Operation of a p2mp gre tunnel – H3C Technologies H3C SecPath F1000-E User Manual
Page 18
2
traditional P2P GRE tunnel mode. Then, a GRE tunnel will be established dynamically between the
headquarters and each branch.
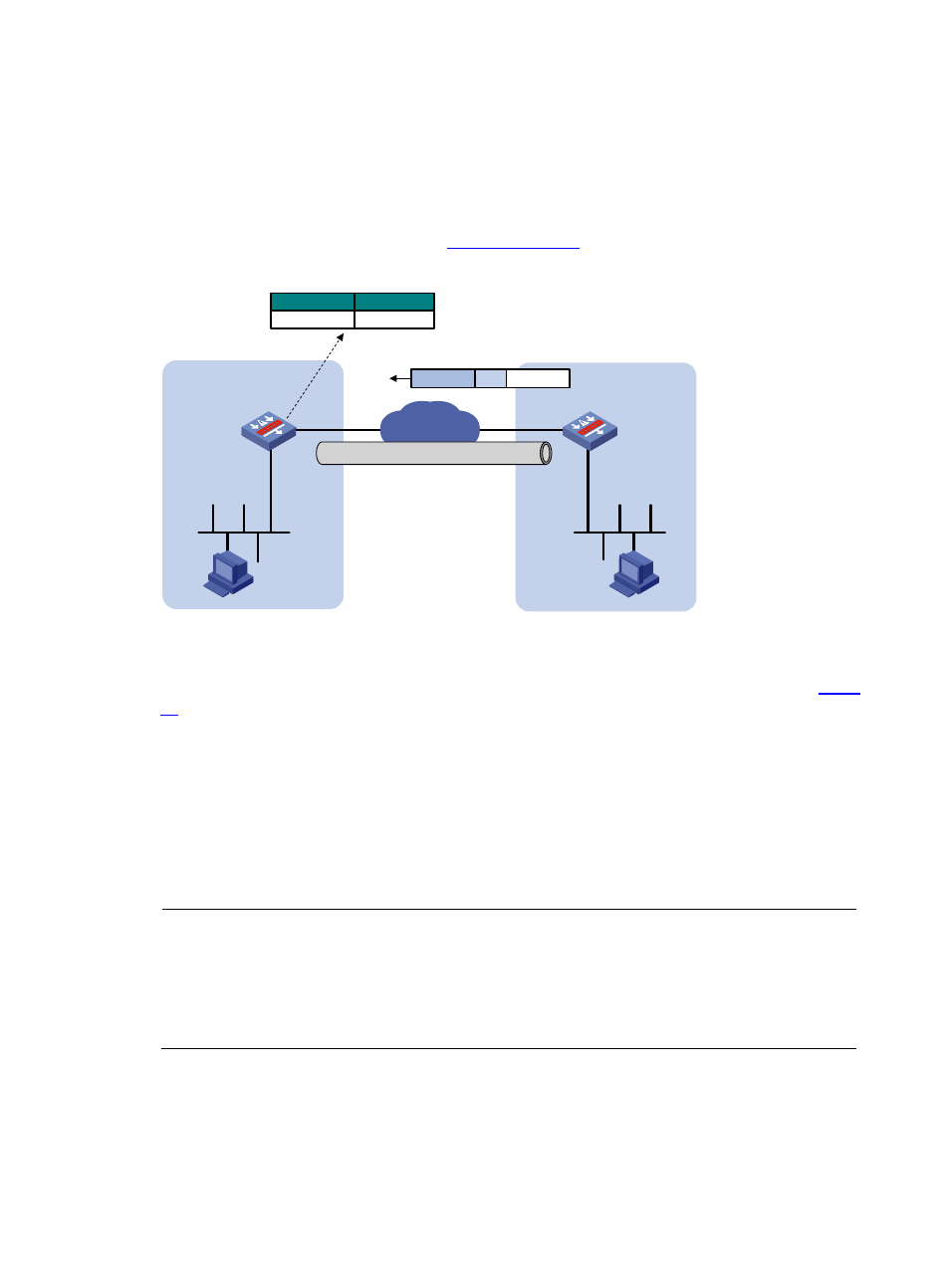
Operation of a P2MP GRE Tunnel
The encapsulation and de-encapsulation of P2MP GRE tunnel packets are the same as those of P2P GRE
tunnel packets. For more information, see
Figure 12 Learning tunnel destination addresses dynamically
10.2.1.2/24
10.1.1.2/24
Tunnel0
10.3.1.1/24
11.1.1.1/24
11.1.1.2/24
IPv4 network
GRE tunnel
Tunnel0
10.3.1.2/24
Device A
Device B
Host A
Host B
Headquarters
Branch
10.1.1.2
GRE
11.1.1.2
Tun Dest
11.1.1.2
Dest
10.1.1.0/24
Different from a P2P GRE tunnel, a P2MP GRE tunnel does not require manual configuration of the tunnel
destination addresses but learns them from GRE tunnel packets received from peers. As shown in
, Device A resides at the headquarters and has a P2MP GRE tunnel interface configured, while Device
B resides at a branch and has a P2P GRE tunnel interface configured. After Device A receives a GRE
packet from Device B, it establishes a tunnel entry, taking the source address in the transport protocol
(IPv4) header as the tunnel destination address and the source address in the passenger protocol (IPv4)
header (that is, the private network address of the branch) as the packet destination address.
When forwarding a packet through a P2MP GRE tunnel, the device searches the tunnel entries for the
tunnel destination address according to the packet’s destination address, and then encapsulates the
packet with GRE and then with IPv4, using the tunnel destination address as the destination address in
the transport protocol header.
NOTE:
The mask length of the packet destination address in a tunnel entry is configurable. After you configure a
mask length for a packet destination address, the node at the headquarters establishes only one tunnel
entry for private IP addresses in the same network segment, thus reducing the number of tunnel entries on
the node at the headquarters and allowing branches to initiate establishment of tunnels by sending
emulated data to the node at the headquarters.
