Landmark Lighting D20R2-06/99 User Manual
Page 54
DESCRIPTION
Displays the 1- to 30-character description of the function. You
cannot change this field.
FUNCTION
Displays the 1- to 8-character name of the facility within the
product. You cannot change this field.
LO-ACCESS LEVELS-HI
Displays the level of access assigned this profile for each secured
function. Enter X under the access level appropriate for the
function and the profile. Access levels vary in meaning depending
on the function. Review the function access level table, later in this
chapter, to identify the minimum access level required for a specific
function and a description of the other access levels for that
function (if more than one access level applies). The following
table describes the five access levels, in order of increasing security
level.
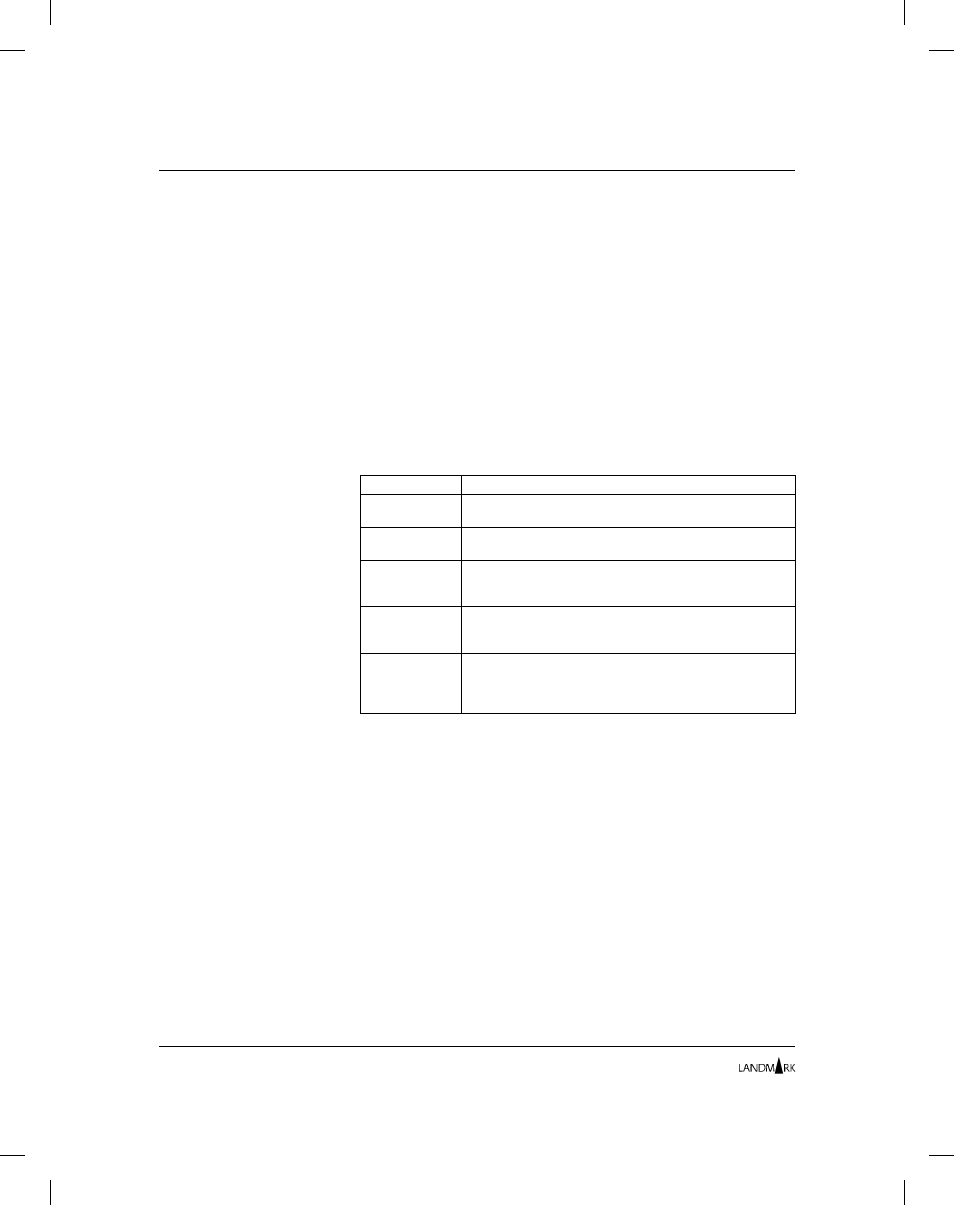
Access Level
Description
NONE
The lowest security access level. An X (the default) in this
field denies the user access to the function.
READ
Defines READ access authorization. This is the fourth
highest level of secured access.
UPDT
Defines UPDATE access authorization. This is the third
highest level of secured access. Users with UPDT access
also have READ access to the function.
CNTL
Defines CONTROL access authorization. This is the
second highest level of secured access. Users with CNTL
access also have READ and UPDT access to the function.
ALTR
Defines ALTER access authorization. This is the highest
level of secured access. Users with ALTR access have
total access, including READ, UPDT, and CNTL access to
the function.
PRIMARY RESOURCE
Shows the name of the principal resource for this profile definition.
User IDs using this profile definition are in effect only for the
resource specified here.
•
TMON for CICS primary resources are job names.
•
TMON for DB2 primary resources are DB2 subsystem names.
•
TMON for DBCTL primary resources are DBCTL subsystem
names.
•
TMON for MQSeries primary resources are MQSeries object
names.
•
TMON for MVS primary resources are job names or volume
serial numbers.
You can use an asterisk (*) to activate pattern matching for this
field. For example, PROD* identifies all primary resources
Detail Profile Definition
Chapter 2: Security Definitions
2-38
