Verilink Red Zone Encryption (REMS) (880-502423-001) Product Manual User Manual
Page 39
How the BRC communicates with the FBR
Red Zone Encryption Management System (REMS) User Manual
3-13
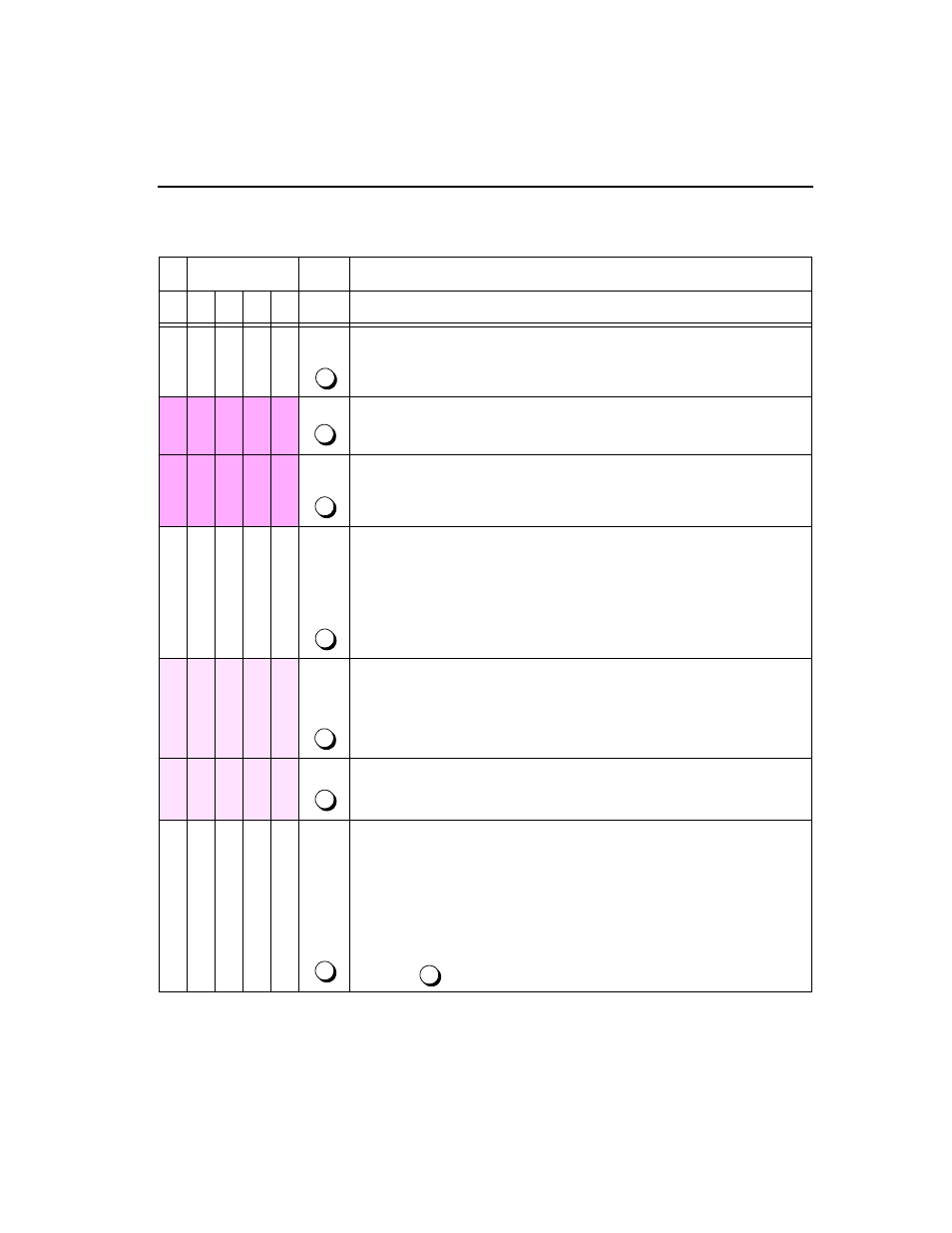
Table 3-1
Decoding the 4-bit Message Field
Message bit #
1
2
3
4
Site
Code or Message State
1
0
1
1
FBR Code
The FBR code, placed in the offset frame bit positions, is sent from the far-end
FBR.
0
1
1
0
Encrypted FBR Code
As it passes through the encryptor, the FBR code is encrypted.
1
⇓
1
⇓
0
⇓
1
⇓
Originating BRC performance message
Network performance data is coded as a BRC performance message, ready to
be inserted and sent to the near-end Access Manager 2000.
1
0
1
1
Combined encrypted FBR code and BRC performance message
The encrypted FBR code and the BRC performance message are combined into
one message using a 2-input exclusive-OR function. Simply, for each bit
position, if the bit values which are being combined are:
• different, the resulting value is “1
• the same, the resulting value is “0”
0
1
1
0
Decrypted FBR code (with inserted BRC performance message
As the exclusive-OR’ed text passes through the encryptor, it is decrypted to
produce this result. Remember that the decryption key has now been applied to a
message which was created from encrypted FBR code and a plain text BRC
performance message, so the result will differ from original exclusive-OR’ed text.
1
⇓
0
⇓
1
⇓
1
⇓
Local FBR reference code
The local FBR refers to the FBR code it was expecting.
1
1
0
1
Resulting BRC performance message
The FBR extracts the BRC message by using a second exclusive-OR function to
compare the received code with the FBR reference code. Simply, each bit
position is compared to the expected value. If the result of the comparison is:
• different, the output is a “1”
• the same, the output is a “0”
The resulting message is the same as the original BRC performance message
created in
.
A
B
C
D
E
F
G
C
