3 physical security assurance – HP FIPS 140-2 User Manual
Page 22
Security Policy, version 1.0
January 31, 2008
HP StorageWorks Secure Key Manager
Page 22 of 26
© 2008 Hewlett-Packard Company
This document may be freely reproduced in its original entirety.
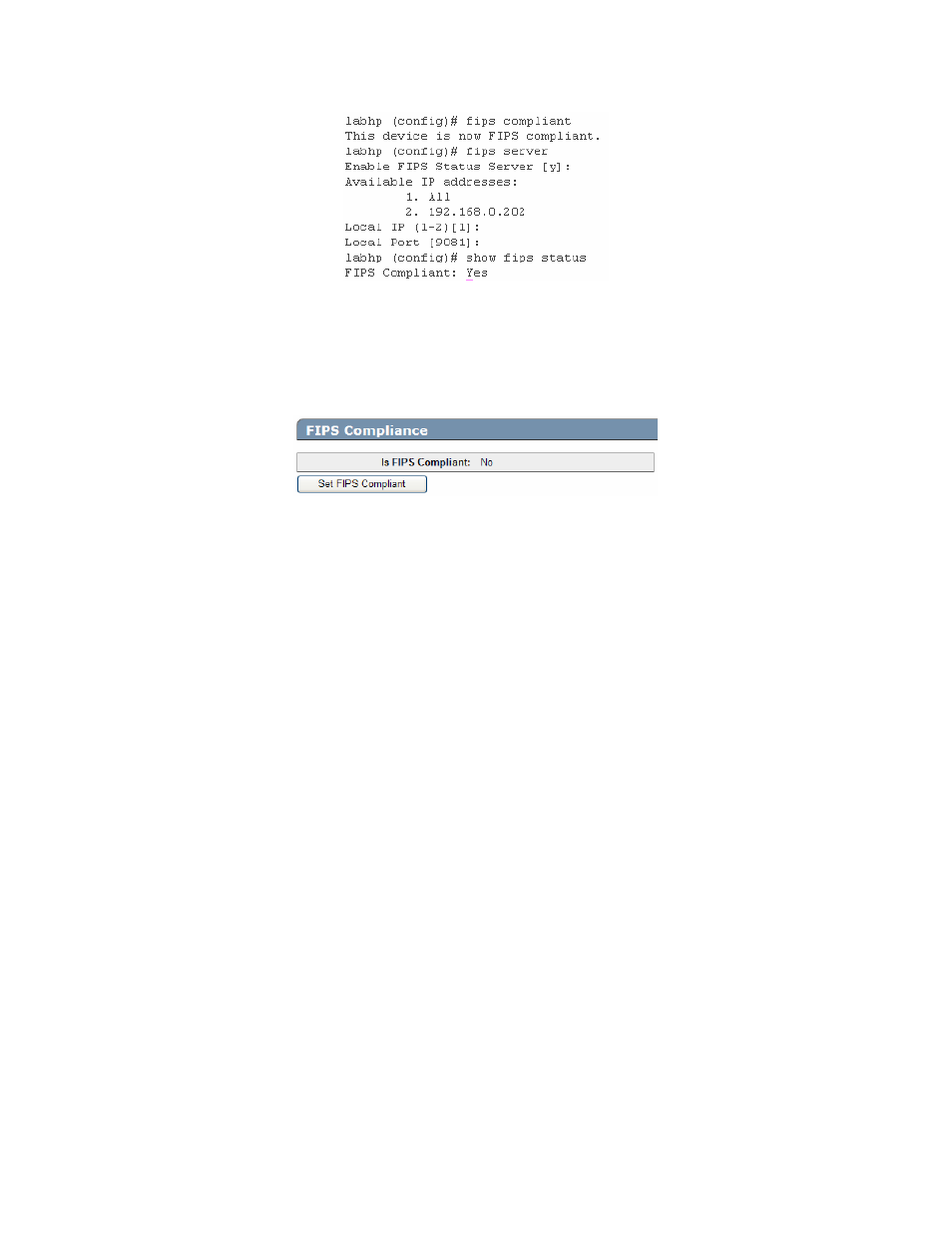
Figure 6 – FIPS Compliance in CLI
In the web administration interface, the Crypto Officer should use the “High Security Configuration” page to enable
and disable FIPS compliance. To enable the Approved FIPS mode of operation, click on the “Set FIPS Compliant”
button. See Figure 7 – FIPS Compliance in Web Administration Interface. This will alter various server settings as
described above.
Figure 7 – FIPS Compliance in Web Administration Interface
In the web administration interface, the User can review the FIPS mode configuration by reading the “High Security
Configuration” page.
The Crypto Officer must zeroize all keys when switching from the Approved FIPS mode of operation to the non-
FIPS mode and vice versa.
3.3 Physical Security Assurance
Serialized tamper-evidence labels have been applied at four locations on the metal casing. See Figure 8 – Tamper-
Evidence Labels. The tamper-evidence labels have a special adhesive backing to adhere to the module’s surface.
The tamper-evidence labels have individual, unique serial numbers. They should be inspected periodically and
compared to the previously-recorded serial numbers to verify that fresh labels have not been applied to a tampered
module.
