HP FIPS 140-2 User Manual
Page 7
Security Policy, version 1.0
January 31, 2008
HP StorageWorks Secure Key Manager
Page 7 of 26
© 2008 Hewlett-Packard Company
This document may be freely reproduced in its original entirety.
Section
Section Title
Level
10 Design
Assurance
2
11
Mitigation of Other Attacks
N/A
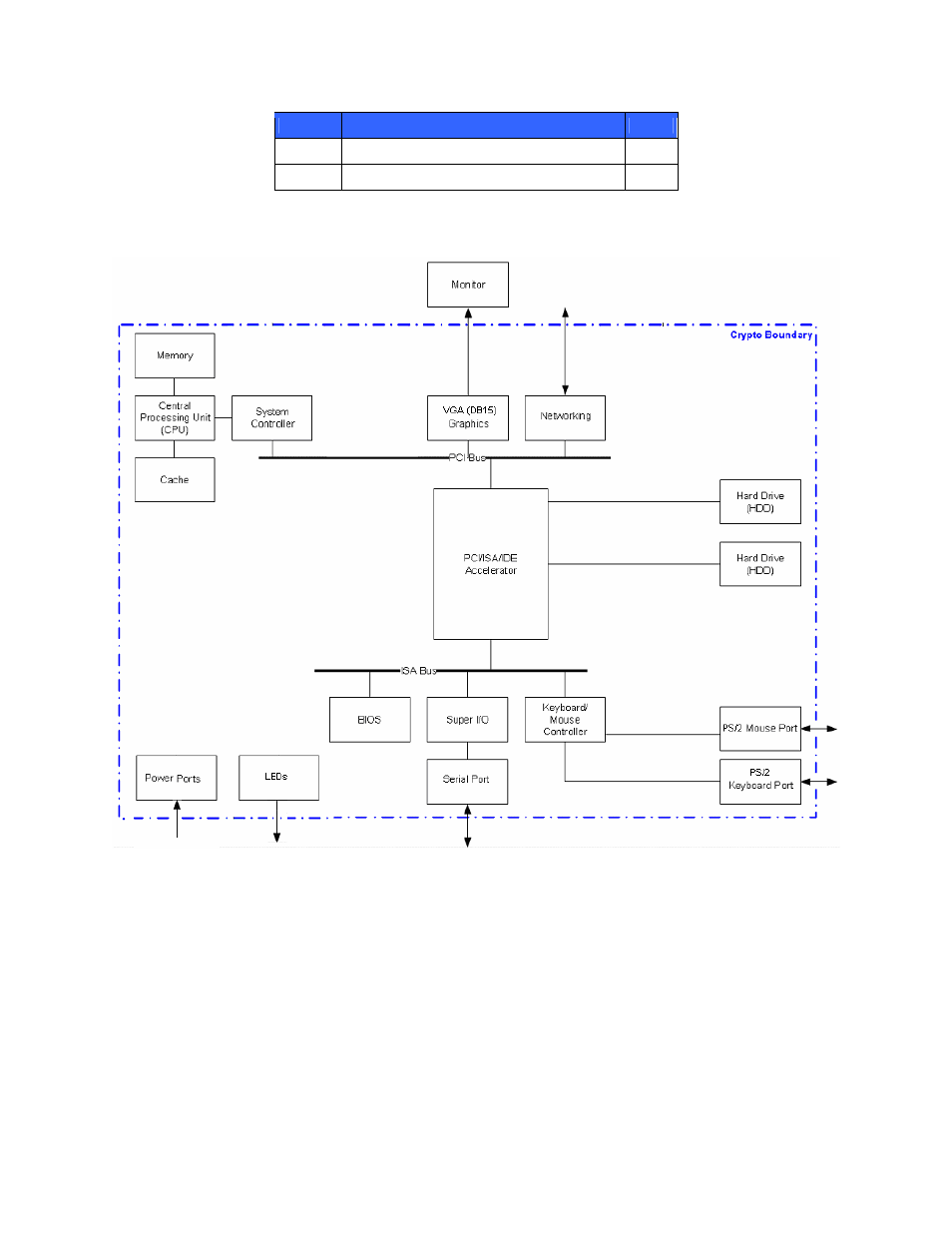
The block diagram of the module is given in Figure 2 – Block Diagram of SKM. The cryptographic boundary is
clearly shown in the figure.
Figure 2 – Block Diagram of SKM
In the FIPS mode of operation, the module implements the following Approved algorithms:
• Advanced Encryption Standard (AES) encryption and decryption: 128, 192, and 256 bits, in Electronic
Codebook (ECB) and Cipher Block Chaining (CBC) modes (certificate # 653)
• Triple Data Encryption Standard (3DES) encryption and decryption: 112 and 168 bits, in ECB and CBC
modes (certificate # 604)
• Secure Hash Algorithm (SHA)-1, SHA-256, SHA-384, SHA-512 (certificate # 847)
• Keyed-Hash Message Authentication Code (HMAC) SHA-1 and HMAC SHA-256 (certificate # 470)
• Rivest, Shamir, and Adleman (RSA) American National Standard Institute (ANSI) X9.31 key generation,
signature generation, and signature verification: 1024 and 2048 bits (certificate # 302)
