Saml – Google Search Appliance Security User Manual
Page 28
28
SAML
The search appliance supports
an XML based protocol for an external identity provider. There
might be cases where you will need to develop a custom SAML IdP. Note that building a SAML IdP from
scratch is time consuming. You should start with an existing code base—such as
also provides an open source project
for silent authentication with Windows technologies.
Bear in mind that there are two different ways to set up SAML authentication with the search appliance:
●
where the browser is used as the main communication mechanism
between the GSA (Service Provider) and the Identity Provider (your SAML server).
●
which requires a trust mechanism between the GSA (Service Provider) and
the Identity Provider (your SAML server).
It’s not the intention of this document to guide you through setting up this configuration, as this is already
described in the GSA documentation, but the following table contains tips about which SAML binding to
use.
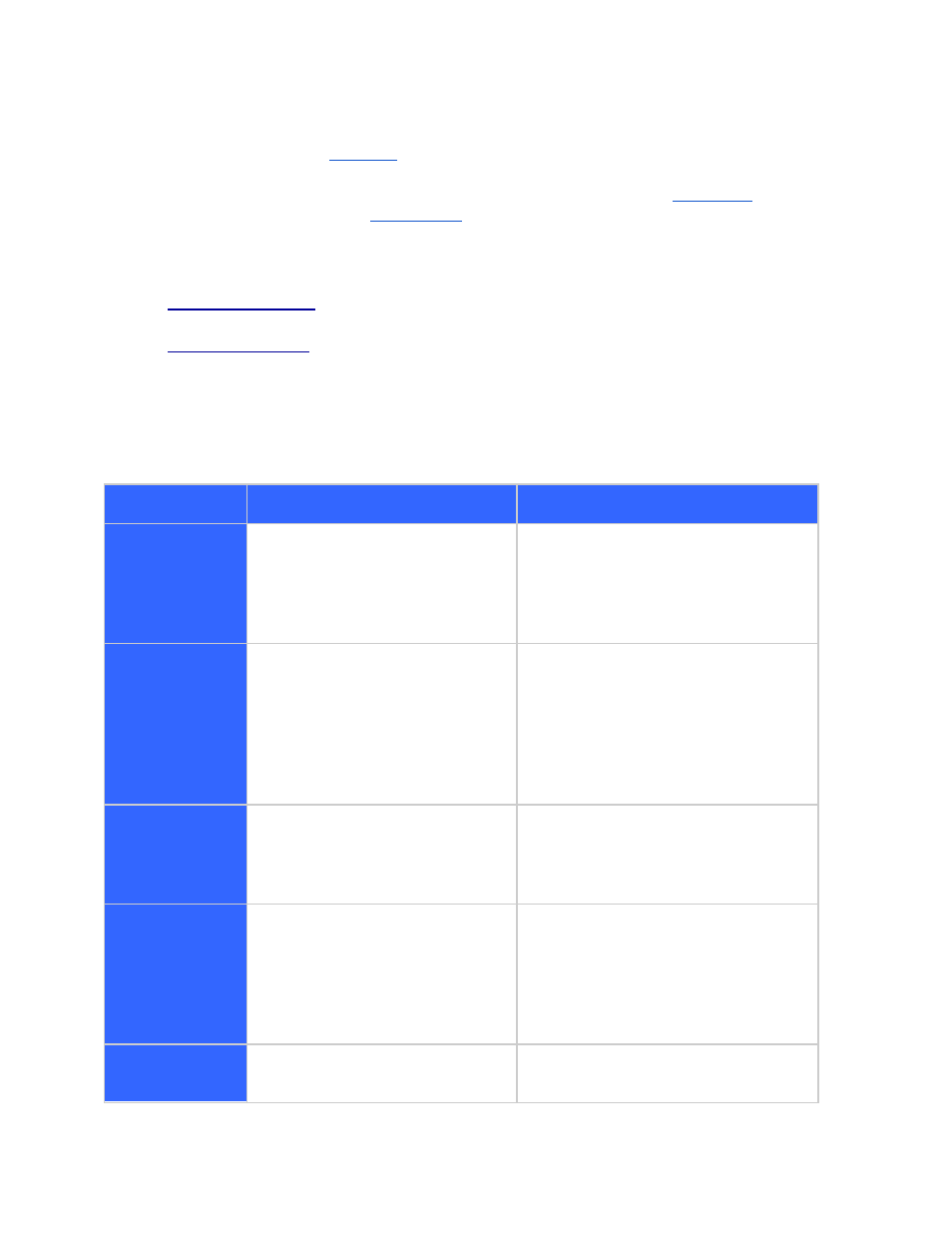
SAML HTTP Artifact Binding
SAML HTTP POST Binding
Requirements
Multiple transparent redirections
are required. Trust between the
browser and the GSA/SAML
Identity Provider is required.
Apart from the trust between the
browser and the other servers, it also
requires you to create a trusted link
between the GSA and the Service
Provider.
Configuration
Secure HTTP connections from the
client with GSA and Identity
Provider are desirable. An additional
URL has to be configured on the
GSA (Artifact Resolver URL) to
provide final authentication
information to the GSA.
Apart from having SSL connections
between client and servers, it also
requires you to configure certificates
between the GSA and the Identity
Provider. This is used for the GSA to get
the authentication information directly
from the Service Provider.
Public key
infrastructure
It’s less complex from a security
perspective as it doesn’t necessarily
require you to have a PKI (Public
Key Infrastructure) solution.
It does require issuing trusted
certificates so a PKI infrastructure is
needed. Take into account this can also
be done by using OpenSSL solution.
High availability
It’s more complex to provide a
Highly Available solution for the
GSA and the Identity Provider due
to the multiple browser redirections
and required persistence of the
artifact between multiple calls.
High Availability can easily be
implemented.
SAML identity
provider
If you have to develop a SAML
Identity Provider based on Artifact
Developing a SAML Identity Provider
from scratch could be simpler, but it
