About the p2 proposal, About replay detection – D-Link DFL-500 User Manual
Page 58
DFL-500 User Manual
58
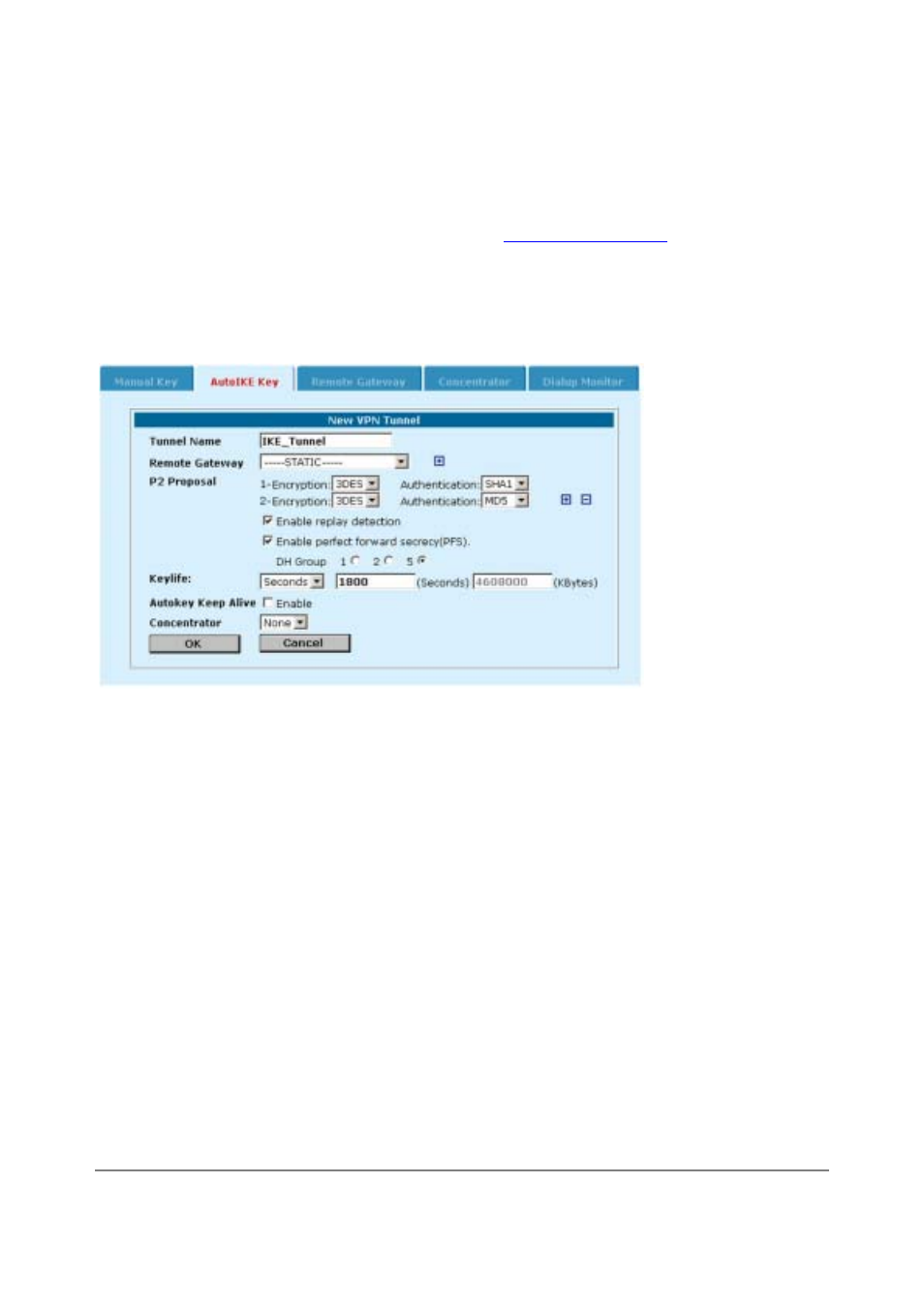
Autokey Keep
Alive
Enable Autokey Keep Alive to keep the VPN tunnel running even if no data is being
processed.
Concentrator
Select a concentrator if you want the tunnel to be part of a hub and spoke VPN
configuration. If you use the procedure,
Adding a VPN concentrator
to add the tunnel to a
concentrator, the next time you open the tunnel, the Concentrator field displays the name of
the concentrator to which you have added the tunnel.
• Select OK to save the AutoIKE key VPN tunnel.
Adding an AutoIKE key VPN tunnel
About the P2 proposal
During tunnel negotiation, the VPN gateways negotiate to select a common algorithm for data communication.
When you select algorithms for the P2 proposal, you are selecting the algorithms that the DFL-500 NPG
proposes during phase 2 negotiation. For phase 2 to be completed successfully, each VPN gateway must
have at least one encryption and one authentication algorithm in common.
• Select DES to propose to encrypt packets using DES encryption.
• Select 3DES to propose to encrypt packets using triple-DES encryption.
• Select MD5 to propose to use MD5 authentication.
• Select SHA1 to propose to use SHA1 authentication.
• Select NULL to propose that the VPN packets not be encrypted or that a hash is not made for
authentication.
About replay detection
IPSec tunnels can be vulnerable to replay attacks. A replay attack occurs when an unauthorized party
intercepts a series of IPSec packets and replays them back into the tunnel. An attacker can use this
technique to cause a denial of service (DoS) attack by flooding the tunnel with packets. An attacker could also
change and then replay intercepted packets to attempt to gain entry to a trusted network.
Enable replay detection to check the sequence number of every IPSec packet to see if it has previously been
received. If packets arrive out of sequence, the DFL-500 NPG discards them.
