Enforced fingerprint bypass option, Fingerprint swipe result, Command-line tools – Lenovo ThinkVantage (Client Security Solution 8.21) User Manual
Page 38
To leverage the PKCS #11 module of Client Security Solution, the following policies must be set for Active
Directory:
1. PKCS #11 Signature
2. PKCS #11 Decryption
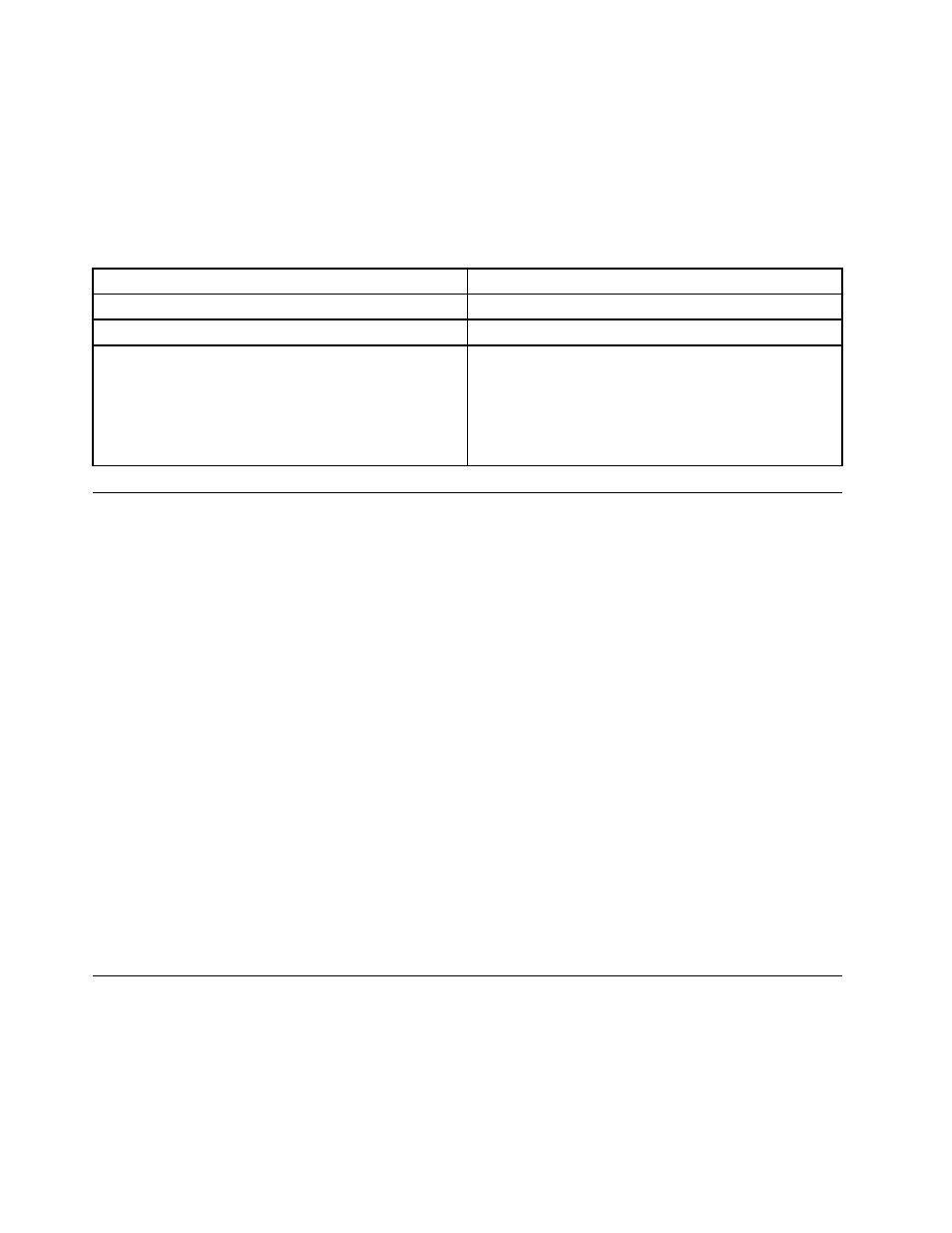
The following table provides the modifiable field and description of policies for PKCS# 11:
Table 10. ThinkVantage\Client Security Solution\Authentication Policies\PKCS# 11 Signature\Custom Mode
Fields
CSS.ADM
Modifiable field
Required
Field Description
Controls whether password or passphrase is required.
Possible values
• Enabled
– Every time
– Once per logon
• Disabled
• Not configured
Settings and policies for the fingerprint reader authentication
Enforced fingerprint bypass option
The fingerprint bypass option enables a user to bypass the fingerprint authentication and use a windows
password to log on. The user can select or deselect this option on the Password Manager user interface
when adding a new entry.
However, by default, the fingerprint bypass is enabled even if this option is not selected. This is to allow the
user to log on to Windows when the fingerprint sensor is not functional. To disable the enforced fingerprint
bypass option, edit the following registry key:
[HKEY_LOCAL_MACHINE\SOFTWARE\Lenovo\Client Security Solution\CSS Configuration]
"GinaDenyLogonDeviceNonEnrolled"=dword:00000001
When the registry key is set as above, the user can not bypass fingerprint authentication when the fingerprint
sensor is not working.
Fingerprint swipe result
During the fingerprint authentication, the below policy controls the display of fingerprint swipe results.
HKLM\Lenovo\TVT Common\Client Security Solution\FPSwipeResult
• FPSwipeResult=0: Show all messages.
• FPSwipeResult=1: Show failure messages only(default value).
• FPSwipeResult=2: Do not show any messages.
Command-line tools
ThinkVantage Technologies features can also be implemented locally or remotely by corporate IT
administrators through the command-line interface. Configuration settings can be maintained through
remote text file settings.
Client Security Solution has the following command-line tools:
32
Client Security Solution 8.21Deployment Guide
