Generate https certificate – Rockwell Automation 1756-EN2TSC EtherNet/IP Secure Communication User Manual User Manual
Page 23
Rockwell Automation Publication ENET-UM003B-EN-P - August 2013
23
Get Started
Chapter 2
Some web pages use both .asp, form, and URL elements. In such cases, each
element is represented by a separate access limit. For example, the ‘Edit Access
Limits’ web page is composed of the following:
• editlimits.asp to generate a list of access limits
• /rokform/AddAccessLimits to add or update an existing limit
• /rokform/DeleteAccessLimit to delete an existing limit
Generate HTTPS Certificate
You can generate a new HTTPS certificate if needed. This is optional as the
module automatically generates a certificate when the module is turned on for
the first time after factory reset.
• The certificate generated at first powerup of the module is not bound to
any specific IP address. This can cause the browser to report a certificate
error and you can decide whether to generate a new certificate.
• If you generate a new certificate and then later change the IP address of the
module, the current certificate becomes invalid. Generate a new certificate
that uses the new IP address; otherwise the browser reports a certificate
error.
A newly-generated certificate has an advantage that the module uses the current
IP address. This can limit web browser certificate warnings, even though the
browser can still report an error due to a self-signed certificate.
You can specify the validity period of the certificate you generate. The period is
set from the current time on the module to a specified end time. Synchronize the
real-time clock on the Logix5000 controller with the current time. Generating a
short-validity period without the clock being synchronized can generate an
outdated certificate.
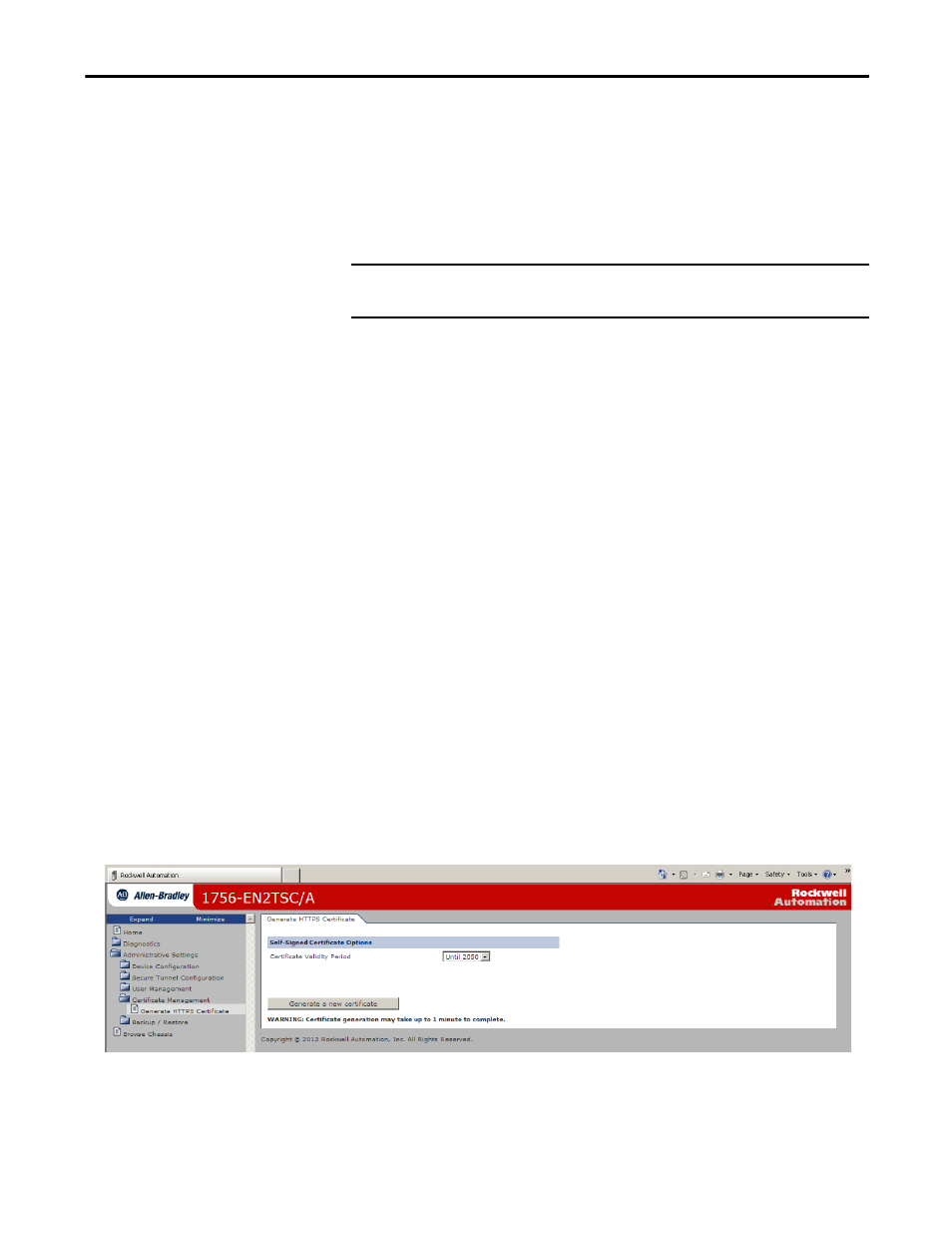
To generate a new certificate, choose Administrative Settings > Certificate
Management > Generate HTTPS Certificate.
Use the pull-down menu to choose a valid length of time for the certificate to be
enabled.
IMPORTANT
Limiting access to the .asp file is not enough to limit its functionality. If
unsecured, a form handler could be used with externally prepared request.
