Network with non-intelligent edge -4 – Enterasys Networks 9034385 User Manual
Page 56
Survey the Network
4-4 Design Planning
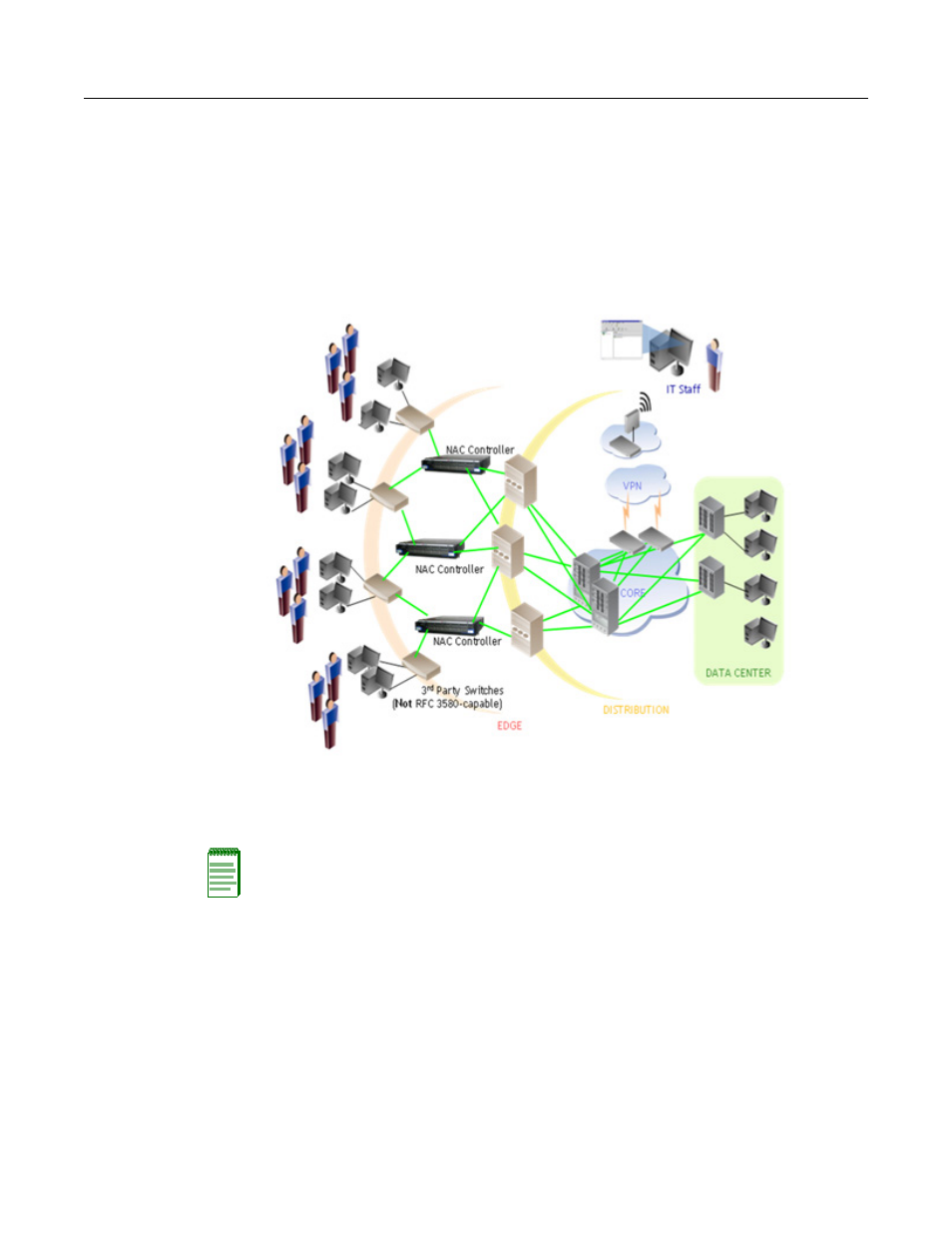
For the inline implementation of the Enterasys NAC solution, the NAC Controller authenticates
and authorizes end‐systems locally on the appliance, and does not rely on the capabilities of
downstream infrastructure devices. Because of this, the NAC Controller can be utilized in
networks where non‐intelligent and/or intelligent infrastructure devices exist at the edge of the
network. If the network does not have an intelligent edge, then the NAC Controller must be
deployed in order to provide the authentication and authorization capabilities required for
implementing network access control, as shown in
.
Figure 4-2 Network with Non-Intelligent Edge
2. Evaluate Policy/VLAN and Authentication Configuration
For a network with an intelligent edge, the second step in surveying your network is to evaluate
the network authentication method currently being used, and how the deployment of Enterasys
NAC will affect it. A network with an intelligent edge can be classified into one of two cases: either
authentication is deployed on the network or it is not.
Case #1: No authentication method is deployed on the network.
If authentication is not configured on the network, out‐of‐band NAC can be deployed with
minimal configuration by implementing MAC authentication on the intelligent edge of the
network (if the edge switches support MAC authentication). The NAC Gateway can be configured
Note: This step is not necessary if in step 1 you determined that the network does not have an
intelligent edge and the inline NAC Controller appliance will be deployed to provide the
authentication and policy enforcement capabilities.
