Google Search Appliance Security User Manual
Page 12
12
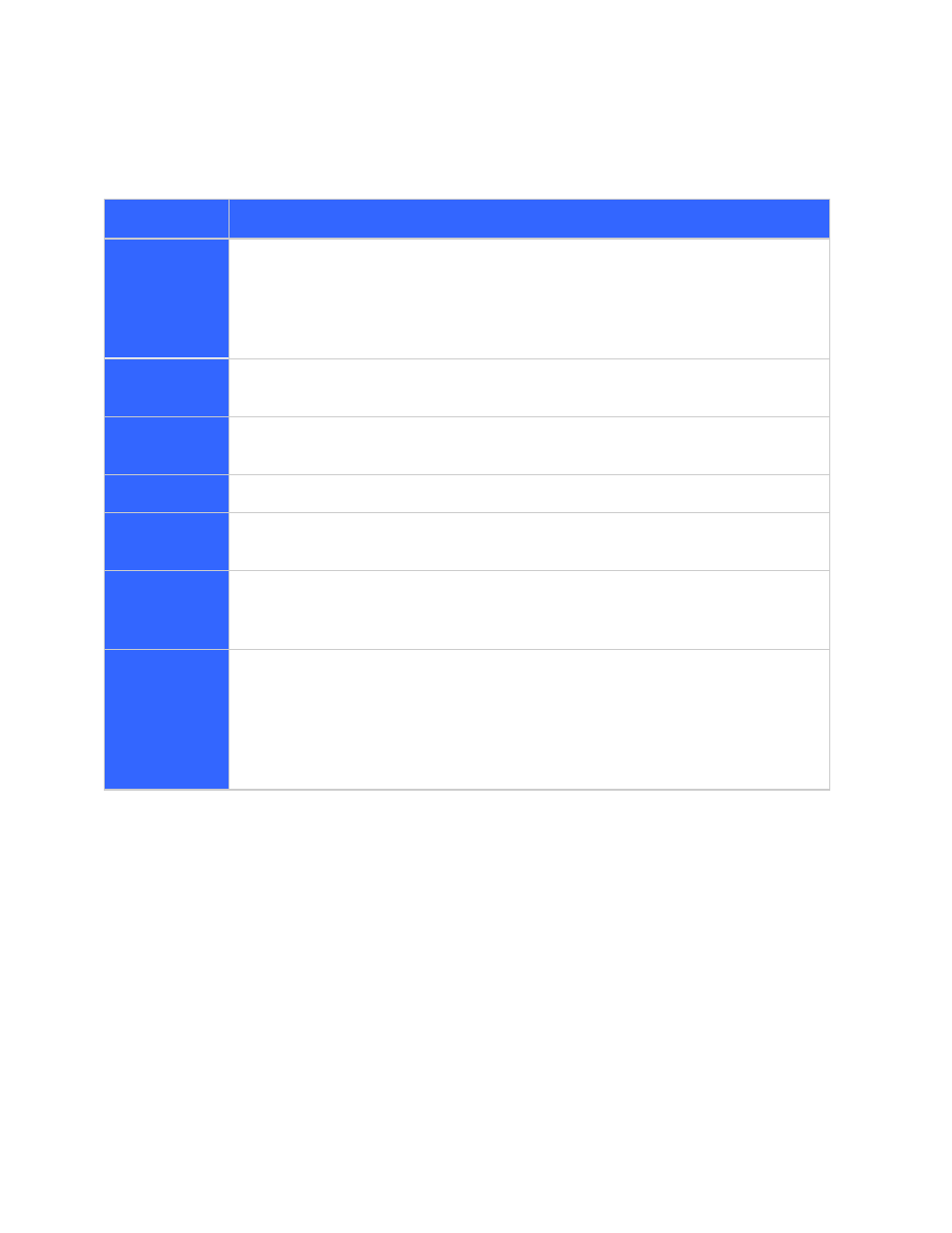
All authorization mechanisms require User ID except Head Requests. The following table lists
authentication mechanisms that would result in a User ID:
Authentication mechanisms when user ID is required
HTTP
Basic/NTLM
It is listed as HTTP Basic/NTLM. However, these are the authentication protocols
used to verify the user credentials which happens between GSA and a back end
server. To the end user, it is forms authentication. After the user credentials are
verified by the configured “Sample URL”, the User ID entered by the user is treated
as the verified ID.
Client
Certificate
Certificate’s DN is passed as the verified ID.
Kerberos
The Windows user ID extracted from the Kerberos ticket is used as the verified
user ID.
SAML AuthN
The “Subject” passed by the SAML IDP is the verified ID.
LDAP
Authentication
User ID verified by the LDAP server is used as the verified ID.
Forms Authn
with Cookie
Cracking
User ID is passed back to the GSA by the Cookie Cracker. This involves some
coding where a simple dynamic web page needs to be implemented to pass this.
Connectors
Connector Framework provides the authentication SPI which returns a trusted User
ID. However, it must be implemented by the connector, which is optional. Not every
connector available provides authentication. Connector implementers can even
choose to require a password. For example, The File system connector 2.x requires
both the username and password in order to perform late binding authorization when
there are deny rules on documents.
All the authentication mechanisms above can be mixed with ACLs, Connector and SAML authorizations.
You can pick the one that fits customer requirements and is easiest to implement (also take into
consideration any silent authentication requirements).
For Head Request authorization, you cannot pick just any possible authentication mechanism as the head
requests are sent from the GSA to the content source, not by the client’s browser to the GSA. Depending
on the authentication protocol used by the content source, different credentials must be obtained by the
GSA during the user authentication process.
