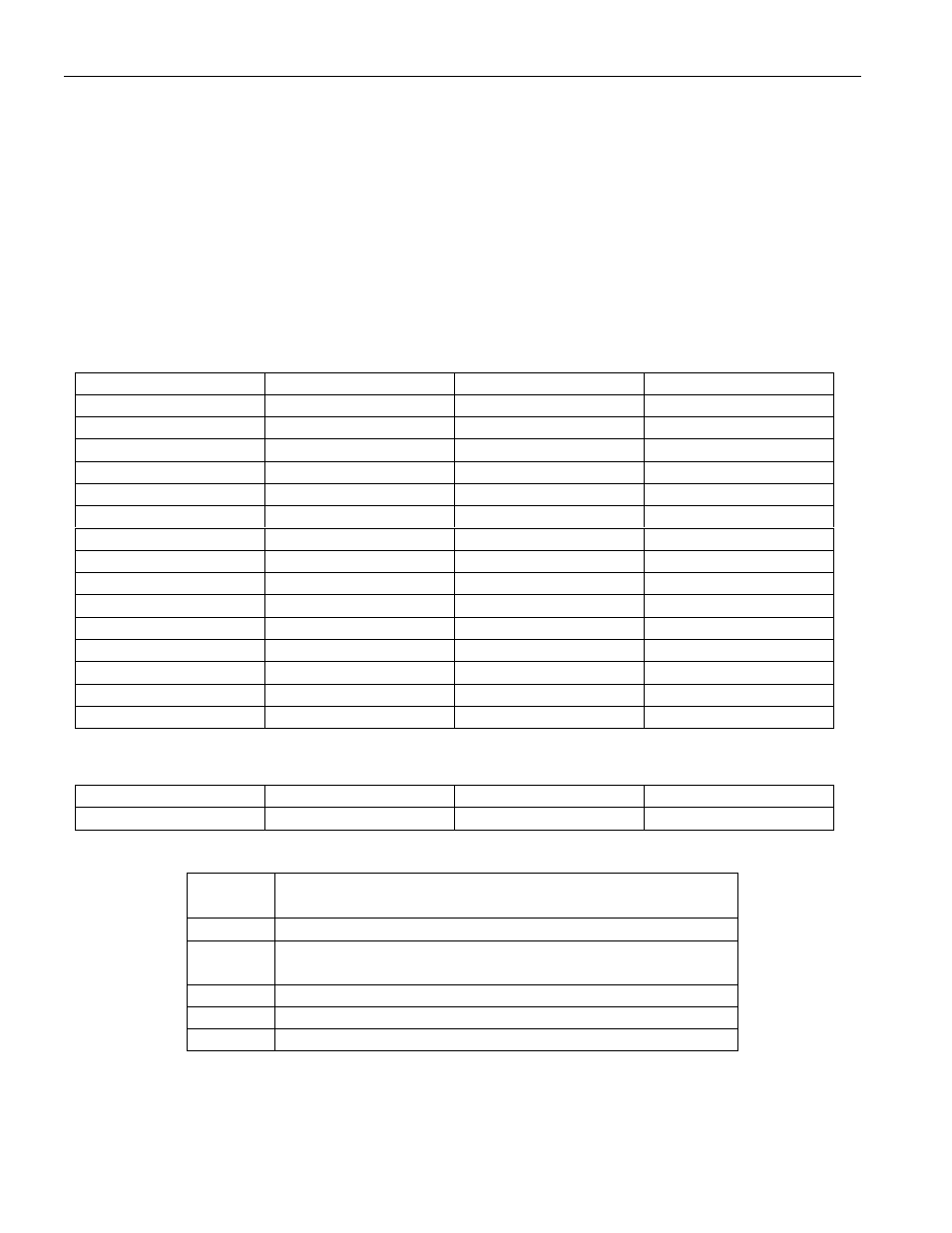
SHA-1 Input Data for Compute Next Secret Command Table 1
M0[31:24] = (SS+0)
M0[23:16] = (SS+1)
M0[15:8] = (SS+2)
M0[7:0] = (SS+3)
M1[31:24] = (PP+0)
M1[23:16] = (PP+1)
M1[15:8] = (PP+2)
M1[7:0] = (PP+3)
M2[31:24] = (PP+4)
M2[23:16] = (PP+5)
M2[15:8] = (PP+6)
M2[7:0] = (PP+7)
M3[31:24] = (PP+8)
M3[23:16] = (PP+9)
M3[15:8] = (PP+10)
M3[7:0] = (PP+11)
M4[31:24] = (PP+12)
M4[23:16] = (PP+13)
M4[15:8] = (PP+14)
M4[7:0] = (PP+15)
M5[31:24] = (PP+16)
M5[23:16] = (PP+17)
M5[15:8] = (PP+18)
M5[7:0] = (PP+19)
M6[31:24] = (PP+20)
M6[23:16] = (PP+21)
M6[15:8] = (PP+22)
M6[7:0] = (PP+23)
M7[31:24] = (PP+24)
M7[23:16] = (PP+25)
M7[15:8] = (PP+26)
M7[7:0] = (PP+27)
M8[31:24] = (PP+28)
M8[23:16] = (PP+29)
M8[15:8] = (PP+30)
M8[7:0] = (PP+31)
M9[31:24] = FFh
M9[23:16] = FFh
M9[15:8] = FFh
M9[7:0] = FFh
M10[31:24] = MPX
M10[23:16] = (SP+1)
M10[15:8] = (SP+2)
M10[7:0] = (SP+3)
M11[31:24] = (SP+4)
M11[23:16] = (SP+5)
M11[15:8] = (SP+6)
M11[7:0] = (SP+7)
M12[31:24] = (SS+4)
M12[23:16] = (SS+5)
M12[15:8] = (SS+6)
M12[7:0] = (SS+7)
M13[31:24] = FFh
M13[23:16] = FFh
M13[15:8] = FFh
M13[7:0] = 80h
M14[31:24] = 00h
M14[23:16] = 00h
M14[15:8] = 00h
M14[7:0] = 00h
M15[31:24] = 00h
M15[23:16] = 00h
M15[15:8] = 01h
M15[7:0] = B8h
Result of Compute Next Secret
(SS+0) := E[7:0]
(SS+1) := E[15:8]
(SS+2) := E[23:16]
(SS+3) := E[31:24]
(SS+4) := D[7:0]
(SS+5) := D[15:8]
(SS+6) := D[23:16]
(SS+7) := D[31:24]
Legend
Mt
Input buffer of SHA engine
0
≤
t
≤
15; 32-bit words
SS
Starting address of secret (80h)
PP
Starting address of memory page
See Memory Map, memory pages 0 through 3
(SP+n)
Byte n of scratchpad
MPX
MPX[7] = 0; MPX[6] = 0; MPX[5:0] = (SP+0)[5:0]
D, E
32-bit words, portions of the 160-bit SHA result
After issuing the Compute Next Secret command the master must provide a 2-byte target address to select
the memory page that contributes 256 bits of the SHA input data. The lower five bits of the target address
TA1 are not relevant. If the target address is valid, i. e. is in the range of 0000h to 007Fh, and the secret is
