Chapter 1 designing security in the gsa, Overview – Google Search Appliance Security User Manual
Page 4
4
Chapter 1 Designing Security in the GSA
Overview
Enterprise search projects integrate data from different sources to enable users to find information easily.
In most cases, especially in intranet projects, access to documents in source applications is protected. To
provide relevant and secure results to users, the corporate search engine must apply the same
authorization policies as the sources where documents are stored.
The search appliance acts as a hub, where content coming from different sources is indexed to facilitate
access to the information. The search appliance must rely on the same security protocols as those that
the applications use. If your enterprise search project includes indexing protected content, you need to
invest time during the design phase to model the security relationships between your content sources and
the Google Search Appliance.
Before actual implementation of security in the GSA begins, take time to understand the overall
integration scenario and reference architecture. Because there are probably internal security policies and
protocols already established in your organization, you have to explore the best options for implementing
security in the search environment. And you have to design a security model for the search appliance that
will be consistent with all project phases.
This chapter explains the key processes of GSA’s secure search, and how you should approach the
overall design.
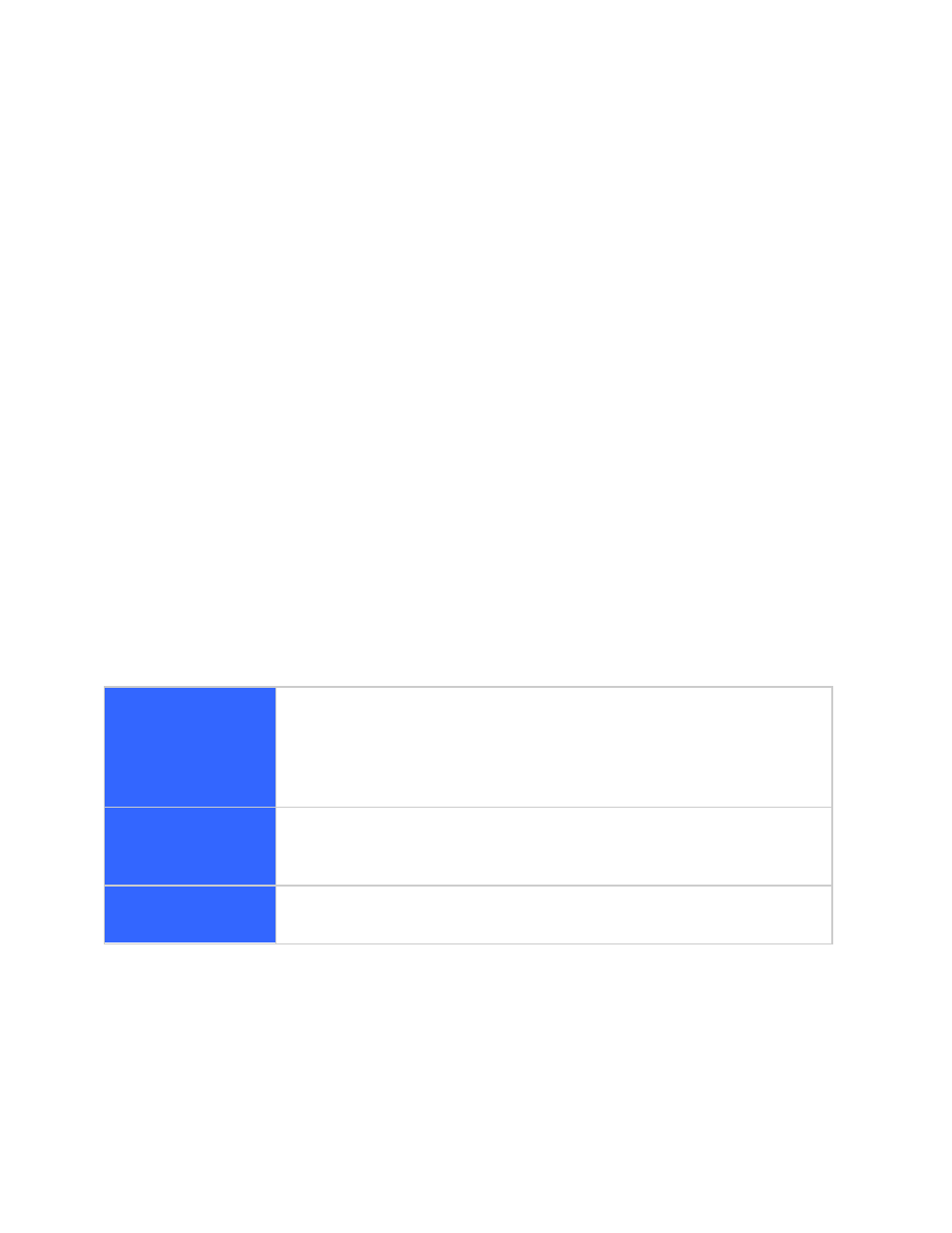
We can divide the secure search into three distinct but related processes:
Secure Content
Acquisition
The mechanism GSA uses to acquire the secured content source.
GSA has to pass through the protection that the content source puts
in place in order to gain access. It’s an integral part of content
acquisition, but it has to be considered as part of the security
design.
Serve Time
Authentication
The mechanism used by GSA to identify end users. It could be one
or more of the Internet authentication protocols. Note that this is the
communication between GSA and the client (browser).
Serve Time
Authorization
The process that GSA employs to check whether a search user has
access to the search results.
Content Acquisition
Once you have modeled the information about your content sources, you can design the authentication
mechanism(s) the GSA will use to integrate with each secure source. This is the process portion of the
project design phase that models the integration between the search appliance and an organization’s
systems. The search appliance permits the use of several authentication mechanisms simultaneously to
