HP FIPS 140-2 User Manual
Page 18
Security Policy, version 1.0
January 31, 2008
HP StorageWorks Secure Key Manager
Page 18 of 26
© 2008 Hewlett-Packard Company
This document may be freely reproduced in its original entirety.
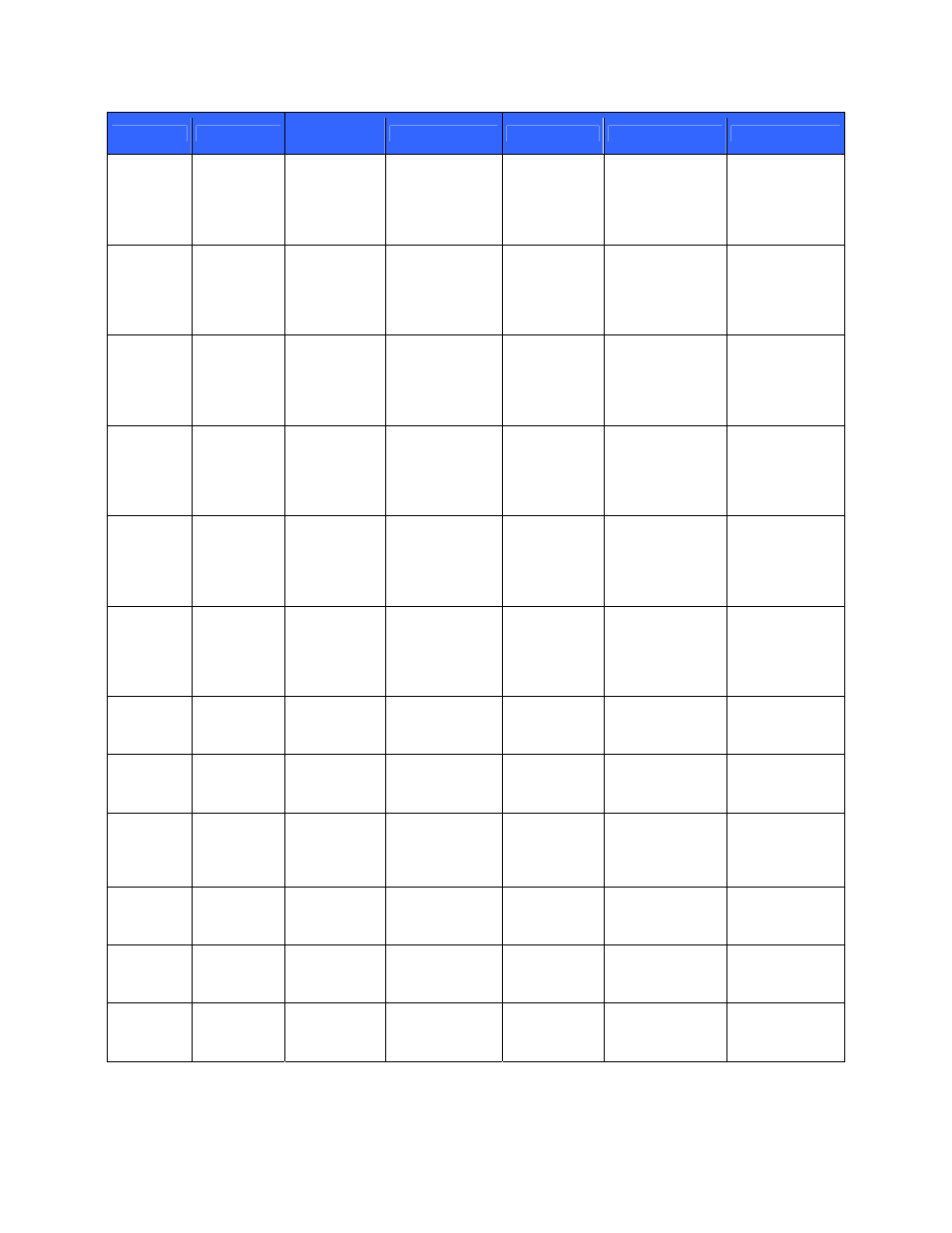
Key
Key Type
Generation /
Input
Output
Storage
Zeroization
Use
Client AES
key
128, 192 or
256-bit AES
key
Generated by
ANSI X9.31
DRNG
Via TLS in
encrypted form
(encrypted with
TLS Ks) per
client’s request
Encrypted in
non-volatile
memory
Per client’s
request or zeroize
request
Encrypt
plaintexts/decrypt
ciphertexts
Client
3DES key
3DES key
Generated by
ANSI X9.31
DRNG
Via TLS in
encrypted form
(encrypted with
TLS Ks) per
client’s request
Encrypted in
non-volatile
memory
Per client’s
request or zeroize
request
Encrypt
plaintexts/decrypt
ciphertexts
Client RSA
public keys
RSA public
key
Generated by
ANSI X9.31
DRNG
Via TLS in
encrypted form
(encrypted with
TLS Ks) per
client’s request
Encrypted in
non-volatile
memory
At operator delete Sign
messages/verify
signatures
Client RSA
keys
RSA private
keys
Generated by
ANSI X9.31
DRNG
Via TLS in
encrypted form
(encrypted with
TLS Ks) per
client’s request
Encrypted in
non-volatile
memory
Per client’s
request or zeroize
request
Sign
messages/verify
signatures
Client
HMAC keys
HMAC keys
Generated by
ANSI X9.31
DRNG
Via TLS in
encrypted form
(encrypted with
TLS Ks) per
client’s request
Encrypted in
non-volatile
memory
Per client’s
request or zeroize
request
Compute keyed-
MACs
Client
certificate
X.509
certificate
Input in
ciphertext
over TLS
Via TLS in
encrypted form
(encrypted with
TLS Ks) per
client’s request
In non-volatile
memory
Per client’s
request or by
zeroize request
Encrypt
data/verify
signatures
Crypto
Officer
passwords
Character
string
Input in
plaintext
Never In
non-volatile
memory
At operator delete
or by zeroize
request
Authenticate
Crypto Officer
User
passwords
Character
string
Input in
plaintext
Never In
non-volatile
memory
At operator delete
or by zeroize
request
Authenticate
User
Cluster
Member
password
Character
string
Input in
ciphertext
over TLS
Never In
non-volatile
memory
At operator delete
or zeroize request
When a device
attempts to
become a
Cluster Member
HP User
RSA public
key
2048-bit RSA
public key
Input in
plaintext at
factory
Never In
non-volatile
memory
At installation of a
patch or new
firmware
Authenticate HP
User
Cluster key Character
string
Input in
ciphertext
over TLS
Never In
non-volatile
memory
At operator delete
or by zeroize
request
Authenticate
Cluster Member
Firmware
upgrade
key
1024-bit RSA
public key
Input in
plaintext at
factory
Never In
non-volatile
memory
When new
firmware upgrade
key is input
Used in firmware
upgrade integrity
test
