D-Link DFL-600 User Manual
Page 86
tion.
the
ore more likely to be
IKE
encryption algorithm that will be used to
encrypt the messages passed between the VPN
tunnel endpoints during the Phase 1 negotia
You can choose between DES and 3DES
encryption methods. The key length for
3DES algorithm is three times as long as the
DES key, and is theref
secure. You must choose exactly the same
Encryption algorithm on both ends of a VPN
tunnel.
P
hase 2 Proposal
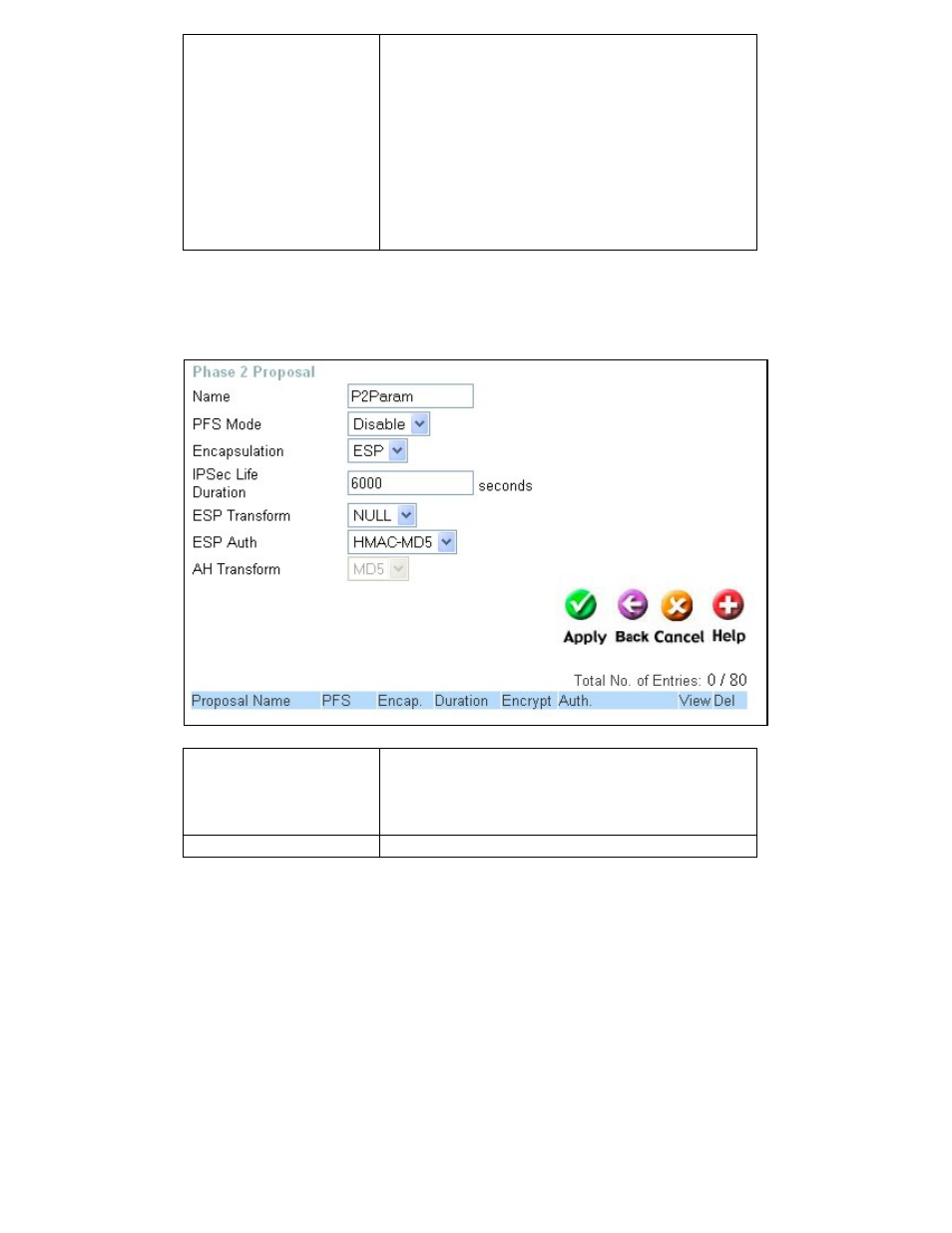
Phase 2 Proposal
The following entries will establish the setup
for the negotiation between the two endpoints
for the encryption of messages once the VPN
tunnel has been initiated.
PFS Mode
This drop-down menu allows you to specify the
See also other documents in the category D-Link Hardware:
- AirPlus G DWL-G120 (2 pages)
- AirPlus G DI-524 (92 pages)
- DI-304 (105 pages)
- DIR-455 (93 pages)
- DI-308 (131 pages)
- DIR-120 (77 pages)
- DIR-451 (3 pages)
- DI-704UP (108 pages)
- DFE-550TX (34 pages)
- DAS-4192-60 (55 pages)
- VDI-624 (91 pages)
- DI-714 (58 pages)
- Wireless ADSL2/2+ 4-port Ethernet Router DSL-2640U (84 pages)
- DCM-202 (7 pages)
- DCM-202 (39 pages)
- DI-514 (62 pages)
- DES-6509 (1 page)
- WIRELESSADSLROUTER DSL-G604T (92 pages)
- DIR-68 (98 pages)
- DFL-500 (122 pages)
- DFE-530TX+ (21 pages)
- DFE-530TX+ (27 pages)
- DFE-530TX+ (2 pages)
- DCM-201 (34 pages)
- DES-5024 (93 pages)
- DI-774 (98 pages)
- WBR-2310 (78 pages)
- DSL 2740B (15 pages)
- DSL 2740B (115 pages)
- DAP-1160 (59 pages)
- Wireless Network Storage Adapter DNS-G120 (2 pages)
- AirPlus DI-524 (95 pages)
- DI-1162M (140 pages)
- DGL3420 (2 pages)
- DRO-210i (78 pages)
- DI-604 (79 pages)
- DSL-500 (74 pages)
- DIR-301 (67 pages)
- WIRELES 108 ROUTER DI-724GU (89 pages)
- DIR-635 (86 pages)
- DFE-500FX (16 pages)
- BROADBAND DSL-30B (12 pages)
- DGL-4300 (74 pages)
- DAP-3220 (76 pages)
