Linksys BEFW11S4 User Manual
Page 28
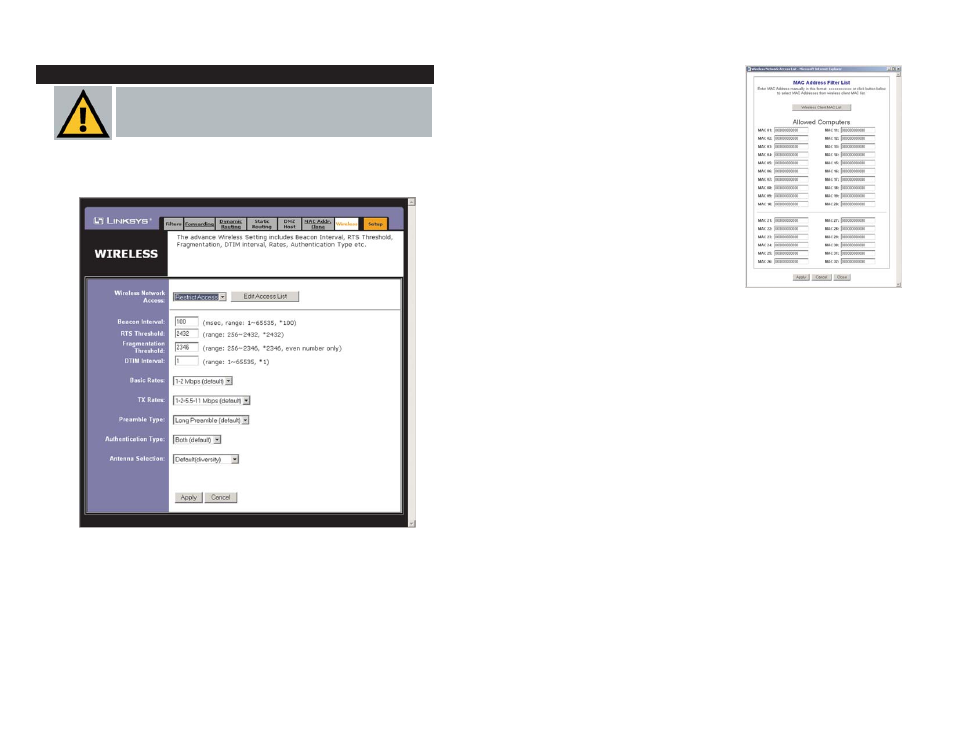
To do this, click the Edit Access List but-
ton, which will open the MAC Address
Filter List window, shown in Figure 5-23.
Enter the MAC Addresses of the comput-
ers (or wireless node) you wish to allow.
To view what wireless devices are cur-
rently accessing your wireless network,
click the Wireless Client MAC List but-
ton.
When you have set the MAC Addresses
you wish to allow, click the Apply button
to save the changes or the Cancel button
to undo your changes. Click the Close
button to close the window, ignoring any
changes you made.
Beacon Interval. This value indicates the frequency interval of the beacon.
A beacon is a packet broadcast by the Router to keep the network synchro-
nized. A beacon includes the wireless LAN service area, the IP address, the
Broadcast destination addresses, a time stamp, Delivery Traffic Indicator
Maps, and the Traffic Indicator Message (TIM).
RTS Threshold. This value should remain at its default setting of 2,346.
Should you encounter inconsistent data flow, only minor modifications are
recommended.
Fragmentation Threshold. This value indicates how much of the Router’s
resources are devoted to recovering packet errors. The value should remain
at its default setting of 2,346. If you have decreased this value and experi-
ence high packet error rates, you can increase it again, but it will likely
decrease overall network performance. Only minor modifications of this
value are recommended.
DTIM Interval. This value indicates the interval of the Delivery Traffic
Indication Message (DTIM). A DTIM field is a countdown field informing
clients of the next window for listening to broadcast and multicast mes-
sages. When the Router has buffered broadcast or multicast messages for
associated clients, it sends the next DTIM with a DTIM Interval value.
Clients for the Router hear the beacons and awaken to receive the broadcast
and multicast messages.
47
Before making any changes to the Wireless tab, shown in Figure 5-22, please
check the wireless settings for all your wireless PCs, as these changes will alter
the Router’s effectiveness. In most cases, these settings do not need to be
changed.
Wireless Network Access. From this drop-down menu, you can determine
how restricted you would like to make your wireless network. By selecting
Allow All, you open your wireless network to all users who have access.
When Restrict Access is selected, you can allow access to your network
according the MAC Address of the wireless node trying to gain access.
Advanced Tab: Wireless
Important: Wireless is an Advanced Function. No changes
should be made to this tab without a thorough understanding of
networking concepts.
Figure 5-22
48
Figure 5-23
