Landmark Lighting D20R2-06/99 User Manual
Page 50
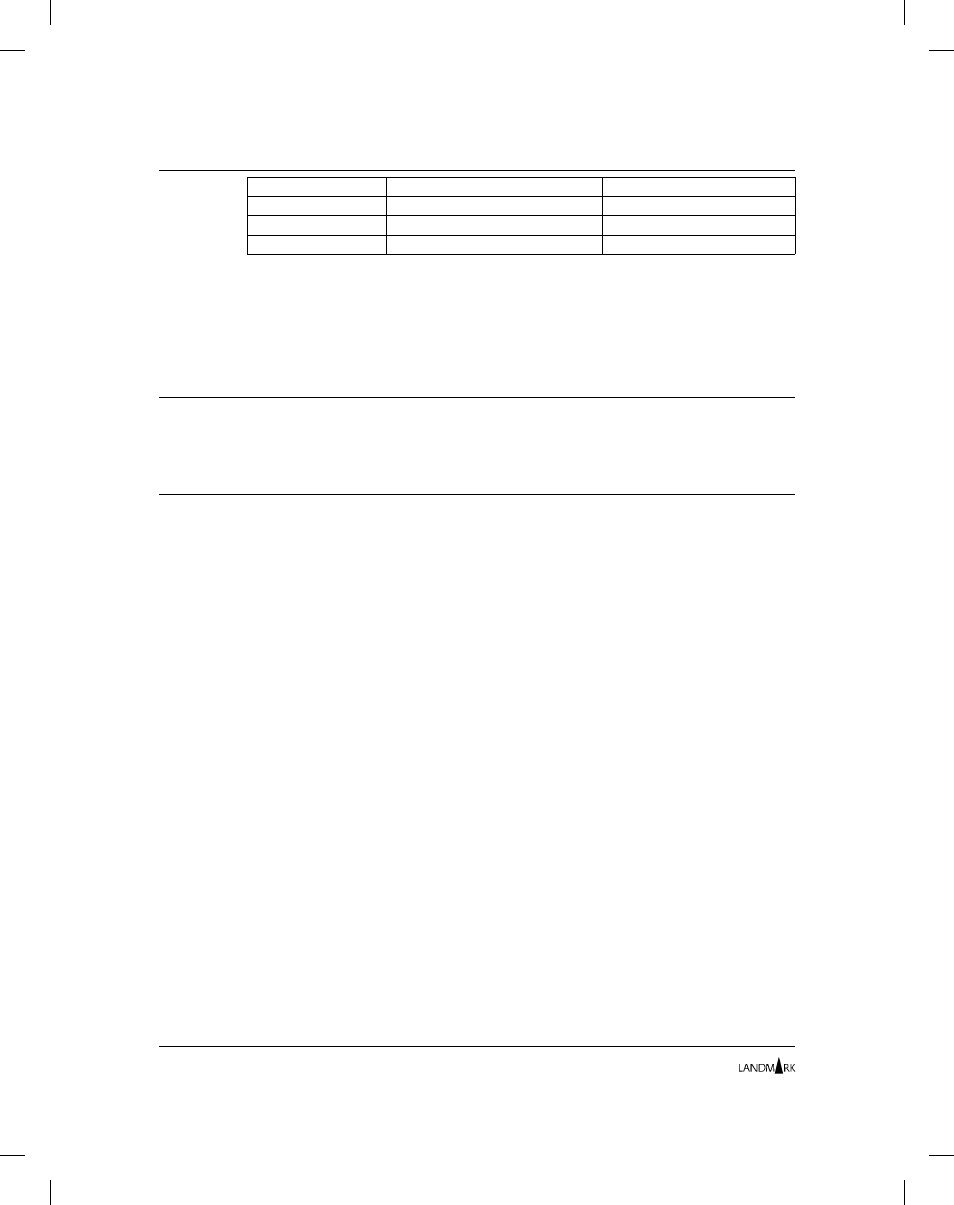
Product
Action
Displays
TMON for DBCTL
On the command line, enter
=M.1.3
.
Profiles/Resources Directory
TMON for MQSeries
On the command line, enter
=8.1.3
.
Profiles/Resources Directory
TMON for MVS
On the command line, enter
=S.2.3
.
Profiles/Resources Directory
If you access the Profile/Resources Directory screen as the third
option of the Security Definitions Menu, it displays resource
information for all existing security profile definitions in the
control file. If you access the screen from the User Definition or
User Profiles Directory screen, it displays only the resources for the
specific profile you selected.
Primary Commands
Use the DOWN and UP commands to scroll through this screen. To
learn about the various ways to scroll using these commands and
for syntax and descriptions of all commands, see Chapter 2 in your
product reference manual.
Fields
PRIMARY RESOURCE
Shows the name of the principal resource for the profile definition.
In addition to checking a user ID’s access level for a given function,
Landmark PerformanceWorks MVS products can limit a user ID’s
use of a function to a selected resource.
•
TMON for CICS primary resources are job names.
•
TMON for DB2 primary resources are DB2 subsystem names.
•
TMON for DBCTL primary resources are DBCTL subsystem
names.
•
TMON for MQSeries primary resources are MQSeries object
names.
•
TMON for MVS primary resources are job names or volume
serial numbers.
An asterisk (*) in the field shows that pattern matching is being
used. For example, PROD* identifies all primary resources
beginning with the letters “PROD.” If you specify an asterisk
alone, all values of the primary resource are used.
➥
PROFILE ID
Displays the 1- to 8-character profile ID for the product.
Cursor-select this field to add, update, or delete profile definitions.
The Detail Profile Definition screen is displayed.
SECONDARY RESOURCE
Shows the name of the secondary resource for the profile definition.
Profiles/Resources Directory
Chapter 2: Security Definitions
2-34
