Chapter 4: icas configuration, Configure proxy servers, Access logs – HP Remote Device Access Software User Manual
Page 13
Chapter 4: iCAS Configuration
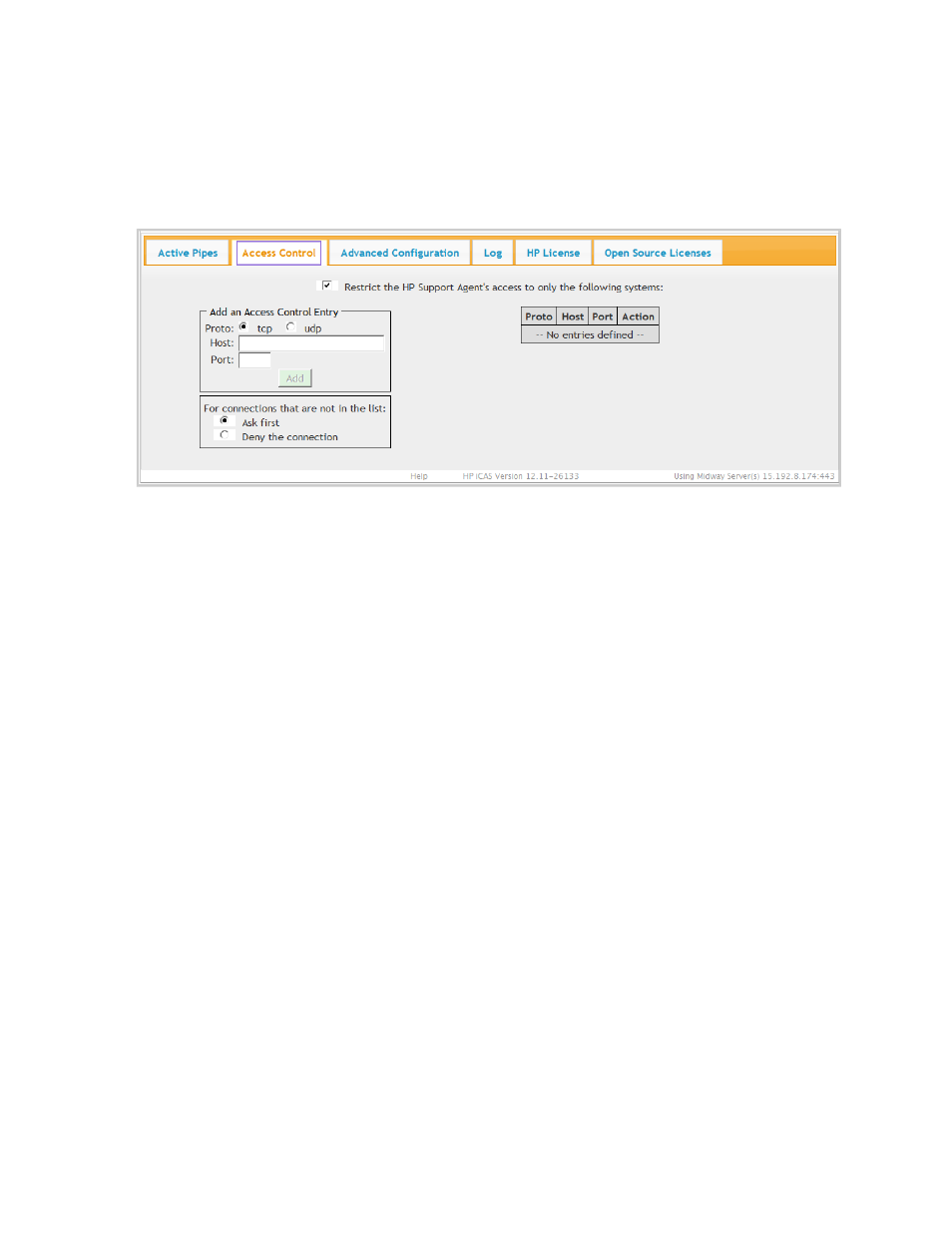
The customer can restrict and control HP's use of iCAS to only designated systems to meet security
needs by clicking the Access Control tab.
Figure 4.1 Access Control Tab
Configure Proxy Servers
We use the HTTP Connect method to jump through the proxy server, requesting port 80. Many proxy
servers are configured by default to forbid a CONNECT to port 80. The iCAS will return a "403 Forbidden"
error from the proxy. Change the proxy configuration to allow this CONNECT to port 80. For example, in
the Squid proxy, add port 80 to the Safe_ports ACL. In tinyproxy, add "ConnectPort 80" to the
configuration.
Access Logs
Customers can monitor HP's use of iCAS to see which systems HP accesses. Logs can also be used to
troubleshoot iCAS connection problems. Click the Log tab to view log records and events.
Page 13 of 15
HP Remote Device Access 8.1: iCAS User Guide
- Scripting Toolkit for Linux (68 pages)
- Scripting Toolkit for Windows 9.50 (62 pages)
- Scripting Toolkit for Windows 9.60 (62 pages)
- Storage Area Manager (13 pages)
- Core HP-UX (5 pages)
- Matrix Operating Environment Software (34 pages)
- Matrix Operating Environment Software (63 pages)
- Matrix Operating Environment Software (67 pages)
- Matrix Operating Environment Software (128 pages)
- Matrix Operating Environment Software (104 pages)
- Matrix Operating Environment Software (75 pages)
- Matrix Operating Environment Software (245 pages)
- Matrix Operating Environment Software (209 pages)
- Matrix Operating Environment Software (71 pages)
- Matrix Operating Environment Software (239 pages)
- Matrix Operating Environment Software (107 pages)
- Matrix Operating Environment Software (77 pages)
- Insight Management-Software (148 pages)
- Matrix Operating Environment Software (80 pages)
- Insight Management-Software (128 pages)
- Matrix Operating Environment Software (74 pages)
- Matrix Operating Environment Software (132 pages)
- Matrix Operating Environment Software (76 pages)
- Matrix Operating Environment Software (233 pages)
- Matrix Operating Environment Software (61 pages)
- Matrix Operating Environment Software (232 pages)
- Matrix Operating Environment Software (120 pages)
- Matrix Operating Environment Software (70 pages)
- Matrix Operating Environment Software (36 pages)
- Matrix Operating Environment Software (99 pages)
- Matrix Operating Environment Software (192 pages)
- Matrix Operating Environment Software (198 pages)
- Matrix Operating Environment Software (66 pages)
- Matrix Operating Environment Software (152 pages)
- Matrix Operating Environment Software (95 pages)
- Matrix Operating Environment Software (264 pages)
- Matrix Operating Environment Software (138 pages)
- Matrix Operating Environment Software (137 pages)
- Matrix Operating Environment Software (97 pages)
- Matrix Operating Environment Software (33 pages)
- Matrix Operating Environment Software (189 pages)
- Matrix Operating Environment Software (142 pages)
- Matrix Operating Environment Software (58 pages)
- Matrix Operating Environment Software (68 pages)
- Matrix Operating Environment Software (79 pages)
