Asante Technologies 35516 User Manual
Page 68
- 68 -
deny statement would follow the last entry, if no match was found before the end of the list. In this case, however, we
are permitting any other IP address other than 192.168.123.254, and a deny statement isn’t necessary.
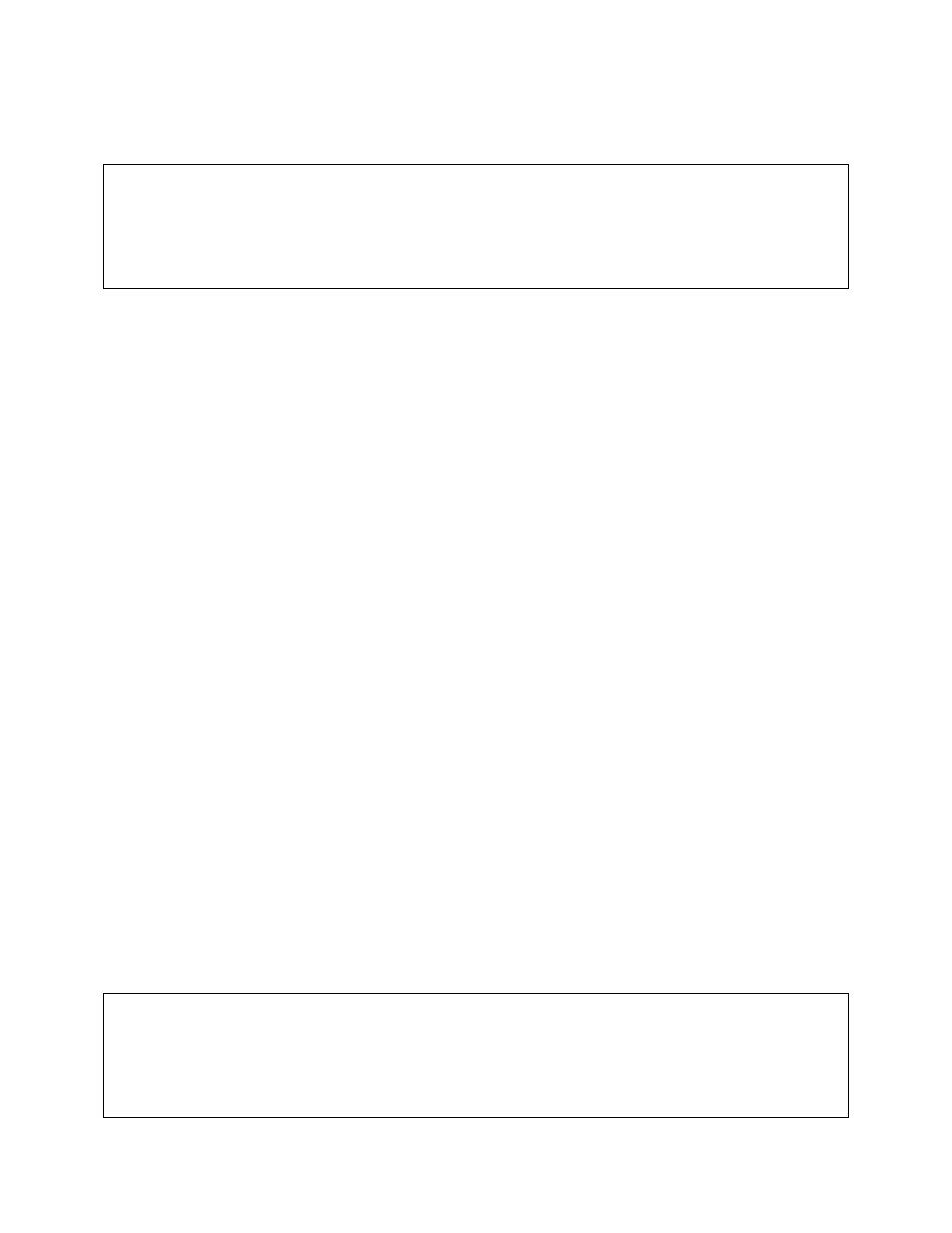
Router(config)# access-list 1 deny 192.168.123.254 ?
A.B.C.D Source wildcard. e.g. 0.0.0.255
Router(config)# access-list 1 deny 192.168.123.254
Router(config)# access-list 1 permit any {0.0.0.0 255.255.255.255}
Router(config)# exit
Router# show access-list
After entering the access list, use the show command from privileged mode, as shown above. Any lists you’ve
created, as well as any remark entered for a list, will be displayed.
Note: In the above examples, the argument any can be used instead of 0.0.0.0 255.255.255.255.
5.6.2 Create an Expanded Access List
Extended access lists filter at Layer 4, and can check source and destination addresses as well as filter transport
layer information, such as TCP and UDP protocols. In addition to the standard access list parameters listed above, an
extended access list also uses the following information:
•
Access list number (100–199): Identifies the access list to which an entry belongs
•
IP/ICMP/TCP/UDP: Specifies protocol connection
•
Destination address: Specifies the destination address to match
•
Operator operand: Select eq (equal to), gt (greater than), lt (less than), or neq (not equal to) to specify how to
match the protocol port number
•
0-65535: Specifies the protocol port number. Well-known ports are listed below:
20
File Transfer Protocol (FTP) data
21 FTP
Program
23 Telnet
25
Simple Mail Transfer Protocol (SMTP)
69
Trivial File Transfer Protocol (TFTP)
53
Domain Name System (DNS)
80
Hypertext Transport Protocol (HTTP)
110
Post Office Protocol (POP3)
119
Network News Transport Protocol (NNTP)
In the following example, an extended access list will be created to deny FTP and allow all other traffic from subnet
192.168.123.0 to be forwarded to all other networks or subnets.
Note: Remember when the cursor reaches the right margin, the command line shifts 8 spaces to the left. You cannot
see the first eight characters of the line, but you can scroll back and check the syntax at the beginning of the
command, using Ctrl-B or the left arrow keys.
Router# configure terminal
Router(config)# access-list 101 ?
remark Access list entry comment
deny Specify packets to reject
permit Specify packets to forward
Router(config)# access-list 101 deny ?
ip Specify IP connections
