Appendix d: secure applications, Restricted switching – Thinklogical VX Routers Manual User Manual
Page 57
®
VX Router Manual Rev. O September, 2014
Page 56
VX
320Video/Audio SD Flash Card Replacement
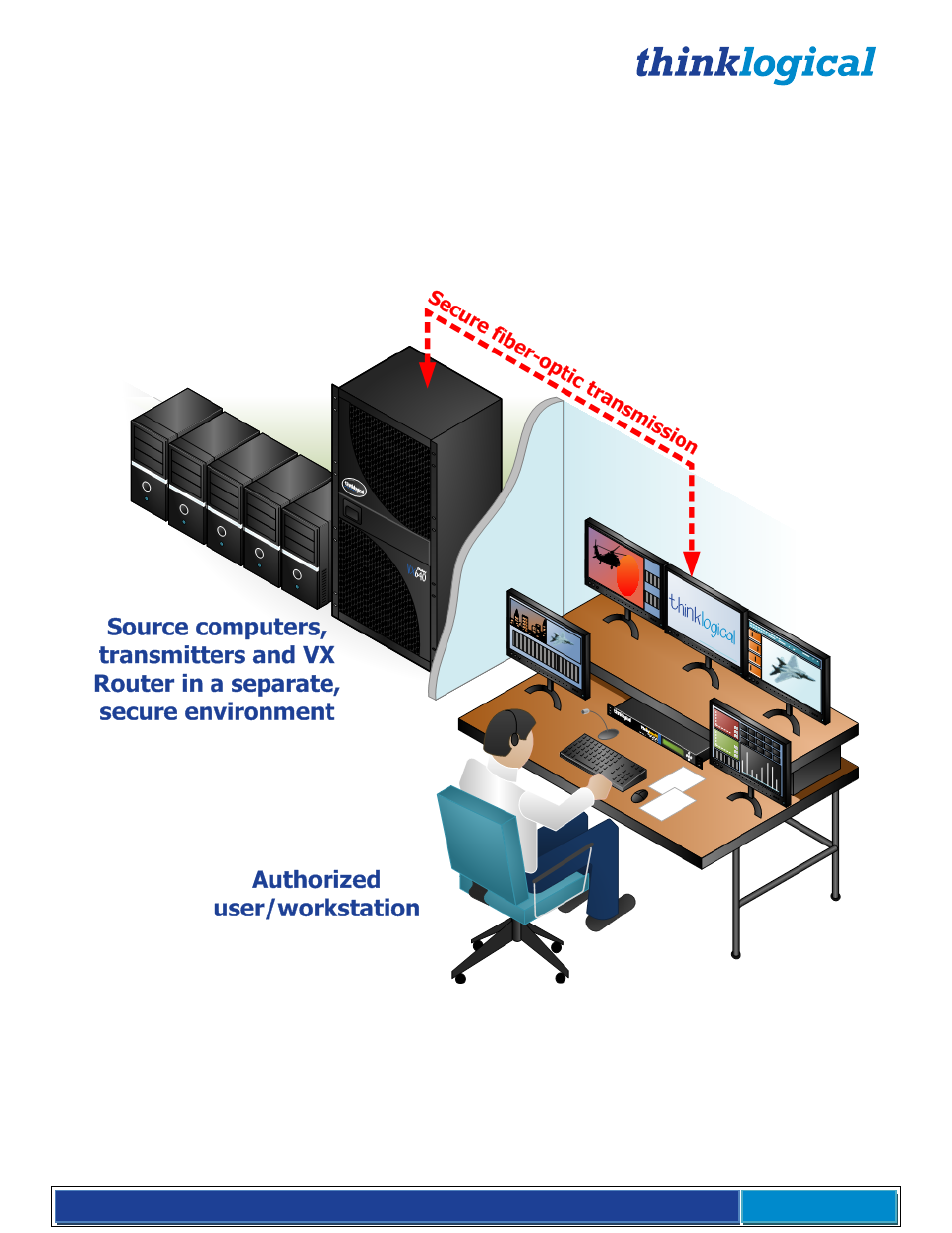
Appendix D: Secure Applications
VX Router Control
When used in a secure application, the VX Router and External Computer (server) used to manage the Router
must be located in a physically secure environment to which only trusted administrators have access. Similarly,
the server used to manage the VX Router must be physically protected and have suitable identification/
authentication mechanisms to ensure that only trusted administrators have access.
Thinklogical’s VX Router uses two methods for secure routing. One is known as Restricted Switching and
the other is known as Partitioning. These methods can be deployed singularly or jointly, depending on
security requirements.
Restricted Switching
Restricted Switching provides multiple levels of security classification domains on the same VX Router. Each
destination must ensure that no unauthorized content is displayed or accessed, therefore, each input and
output needs to be prioritized. Priorities can range from 1 to the total number of ports in the VX Router. An
