Software emulation, User level key structure - enroll user, Background enrollment – Lenovo ThinkVantage (Client Security Solution 8.21) User Manual
Page 26
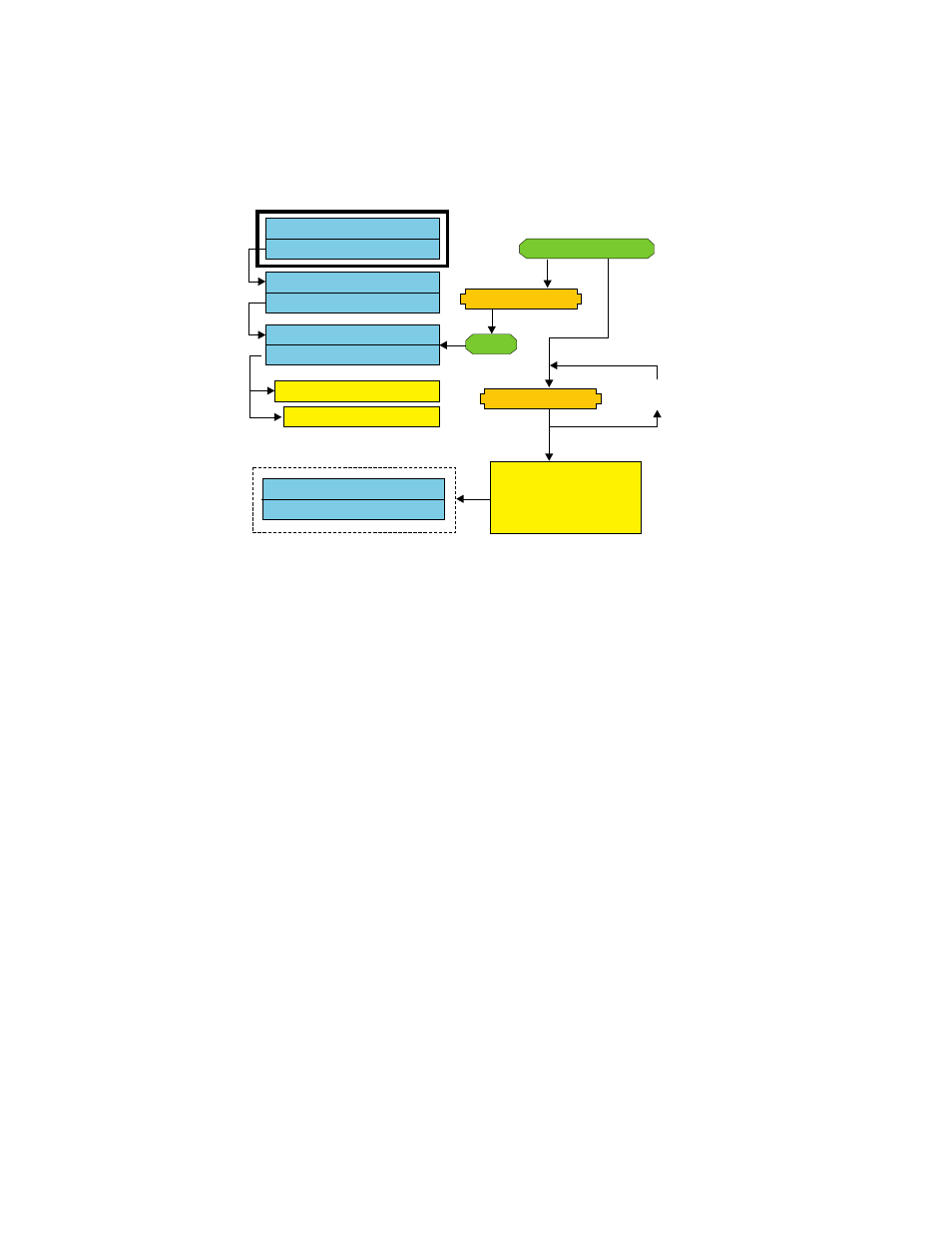
The following diagram provides the structure for the user level key:
User Level Key Structure - Enroll User
Trusted Platform Module
Encrypted via derived AES Key
Storage Root Private Key
Storage Root Public Key
User Leaf Private Key
User Base Private Key
User Leaf Public Key
User Base Public Key
Windows PW AES Key
PW Manager AES Key
User Base Private Key
User Base Public Key
If Passphrase
loop n times
User PW/PP
One-Way Hash
One-Way Hash
User Base AES
Protection Key
(derived via output
of hash algorithm)
Auth
Figure 2. User Level Key Structure - Enroll User
Background enrollment
Client Security Solution 8.21 supports background enrollment for user enrollment that is started
automatically. The enrollment process runs in the background without displaying any notifications.
Note: The background enrollment is only available for user enrollment that is started automatically. For user
enrollment that is started manually, from the start menu or from the Reset Security Settings, a dialog
indicating the user to wait for the user enrollment will still be displayed.
Local administrator or domain administrator can also force the waiting dialog to be displayed by editing
the following policy as below:
CSS_GUI_ALWAYS_SHOW_ENROLLMENT_PROCESSING
Or by editing the following registry key as below:
HKLM\software\policies\lenovo\client security solution\GUI options\
AlwaysShowEnrollmentProcessing
The default value of AlwaysShowEnrollmentProcessing is 0. When the above registry key is set to 0, the
waiting dialog is not displayed for user enrollment started automatically. When this policy is set to 1, the
waiting dialog will always be displayed during user enrollment regardless of how the enrollment is started.
Software emulation
To provide a consistent experience for the user whose computer does not have a TPM, CSS supports the
TPM emulation mode.
The TPM emulation mode is a software-based root of trust. The same functionalities provided by the
TPM, including digital signature, symmetric key decryption, RSA key import, protection, and random
number generation, are available to the user, except there is decreased security because the root of trust is
software based keys.
20
Client Security Solution 8.21Deployment Guide
