Http artifact binding – Google Search Appliance Authentication/Authorization for Enterprise SPI Guide User Manual
Page 12
Google Search Appliance: Authentication/Authorization for Enterprise SPI Guide
12
After Authentication, the IdP can either use Artifact Binding or POST Binding depending on what
mechanism its setup for.
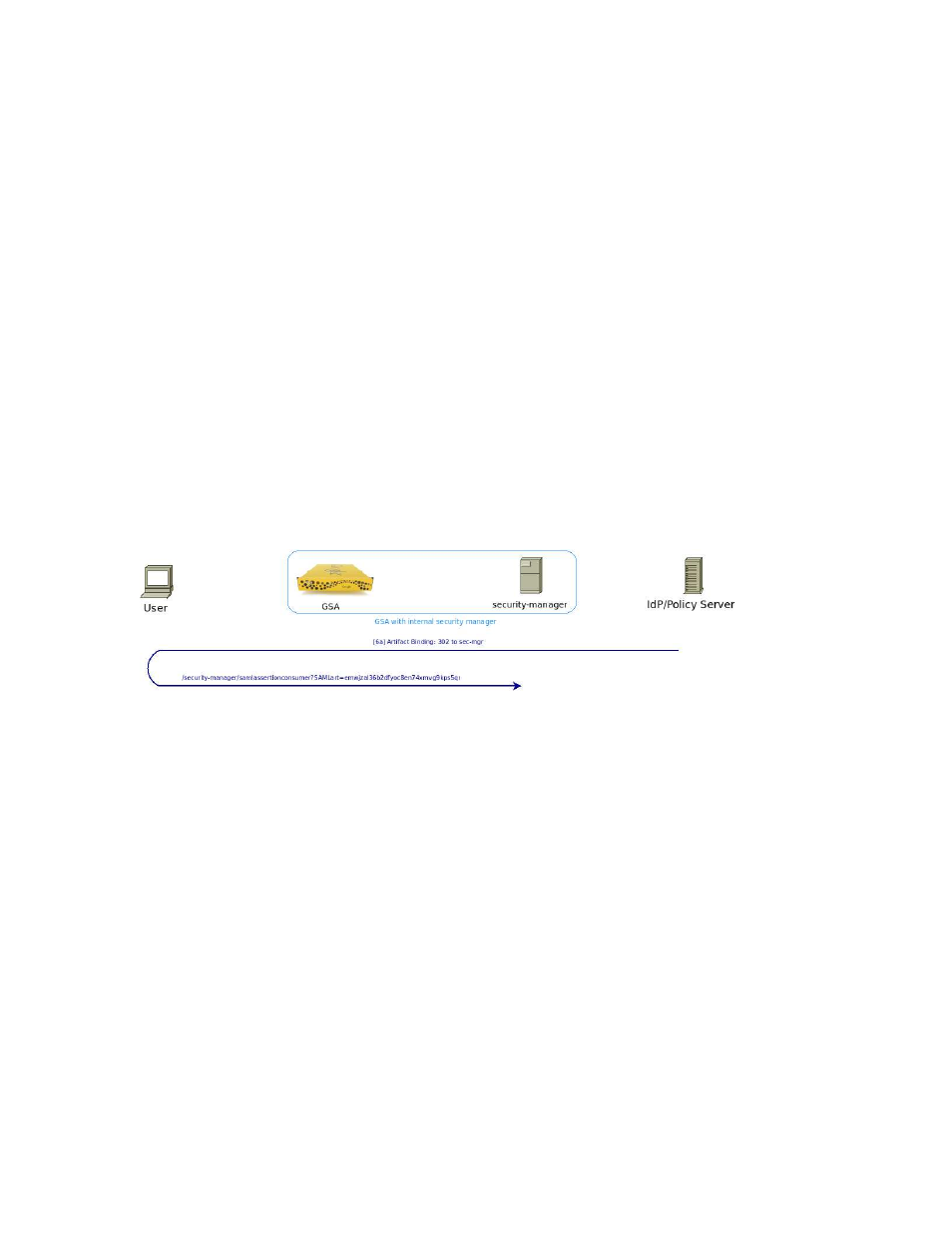
HTTP Artifact Binding
[6a] With Artifact Binding, the IdP generates a random-looking string called an artifact, then associates it
with the response from the authentication step. This association is used later to look up the response.
Now the IdP redirects the user back to the security manager (/security- manager/
samlassertionconsumer) and passes on this artifact in the GET query string. How the IDP determines
the host/port of the security manager is up to the IdP. The Referer HTTP header MUST never be used to
determine the Google Search Appliance or security manager host/URL. An IdP can simply hard-code the
SecurityManager URL in code or in a config file. Although the AssertionConsumerServiceURL does
properly indicate the URL of the security manager, per specifications, if the request isn’t integrity
protected, an IdP MUST not rely on its value. From the SAML Core 2.0 Specifications:
AssertionConsumerServiceURL [Optional]:
Specifies by value the location to which the Response message MUST be returned to
the requester. The responder MUST ensure by some means that the value specified is
in fact associated with the requester.
One way to derive the SecurityManager URL from the &SAMLRequest= is to store the URL along with the
I02BQQ2PYJSJT/security-manager which could be stored internally on the IdP in a lookup table
associated with URL https://gsa.yourdomain.com/security-manager/samlassertionconsumer.
Figure 4: Idp Redirecting with the Artifact Profile.
HTTP/1.x 302 Found
Date: Fri, 16 Jul 2010 02:05:06 GMT
Content-Length: 122
Content-Type: text/html
Location: https://gsa.yourdomain.com/security-manager/
samlassertionconsumer?
SAMLart=emwjzal36b2dfyoc8en74xmvg9kps5qr
Server: CherryPy/3.1.0
