Unregistered policy, Inline nac design procedures, Determine nac controller location – Enterasys Networks 9034385 User Manual
Page 92: Unregistered policy -28, Inline nac design procedures -28, Determine nac controller location -28, Service for the quarantine role -28, Figure 5‐8
Inline NAC Design Procedures
5-28 Design Procedures
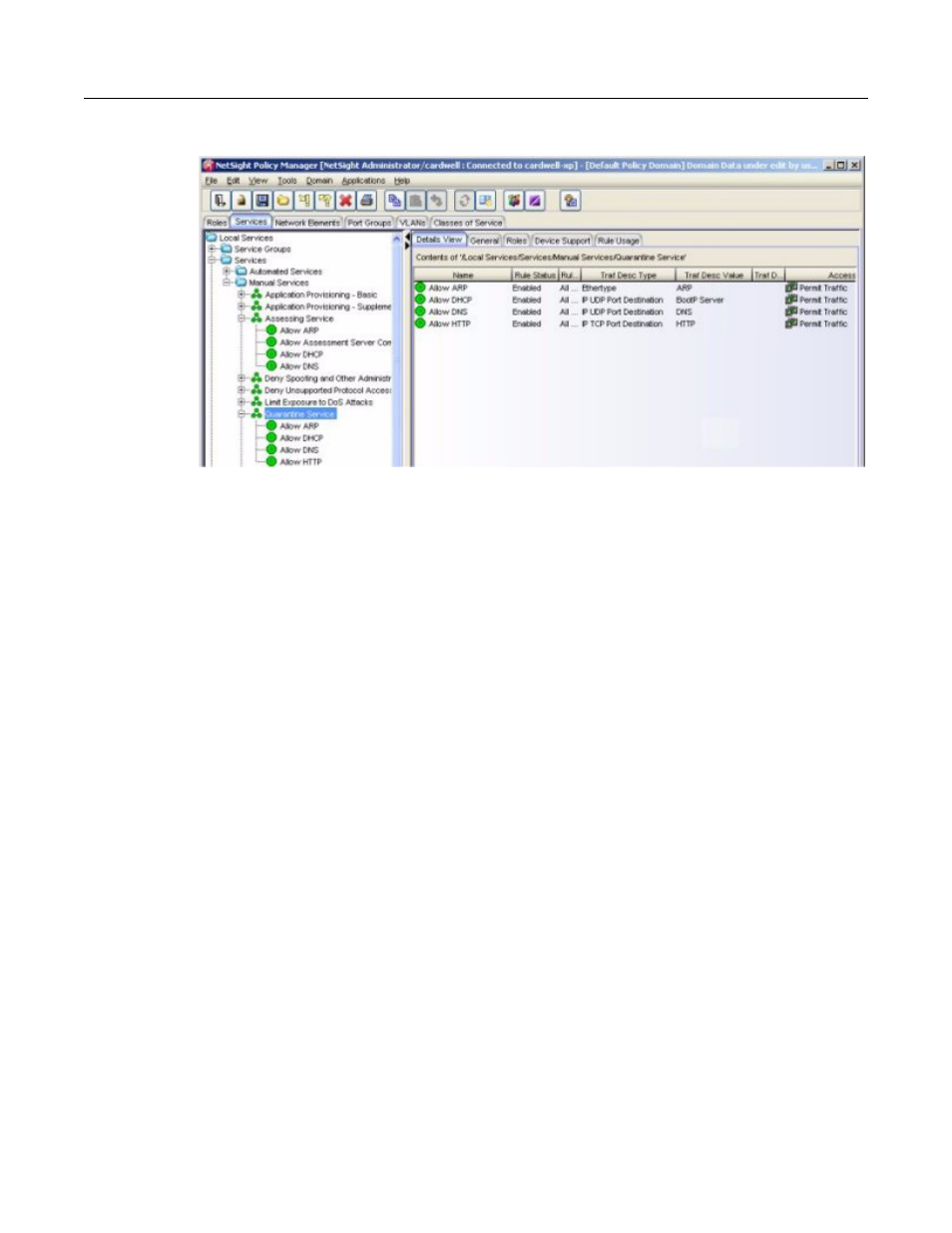
Figure 5-8 Service for the Quarantine Role
Furthermore, the Quarantine Policy and other network infrastructure devices must be configured
to implement HTTP traffic redirection for quarantined end‐systems to return web notification of
the quarantined state of an end‐system.
Unregistered Policy
If MAC (network) registration is configured in the NAC deployment, an “Unregistered” policy
can be assigned to connecting end‐systems while they are unregistered on the network. This
policy must be configured to allow basic services such as ARP, DNS, DHCP, and to implement
HTTP traffic redirection to return web‐based notification for unregistered end‐systems. (Because
this configuration is similar to the Quarantine Policy and the Assessment Policy, those policies
could be assigned to unregistered end‐systems, if desired).
Inline NAC Design Procedures
The following section continues the Enterasys NAC design procedure with steps specifically
relating to the implementation of inline NAC with the NAC Controller.
1. Determine NAC Controller Location
Because the NAC Controller is placed inline with traffic sourced from connecting end‐systems, the
location of NAC Controllers is directly dependent on the network topology. NAC Controllers are
typically placed between the edge where end‐systems connect to the network (for example, the
wired and wireless access edge, or the remote access edge behind a VPN concentrator) and the
networkʹs core and data center where mission critical infrastructure resources reside. This way,
noncompliant end‐systems can be restricted from communicating to mission critical resources.
With the NAC Controller acting as the authorization point for traffic enforcement with inline
NAC, there is a fundamental trade‐off when positioning the NAC Controller in the network
topology: the closer the NAC Controller is placed to the edge of the network, the higher the level
of security is achieved, in that end‐systems are authorized closer to the point of connection and
end‐systems deemed noncompliant have access to a smaller set of network resources.
