Scenario 4 implementation, Scenario 4 implementation -12, Vpn remote access -12 – Enterasys Networks 9034385 User Manual
Page 50
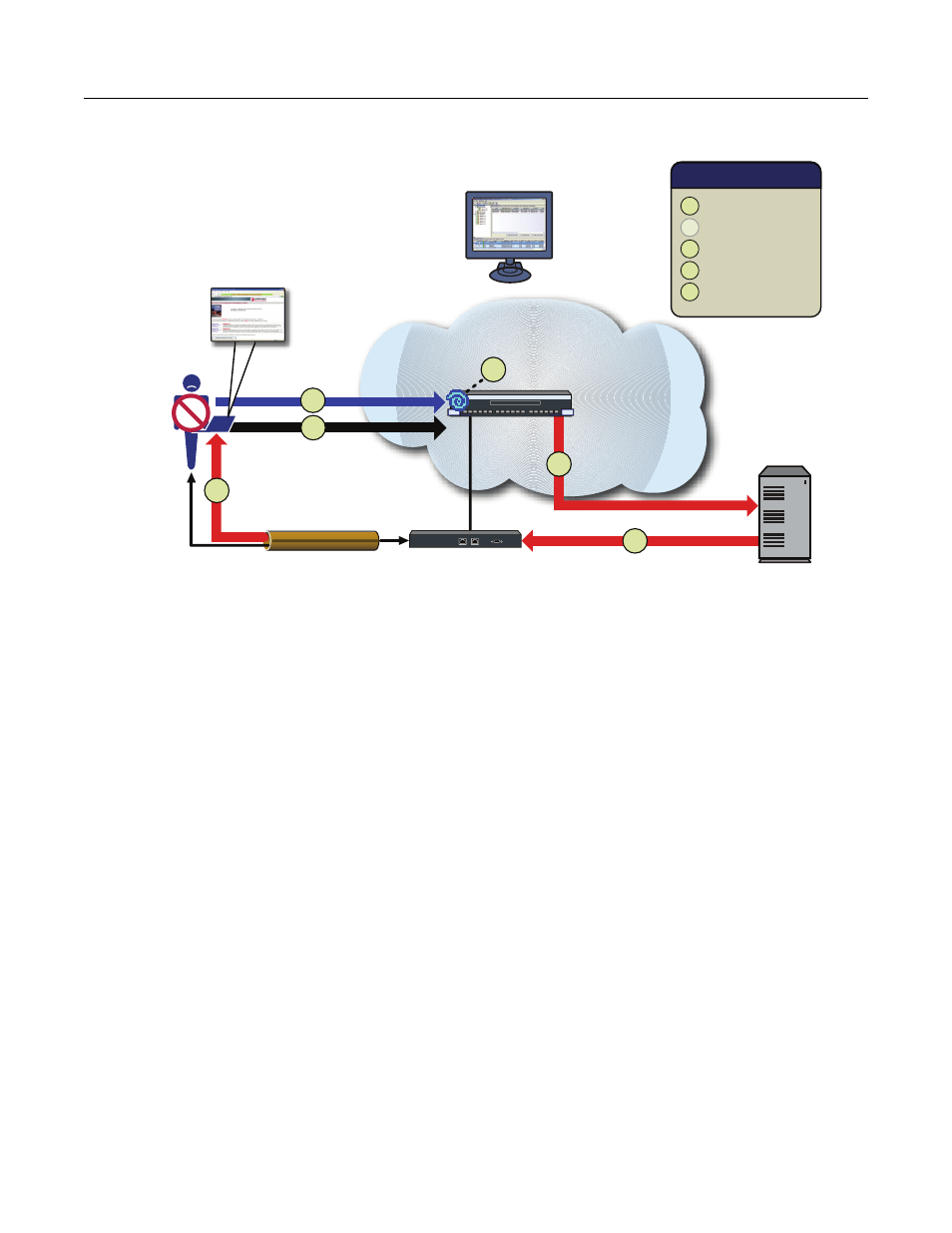
Scenario 4: VPN Remote Access
3-12 Use Scenarios
Figure 3-6 VPN Remote Access
Scenario 4 Implementation
In the VPN remote access use scenario, the five NAC functions are implemented in the following
manner with the deployment of the NAC Controller for inline network access control.
1. Detection ‐ The userʹs end‐system successfully establishes a VPN tunnel with the VPN
concentrator, and the VPN concentrator transmits unencrypted data traffic onto the network that
traverses the NAC Controller. This traffic is sourced from an IP address not previously seen by the
controller.
2. Authentication ‐ Authentication is most likely disabled altogether on the NAC Controller,
trusting that the downstream VPN concentrator authenticated the connecting user.
3. Assessment ‐ The NAC Controller requests an assessment of the end‐system according to
predefined security policy parameters. The assessment can be agent‐based or agent‐less, and is
executed locally by the NAC Controllerʹs assessment functionality and/or remotely by a pool of
assessment servers.
4. Authorization ‐ Once authentication and assessment are complete, the NAC Controller
allocates the appropriate network resources to the end‐system based on authentication and/or
assessment results. This is implemented locally on the NAC Controller by assigning a policy to
traffic sourced from the end‐system. If authentication fails and/or the assessment results indicate a
noncompliant end‐system, the NAC Controller can either deny the end‐system access to the
network, or quarantine the end‐system by assigning a particular policy on the controller.
1
3
3
5
Enterasys
NAC Manager
NAC
Controller
(inline appliance)
Assessment
Server
Role= Quarantine
1
2
3
4
5
NAC Functions
Detect
Authenticate
Assess
Authorize
Remediate
VPN Concentrator
Remediation
Web Page
3
4
