Icmp sweep anomalies – Fortinet Network Device IPS User Manual
Page 57
ICMP sweep attacks
The FortiGate IPS response to ICMP sweep attacks
FortiGate IPS User Guide Version 3.0 MR7
01-30007-0080-20080916
57
ICMP sweep anomalies
The FortiGate unit also detects ICMP sweeps that do not have a predefined
signature to block them. The FortiGate IPS monitors traffic to ensure that ICMP
messages do not exceed the default or user-defined threshold.
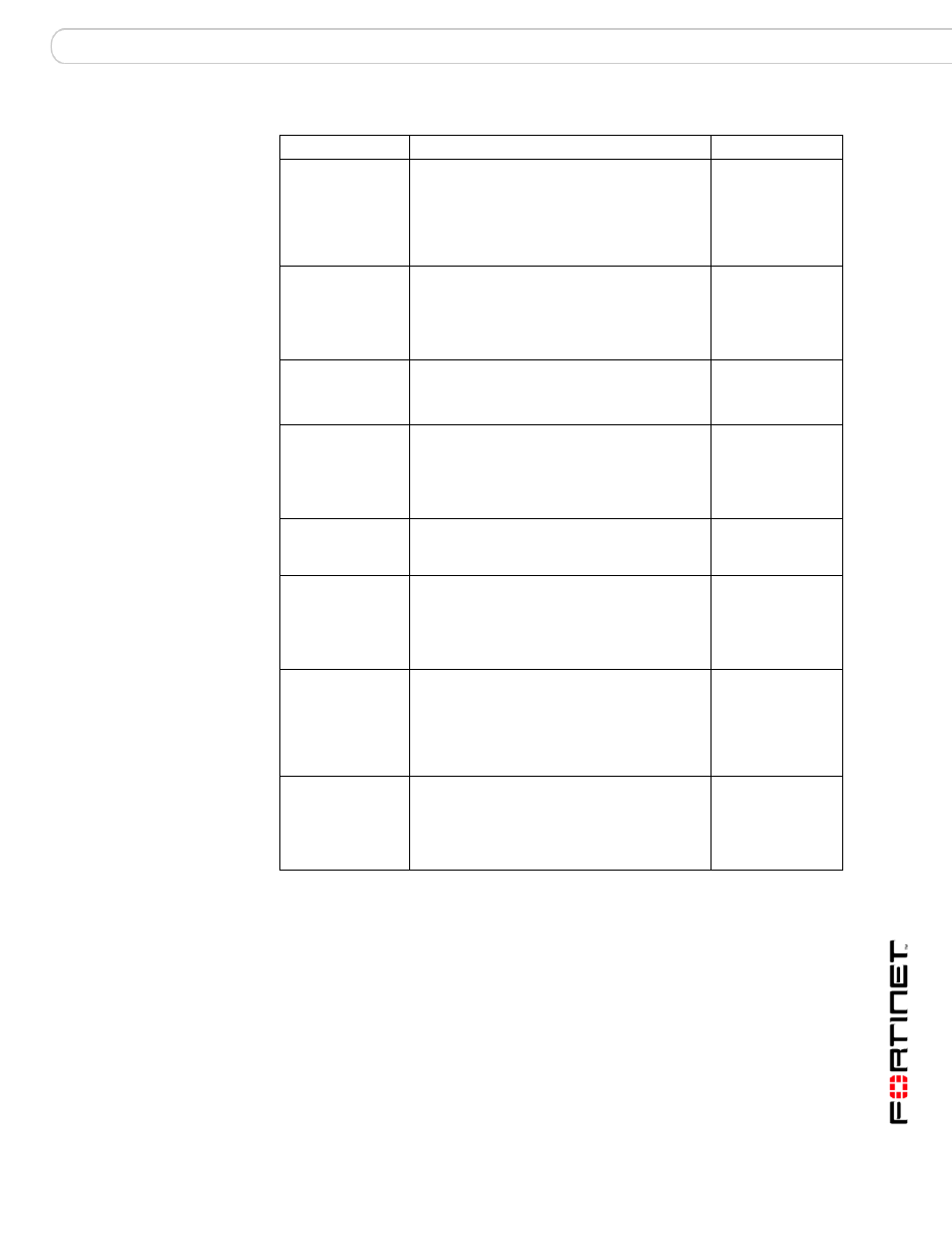
NMAP.Echo.
Request
NMAP is a free open source network
mapping/security tool that is available for most
operating systems. NMAP could be used
maliciously to perform an ICMP sweep. ICMP
echo request messages sent using this
software contain special characters that identify
NMAP as the source.
Signature disabled
Redirect.Code4.
Echo.Request
This signature detects ICMP type 5 code 4
redirect messages. An ICMP redirect message
describes an alternate route for traffic to take.
An attacker may use ICMP redirect messages
to alter the routing table or cause traffic to
follow an unintended route.
Signature enabled
Logging enabled
Action: Pass
Sniffer.Pro.
NetXRay.Echo.
Request
Sniffer Pro and NetXRay are scanning tools.
ICMP echo request messages sent using this
software contain special characters that identify
them as the source.
Signature enabled
Logging enabled
Action: Drop
Superscan.Echo.
Request
Superscan is a free network scanning tool for
Windows from Foundstone Inc. Superscan
could be used maliciously to perform an ICMP
sweep. ICMP echo request messages sent
using this software contain special characters
that identify Superscan as the source.
Signature enabled
Logging enabled
Action: Drop
TimeStamp.
Request
TimeStamp detects timestamp request
messages from a host pretending to be part of
the network.
Signature enabled
Logging enabled
Action: Pass
TJPingPro1.1.
Echo.Request
TJPingPro1.1 is a widely-used network tool for
older versions of Windows. TJPingPro could be
used maliciously to perform an ICMP sweep.
ICMP echo request messages sent using this
software contain special characters that identify
TJPingPro as the source.
Signature enabled
Logging enabled
Action: Drop
Traceroute.Traffic Traceroute is a very common network tool
available on almost any operating system. This
tool could be sued maliciously to perform an
ICMP sweep. ICMP echo request messages
sent using this software contain special
characters that identify traceroute as the
source.
Signature enabled
Logging enabled
Action: Pass
Whatsup.Echo.
Request
WhatsUp Gold is a network scanning tool for
Windows from IPswitch. WhatsUp could be
used maliciously to perform an ICMP sweep.
ICMP echo request messages sent using this
software contain special characters that identify
WhatsUpGold as the source.
Signature enabled
Logging enabled
Action: Drop
Table 11: Predefined ICMP sweep signatures
Signature
Description
Default settings
