Authentication, Purpose of the google search authentication spi, How the authentication spi works – Google Search Appliance Authentication/Authorization for Enterprise SPI Guide User Manual
Page 6
Google Search Appliance: Authentication/Authorization for Enterprise SPI Guide
6
Authentication
Purpose of the Google Search Authentication SPI
When implemented, the Authentication SPI allows search users to authenticate to the search appliance.
It is designed to allow customers to integrate the search appliance into an existing access control
infrastructure. Instead of authenticating search users itself, the search appliance redirects the user to
an Identity Provider (IdP), a customer-implemented server, where the actual authentication takes place.
The IdP then redirects or posts the user back to the search appliance, while passing information that
includes the identity of the search user. The protocol that governs this communication between the
search appliance, the browser, and the customer’s IdP is SAML 2.0, an XML-based standard. Specifically,
the two SAML bindings (how SAML protocol messages are communicated) an IdP could employ to
return a response are HTTP Artifact and HTTP POST. Regardless of the binding used for the response, the
HTTP Redirect binding is used for sending the request.
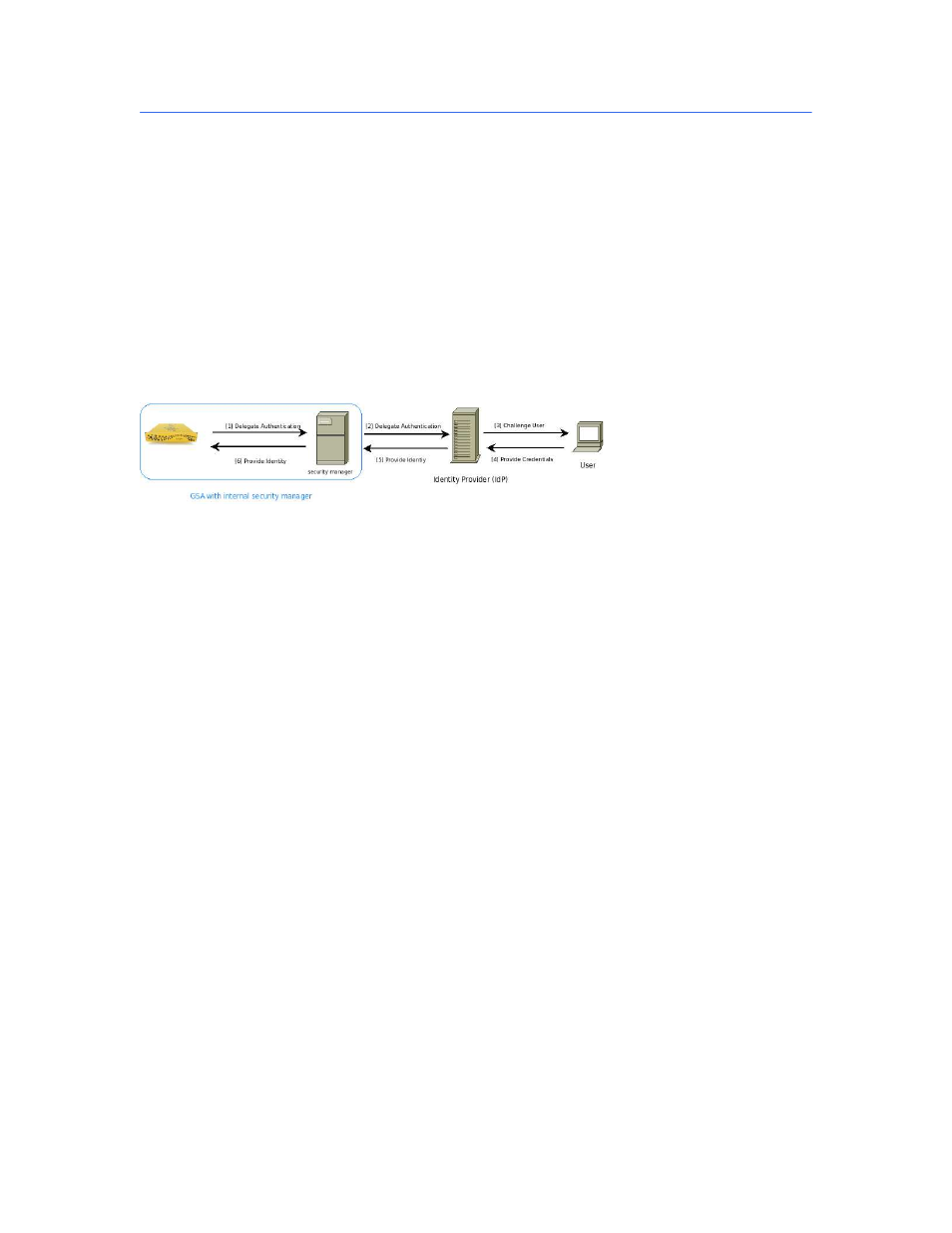
Figure 1: The search appliance communicates through an Identity Provider to authenticate users’ access
to intranet web pages.
How the Authentication SPI Works
The Authentication SPI exposed by the search appliance is the SAML 2.0 standard; specifically, the “Web
Browser SSO Profile.” The Web Browser SSO profile makes use of the “Authentication Request
Protocol,” a request-response protocol. The search appliance sends a SAML
to the customer’s Identity Provider, and the Identity Provider responds with a SAML
message that contains an
are transferred between the search appliance and the customer’s Identity Provider, via the browser,
using the “HTTP Redirect + Artifact” or “HTTP Redirect + POST” bindings.
The messaging flow for the Artifact and POST bindings are different and are discussed separately:
Authentication using Artifact and Post Binding
•
A user enters a search query into a browser.
•
The search appliance checks for an existing user session. If it finds a session running, the search
appliance supplies the search results and the sequence is complete. If no session exists, an
Redirect binding.
•
The HTTP Redirect binding redirects the browser to the Identity Provider with a SAML message sent
as a URL query inside the SAMLRequest string parameter.
•
The Identity Provider authenticates the search user. The IdP can perform this authentication in any
way: HTML form, checking an already established session cookie, NTLM, Kerberos, certificate, 2-
factor, and so on.
