Zoom 4420-A User Manual
Page 53
Chapter 6. Firewall Settings
53
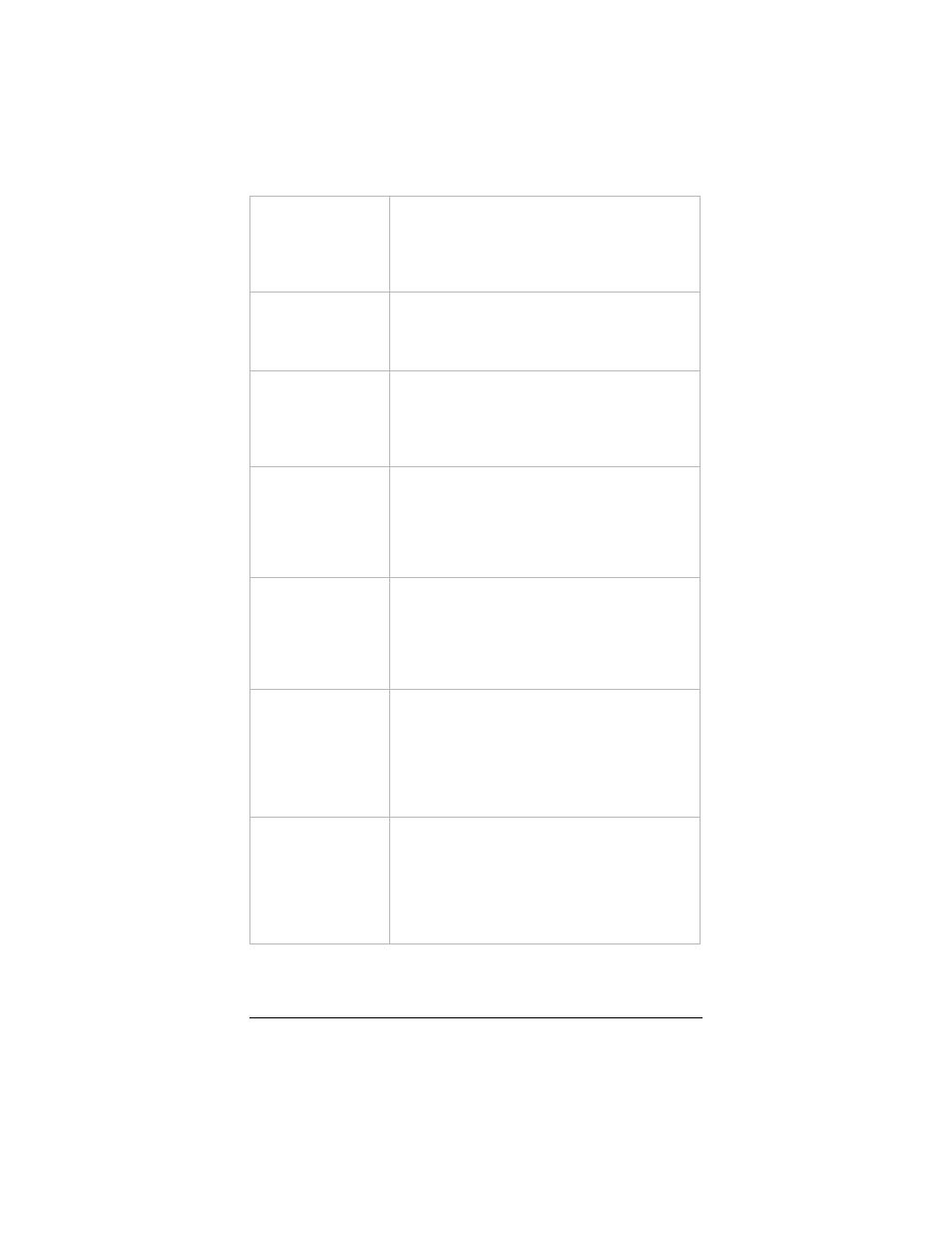
Whole System
Flood: FIN
This DoS attack involves large numbers of FIN
(Finish) packets, which terminate the
connection between the sender and recipient.
Select the check box and enter the number of
FIN Packets/Second that will be accepted.
Whole System
Flood: UDP
This type of attack sends a large amount of
traffic to ports 7 and 19 on LAN clients.
Select the check box and enter the number of
UDP Packets/Second that will be accepted.
Whole System
Flood: ICMP
This type of attack involves large numbers of
ICMP (Internet Control Message Protocol)
requests, such as ping or netmask, etc.
Select the check box and enter the number of
ICMP Packets/Second that will be accepted.
Per Source IP
Flood: SYN
This type of attack involves large numbers of
SYN packets with the source address spoofed
(faked) to appear to be the address of a LAN
client.
Select the check box and enter the number of
SYN Packets/Second that will be accepted.
Per Source IP
Flood: FIN
This type of attack involves large numbers of
FIN (Finish) packets, with the source address
spoofed to appear to be the address of a LAN
client.
Select the check box and enter the number of
FIN Packets/Second that will be accepted.
Per Source IP
Flood: UDP
This type of attack involves a large amount of
traffic directed to ports 7 and 19 on LAN
clients. In these messages the source address
is spoofed to appear to be the address of a
LAN client.
Select the check box and enter the number of
UDP Packets/Second that will be accepted.
Per Source IP
Flood: ICMP
This type of attack involves large numbers of
ICMP (Internet Control Message Protocol)
requests, such as ping or netmask, etc., with
the source address spoofed to appear to be
the address of a LAN client.
Select the check box and enter the number of
ICMP Packets/Second that will be accepted.
