Managing the black list, Configuring firewall settings 134 – SMC Networks ADSL Barricade SMC7204BRA User Manual
Page 132
Configuring Firewall Settings
134
Managing the Black List
If data packets are received that violate the firewall settings or any
of the IP filter rules, then the source IP address of the offending
packets can be blocked from such accesses for a specified period
of time. You can enable or disable use of the black list using the
settings described above. The source computer remains on the
black list for the period of time that you specify.
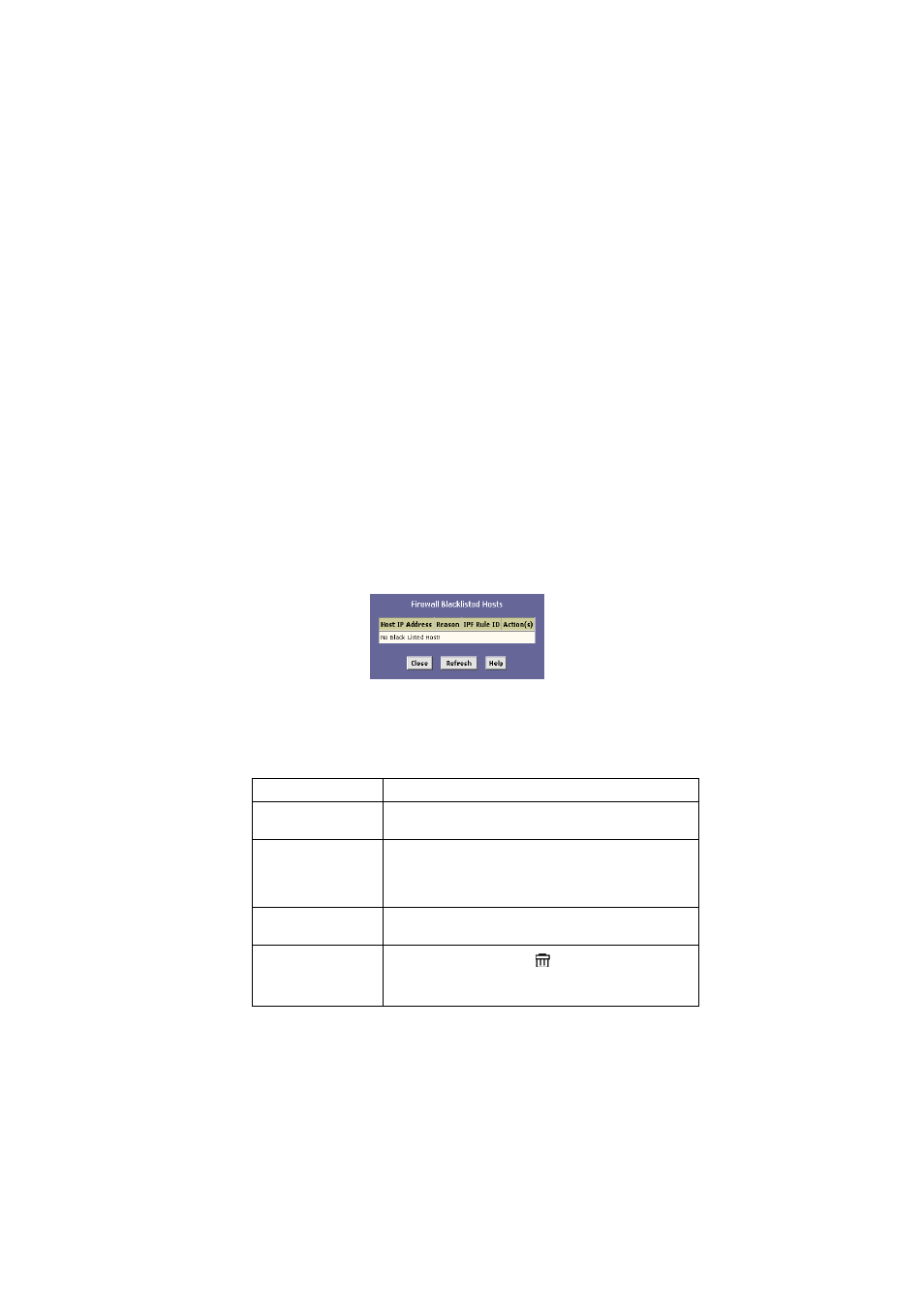
To view the list of currently blacklisted computers, click [Black List]
at the bottom of the [Firewall Configuration] page. The [Firewall
Blacklisted Hosts] page appears, as shown in Figure 46.
Figure 46. Firewall Blacklisted Hosts Page
The table displays the following information for each entry.
Field
Description
Host IP Address
This is the IP address of the computer that sent the
packet(s) that caused the violation
Reason
This is a short description of the type of violation. If the
packet violated an IP filter rule, the custom text from the
[Log Tag] field will display. (See Creating IP Filter Rules
on page 138.)
IPF Rule ID
If the packet violated an IP filter rule, this field will display
the ID assigned to the rule.
Action(s)
This field displays an icon (
) you can click on to delete
the entry from the list, if you want it to be removed prior to
its automatic timed expiration.
