Siemens se5880 User Manual
Page 73
SIEMENS se5880 Ethernet Security Router
User’s Guide
Chapter 6 Security Setup
IKE/IPSec Configuration
SIEMENS
67
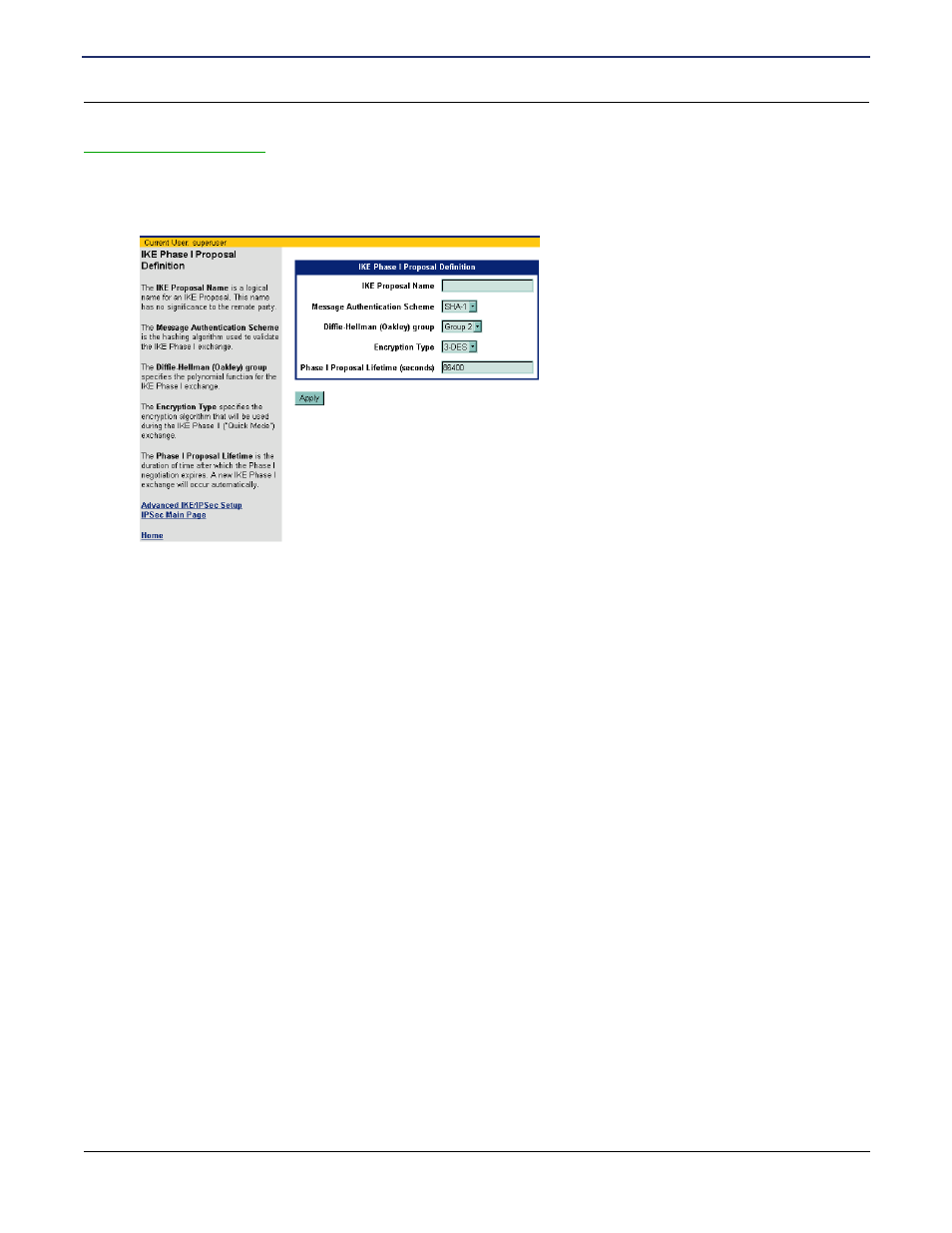
IKE Proposals Definition
IKE I proposals specify how packets will be encrypted/authenticated for Phase I. To define a new IKE proposal:
1. Click Create next to IKE Proposals from the Advanced IKE/IPSec Setup page. This displays the IKE
Proposal Definition page.
2. In IKE Proposal Name, enter a logical name for the IKE Proposal Definition. This name is of no
importance to the remote IKE peer.
3. From the Message Authentication Scheme drop-down menu, select one of the following hashing
(authentication) options to use to validate IKE Phase I exchange:
•
MD5: Performs message authentication using Message Digest 5.
•
SHA1: Performs message authentication using Secure Hashing Algorithm 1 (default).
4. From the Diffie-Hellman (Oakley) Group drop-down menu, select one of the following Diffie-Hellman key
generation groups to use during IKE Phase I exchange:
•
Group 1: Uses Diffie-Hellman Group 1 (768 bits).
•
Group 2: Uses Diffie-Hellman Group 2 (1024 bits).
5. From the Encryption Type drop-down menu, select one of the following encryption types to use during
IKE Phase II (Quick Mode) exchange:
•
DES: Encrypts using a 56-bit key.
•
3DES: Encrypts using three 56-bit keys to produce 168-bit encryption.
6. In Phase I Proposal Lifetime, enter the number of seconds after which the Phase I negotiation expires.
The default is 1800 seconds. Once this time is elapsed, the system will renegotiate the IKE connection.
7. Click Apply.
