Compex Systems WPE53G User Manual
Page 143
Page 137
S
S
t
t
e
e
p
p
1
1
:
:
Select whether to use
E
E
A
A
P
P
-
-
T
T
T
T
L
L
S
S
or
E
E
A
A
P
P
-
-
P
P
E
E
A
A
P
P
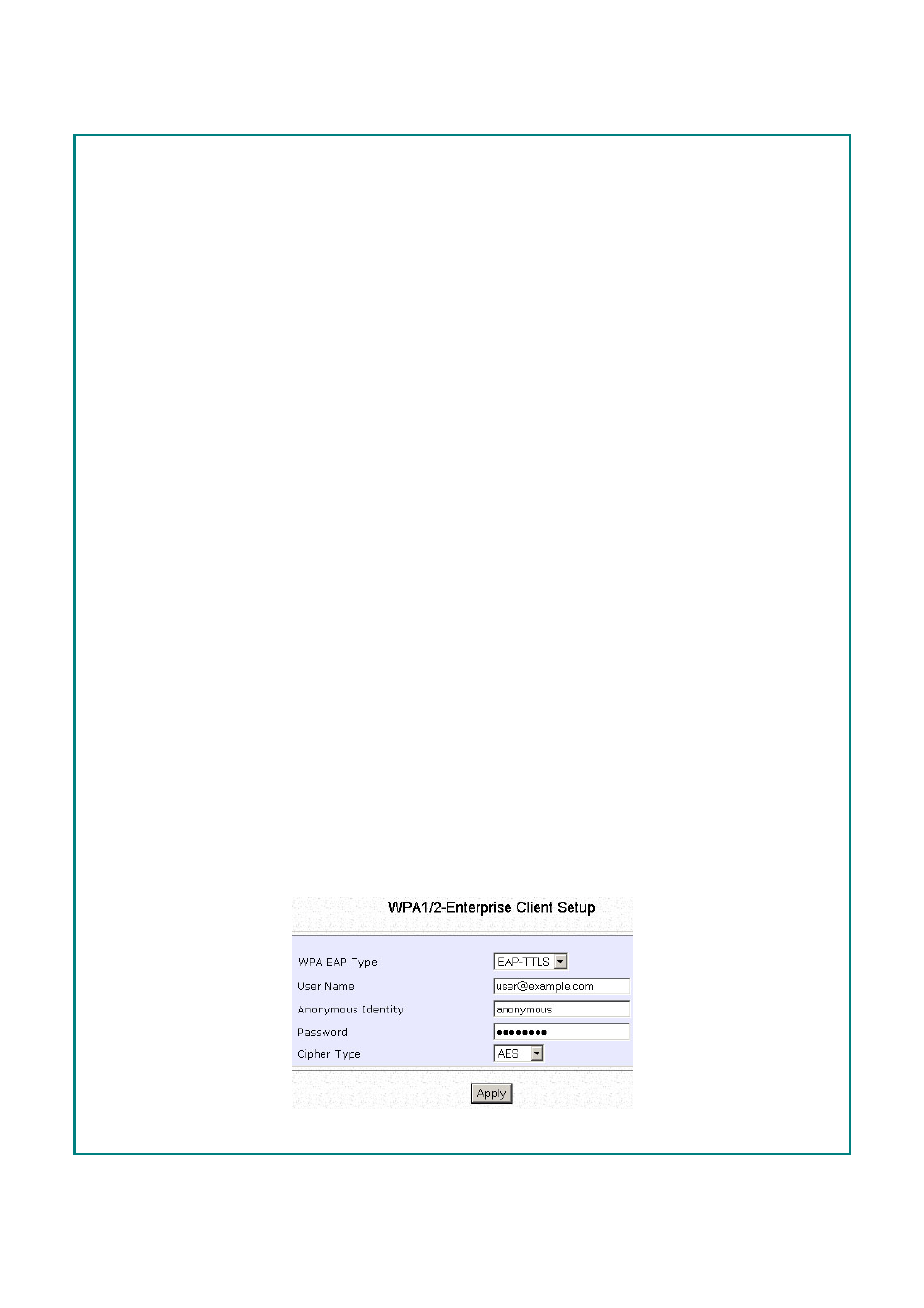
WPA EAP Type.
Step 2:
Both
E
E
A
A
P
P
-
-
T
T
T
T
L
L
S
S
(Extensible Authentication Protocol - Tunneled Transport Layer
Security) and
E
E
A
A
P
P
-
-
P
P
E
E
A
A
P
P
(Protected Extensible Authentication Protocol) support
identity hiding. In the WLAN, the access point generates an identity request. To
preserve anonymity, the client responds with only enough information to allow the
RADIUS server to process the request.
I
I
f
f
u
u
s
s
i
i
n
n
g
g
EAP-TTLS
W
W
P
P
A
A
E
E
A
A
P
P
T
T
y
y
p
p
e
e
:
:
• Enter the
U
U
s
s
e
e
r
r
N
N
a
a
m
m
e
e
.
• Enter the
A
A
n
n
o
o
n
n
y
y
m
m
o
o
u
u
s
s
I
I
d
d
e
e
n
n
t
t
i
i
t
t
y
y
attribute for EAP-TTLS.
• Enter the
P
P
a
a
s
s
s
s
w
w
o
o
r
r
d
d
.
• Enter the
C
C
i
i
p
p
h
h
e
e
r
r
T
T
y
y
p
p
e
e
.
For WPA-Enterprise
Set the
C
C
i
i
p
p
h
h
e
e
r
r
T
T
y
y
p
p
e
e
to
T
T
K
K
I
I
P
P
.
WPA replaces WEP with a strong encryption technology called Temporal Key
Integrity Protocol (TKIP) with Message Integrity Check (MIC).
For WPA2- Enterprise
Set the
C
C
i
i
p
p
h
h
e
e
r
r
T
T
y
y
p
p
e
e
to
A
A
E
E
S
S
.
Advanced Encryption Standard (AES) is a symmetric 128-bit block data encryption
technique. It is a requirement of WPA2 under the IEEE 802.11i standard.
For WPA- Enterprise -AUTO
Set the
C
C
i
i
p
p
h
h
e
e
r
r
T
T
y
y
p
p
e
e
to
A
A
u
u
t
t
o
o
to allow the access point to automatically detect the
cipher type to use.
