Toshiba Satellite U200 User Manual
Page 72
4-4
User’s Manual
Operating Basics
Fingerprint Sensor Limitations.
■
The fingerprint sensor compares and analyzes the unique
characteristics in a fingerprint.
■
A warning message will be displayed when recognition is abnormal or
recognition is not successful within a fixed duration.
■
The recognition success rate may differ from user to user.
■
Toshiba does not guarantee that this fingerprint recognition technology
will be error-free.
■
Toshiba does not guarantee that the fingerprint sensor will recognize
the enrolled user or accurately screen out unauthorized users at all
times. Toshiba is not liable for any failure or damage that might arise out
of the use of this fingerprint recognition software or utility.
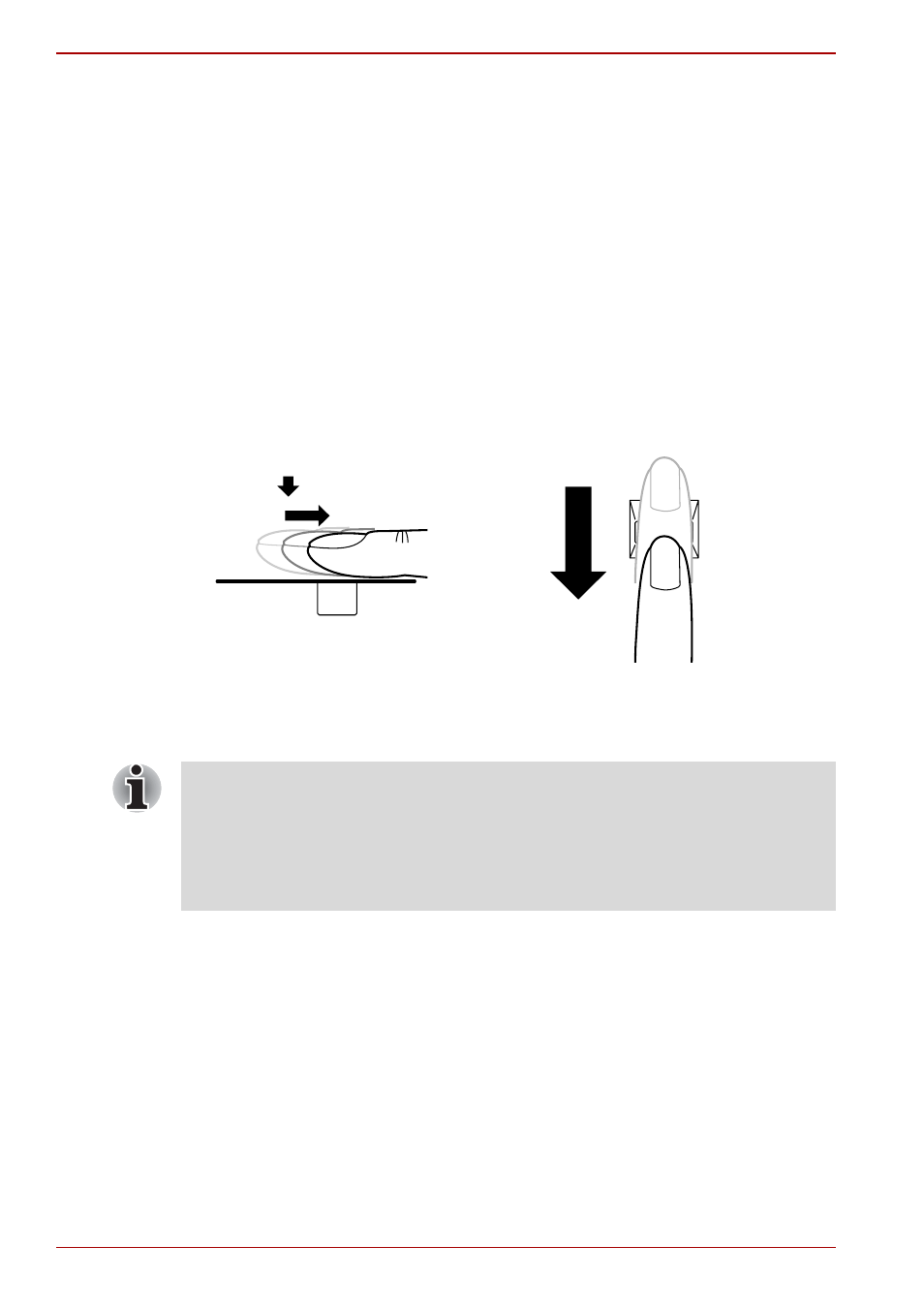
The following illustrations show the correct way to swipe your finger over
the recognition sensor.
Align your fingertip with the sensor as shown in the drawing and swipe.
Points to note about the Fingerprint Utility
If Windows XP’s file encryption function EFS (Encryption File System) is
used to encrypt a file, the file cannot be further encrypted using the
encryption function of this software.
If the fingerprint sensor and Trusted Platform Module (TPM) security are
used as identification devices, install and configure the Infineon TPM
Professional package first before configuring the Fingerprint Utility. Please
refer to the TPM (Trusted Platform Module) Installation Guide for the
installation and configuration methods for TPM.
In the help file, it is stated that this software’s PasswordBank function can
be used for the Internet and general applications. However, the Internet
PasswordBank function in the Fingerprint Utility provided in this computer
can only be used with IE (Internet Explorer).
Backups for saved fingerprint data and saved information in the
PasswordBank can be performed in Import or Export User Data under
Fingerprint Software Management. However, encrypted files cannot be
backuped within Mysafe with this function. Recommended action is
backing up encrypted files to external media with standard methods such
as copying files.
