Enterasys Networks XSR-3020 User Manual
Page 57
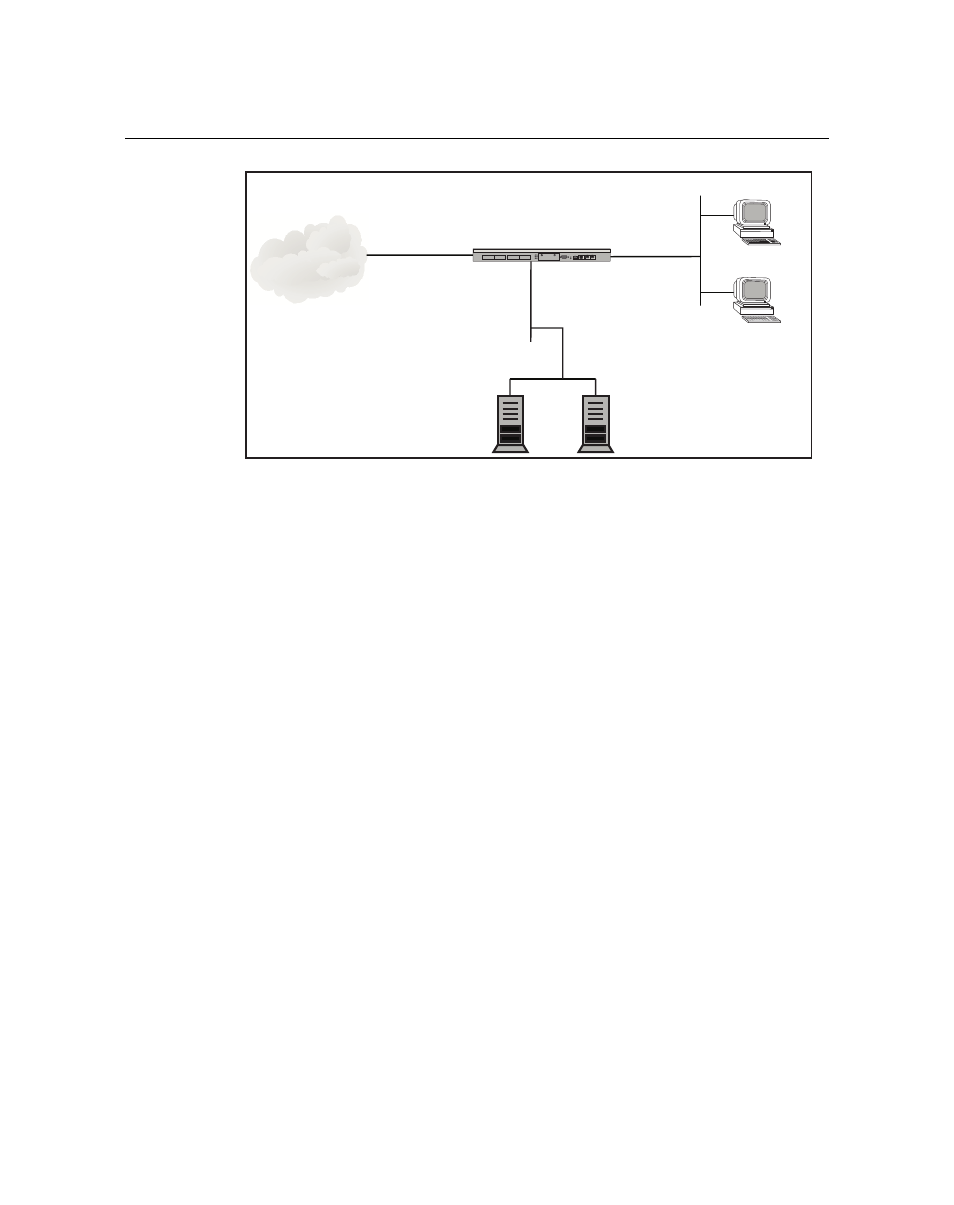
Firewall Sample Configuration
XSR Getting Started Guide 3-13
Figure 3-1 XSR with Firewall Topology
In this configuration, the firewall provides protected access from the private to dmz networks. That
is, access is restricted to Web and mail traffic only. The hosts in the private network are provided
full access to the Internet but access is denied from the Internet to the private network. Also, all Java
and ActiveX pages, IP options, IP broadcast and multicast packets are banned.
Begin by specifying network objects for private, dmz, and Mgmt networks:
XSR(config)#ip firewall network dmz 220.150.2.16 mask 255.255.255.240 internal
XSR(config)#ip firewall network private 220.150.2.32 mask 255.255.255.240
internal
XSR(config)#ip firewall network Mgmt 220.150.2.35 mask 255.255.255.0 internal
Log only critical events:
XSR(config)#ip firewall logging event-threshold 3
Set policies between the dmz and external networks. Note that policy objects and names are case-
sensitive and you must cite network names exactly:
XSR(config)#ip firewall policy a1 private dmz HTTP allow
XSR(config)#ip firewall policy a2 dmz private HTTP allow
XSR(config)#ip firewall policy a3 private dmz HTTP allow
XSR(config)#ip firewall policy a4 dmz private HTTP allow
Set the policies between the dmz and external networks:
XSR(config)#ip firewall policy a5 ANY_EXTERNAL dmz SMTP allow
XSR(config)#ip firewall policy a6 dmz ANY_EXTERNAL SMTP allow
XSR(config)#ip firewall policy a7 ANY_EXTERNAL dmz SMTP allow
XSR(config)#ip firewall policy a8 dmz ANY_EXTERNAL SMTP allow
Set policies to allow any traffic from private to external and Mgmt networks:
XSR(config)#ip firewall policy a9 private ANY_EXTERNAL ANY_TCP allow
XSR(config)#ip firewall policy Telnetsess Mgmt Mgmt Telnet allow bidirectional
Allow ICMP traffic to pass from the dmz to private, private to all external, and all external to private
networks:
XSR(config)#ip firewall filter allowICMP private dmz protocol-id 1
XSR(config)#ip firewall filter allowICMP private ANY_EXTERNAL protocol-id 1
XSR(config)#ip firewall filter allowICMP ANY_EXTERNAL dmz protocol-id 1
Internet
206.12.44.16/28
Frame Relay
FE2
FE1
220.150.2.32/28
220.150.2.37
220.150.2.36
220.150.2.35
220.150.2.16/28
220.150.2.17
DMZ
Internal
S1
Web server
(HTTP)
220.150.2.19
Mail server
(SMTP)
220.150.2.18
XSR-3020
