10 trusted wireless stations, Data - trusted wireless stations, Trusted wireless stations – AirLive WN-300R User Manual
Page 34
Radius Port
Enter the port number used for connections to the Radius
Server.
Shared Key
Enter the shared key. Data is encrypted using a key derived
from the network key. Other Wireless Stations must use the
same key. The key must be from 8 to 63 characters in length.
Encryption
The encryption method is TKIP. Wireless Stations must also
use TKIP.
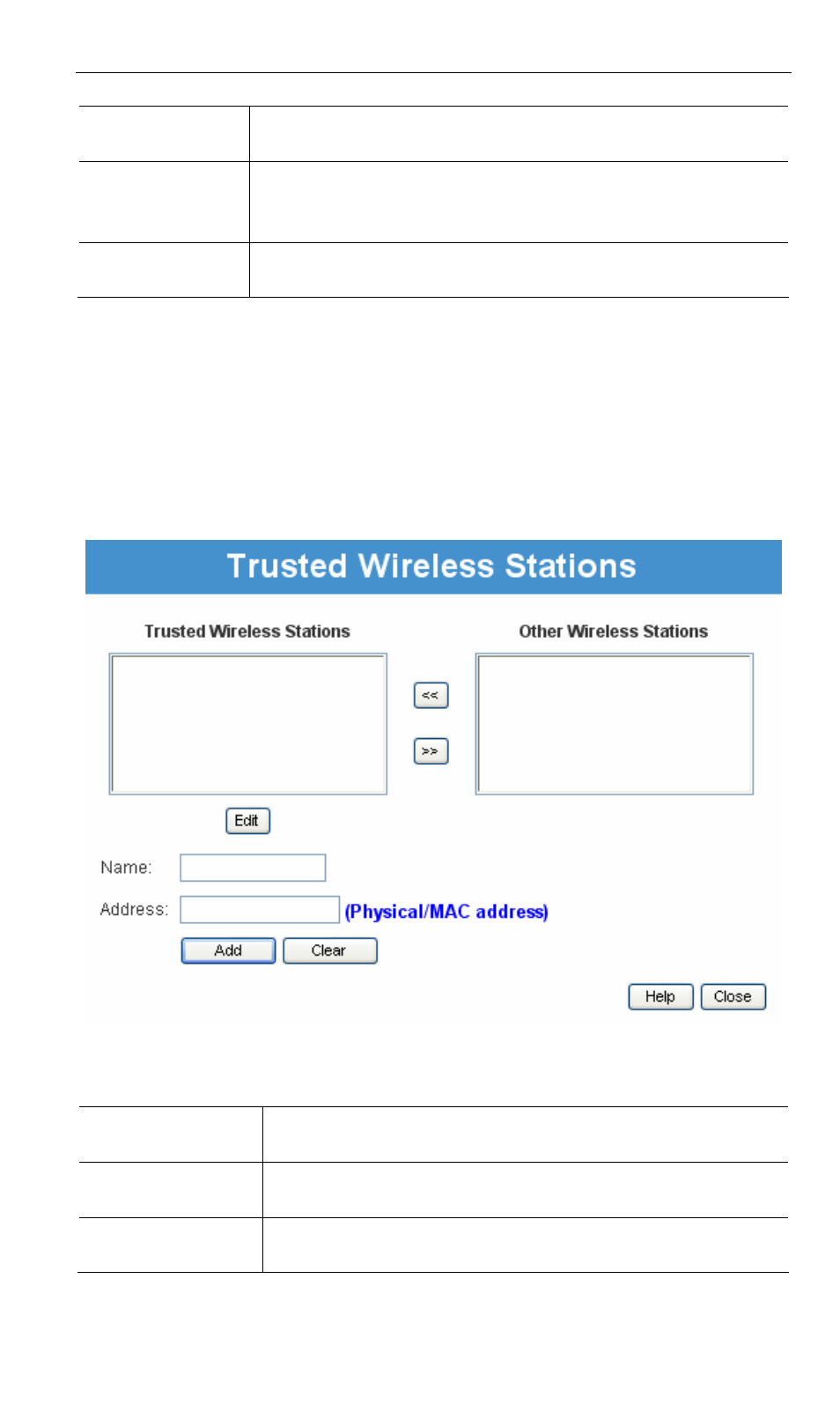
3.10 Trusted Wireless Stations
This feature can be used to prevent unknown Wireless stations from using the Access
Point. This list has no effect unless the setting Allow access by trusted stations only is
enabled.
To change the list of trusted wireless stations, use the Modify List button on the Ac-
cess Control screen. You will see a screen like the sample below.
Figure 13: Trusted Wireless Stations
Data - Trusted Wireless Stations
Trusted Wireless
Stations
This lists any Wireless Stations which you have designated
as “Trusted”.
Other Wireless
Stations
This list any Wireless Stations detected by the Access Point,
which you have not designated as "Trusted".
Name
The name assigned to the Trusted Wireless Station. Use this
when adding or editing a Trusted Station.
AirLive WN-300R User’s Manual
28
