Fortinet Network Device IPS User Manual
Page 53
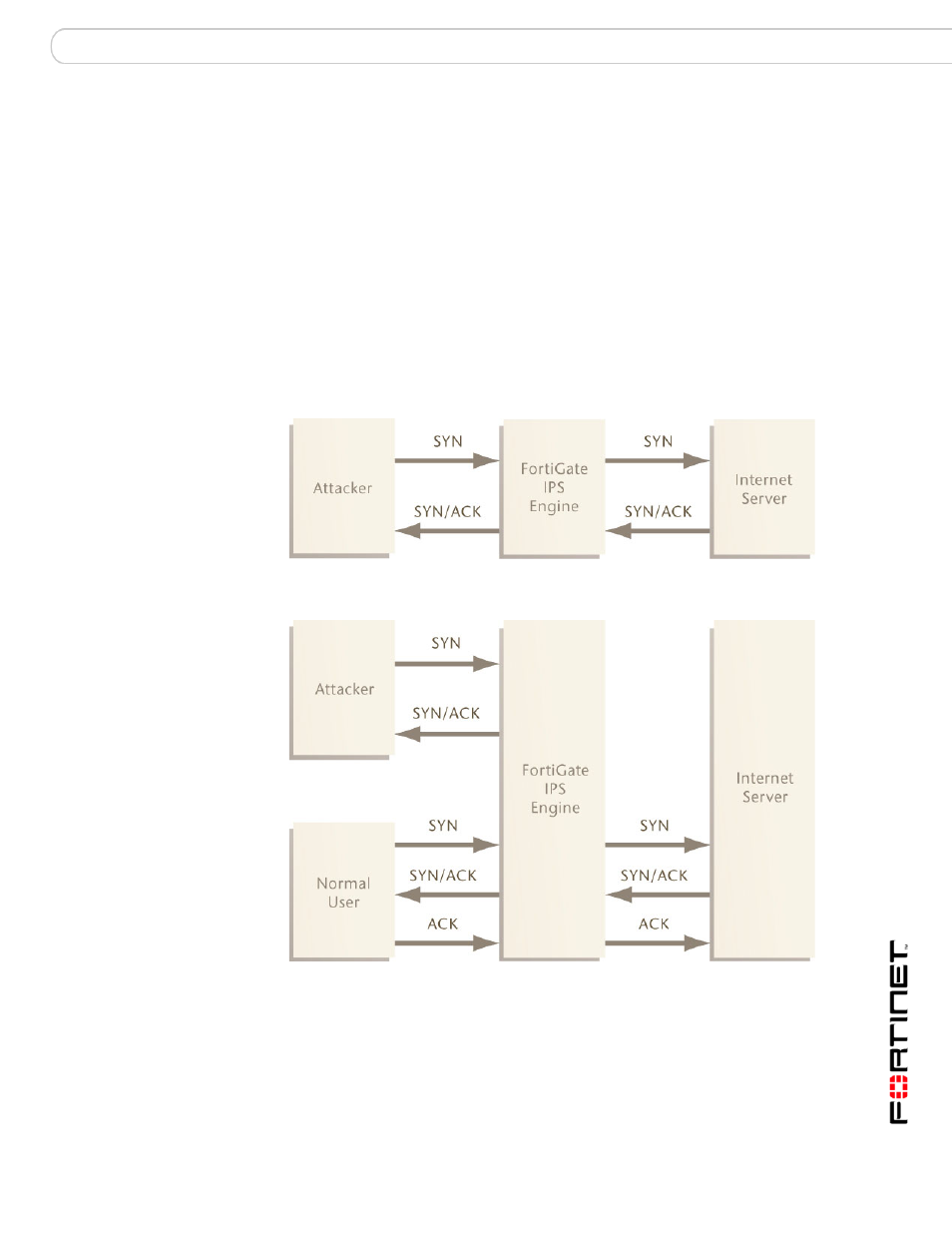
SYN flood attacks
The FortiGate IPS Response to SYN flood attacks
FortiGate IPS User Guide Version 3.0 MR7
01-30007-0080-20080916
53
A true SYN proxy approach requires that all three packets (SYN, SYN/ACK, and
ACK) are cached and replayed even before it is known if a TCP connection
request is legitimate. The FortiGate IPS pseudo SYN proxy retransmits every TCP
packet immediately from the packet source to the packet destination as soon as it
records the necessary information for SYN flood detection.
Since the pseudo SYN proxy in the IPS uses a “best effect” algorithm to determine
whether a TCP connection is legitimate or not, some legitimate connections may
be falsely detected as incomplete TCP connection requests and dropped.
However, the ratio of the pseudo SYN proxy dropping legitimate TCP connection
is quite small.
illustrates the operational behavior of the FortiGate IPS Engine before
the SYN Flood threshold is reached.
illustrates the operation behavior
of the FortiGate IPS Engine after the SYN Flood threshold is reached.
Figure 16: IPS operation before syn_flood threshold is reached
Figure 17: IPS operation after syn_flood threshold is reached
