Summary, Summary -16, Enterasys nac deployment models -16 – Enterasys Networks 9034385 User Manual
Page 38
Summary
2-16 NAC Deployment Models
Summary
Enterasys supports all of the five key NAC functions: detection, authentication, assessment,
authorization, and remediation. However, not all five functions need to be implemented
concurrently in a NAC deployment to derive value from the solution. The four NAC deployment
models each yield unique value propositions to the IT personnel managing the network, and
provide a logical progression to deploying the full Enterasys NAC solution.
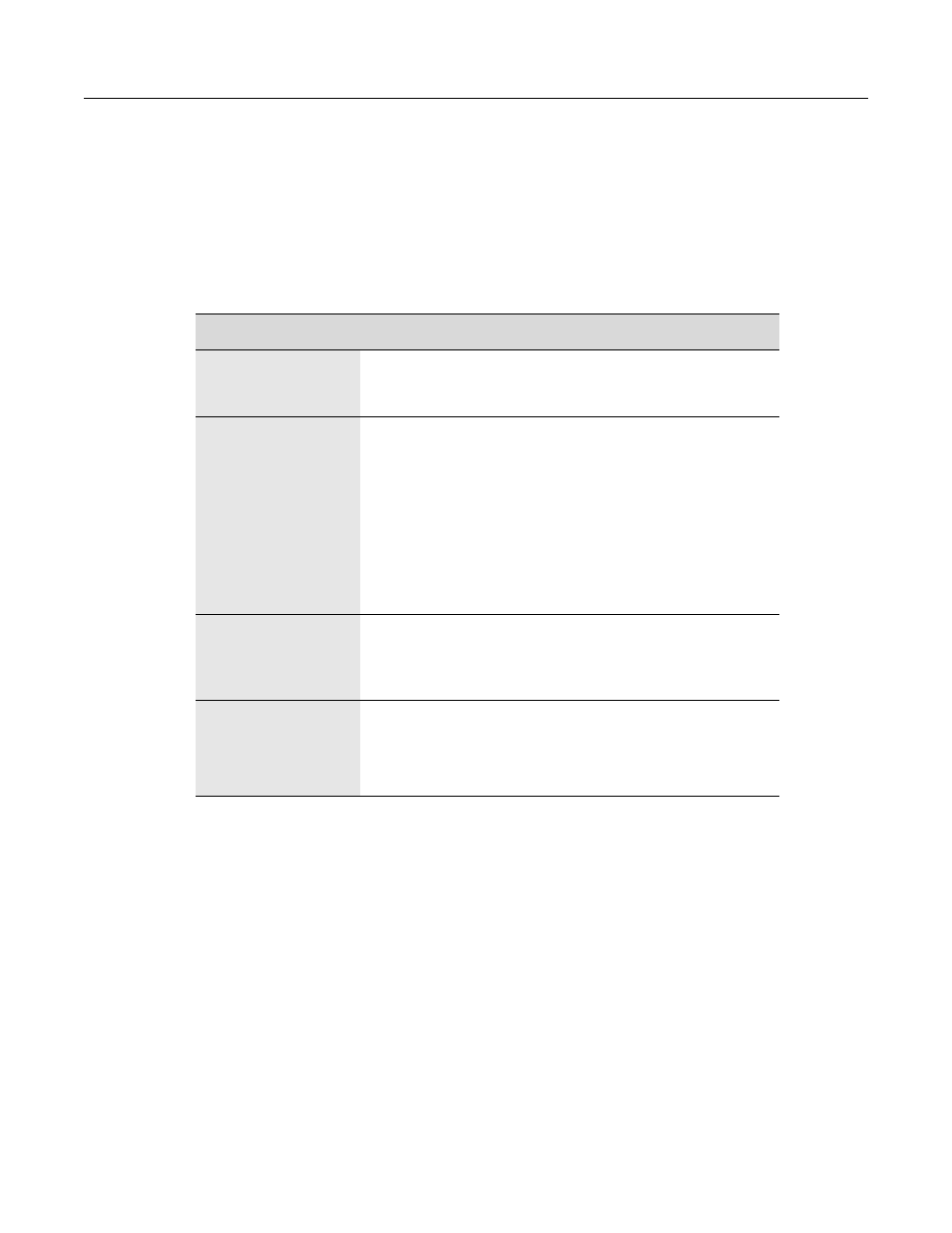
The following table summarizes the value and features of each deployment model.
.
Table 2-5 Enterasys NAC Deployment Models
Deployment Model
Value
Model 1:
End-System Detection
and Tracking
• End-system and user tracking.
• IP-to-ID functionality for Security Information Management
(SIM).
Model 2:
End-System
Authorization
In addition to the values from Model 1:
• Location-based authorization using Security Domains and “Lock
MAC” features.
• Special handling of end-systems or users with MAC/User
overrides that let you specify a unique set of authentication and
authorization parameters for particular devices or users.
• MAC registration where new end-systems register via a web
page before being allowed access to the network.
• Location-independent end-system quarantine action with
NetSight Automated Security Manager integration.
Model 3:
End-System
Authorization with
Assessment
In addition to the values from Models 1 and 2:
• Security posture compliance verification of connecting end-
systems with dynamic quarantine action using integrated or
external assessment.
Model 4:
End-System
Authorization with
Assessment and
Remediation
In addition to the values from Models 1, 2, and 3:
• Self-service remediation of non-compliant end-systems without
impacting IT operations.
