Using the web-based advanced user interface, Securing your wi-fi, Network – Belkin f5d7230-4 User Manual
Page 52: Wired equivalent privacy (wep), Bit wep
50
Using the Web-Based Advanced User Interface
50
Securing your Wi-Fi
®
Network
Here are a few different ways you can maximize the security of your
wireless network and protect your data from prying eyes and ears. This
section is intended for the home, home office, and small office user.
At the time of this User Manual’s publication, there are four encryption
methods available.
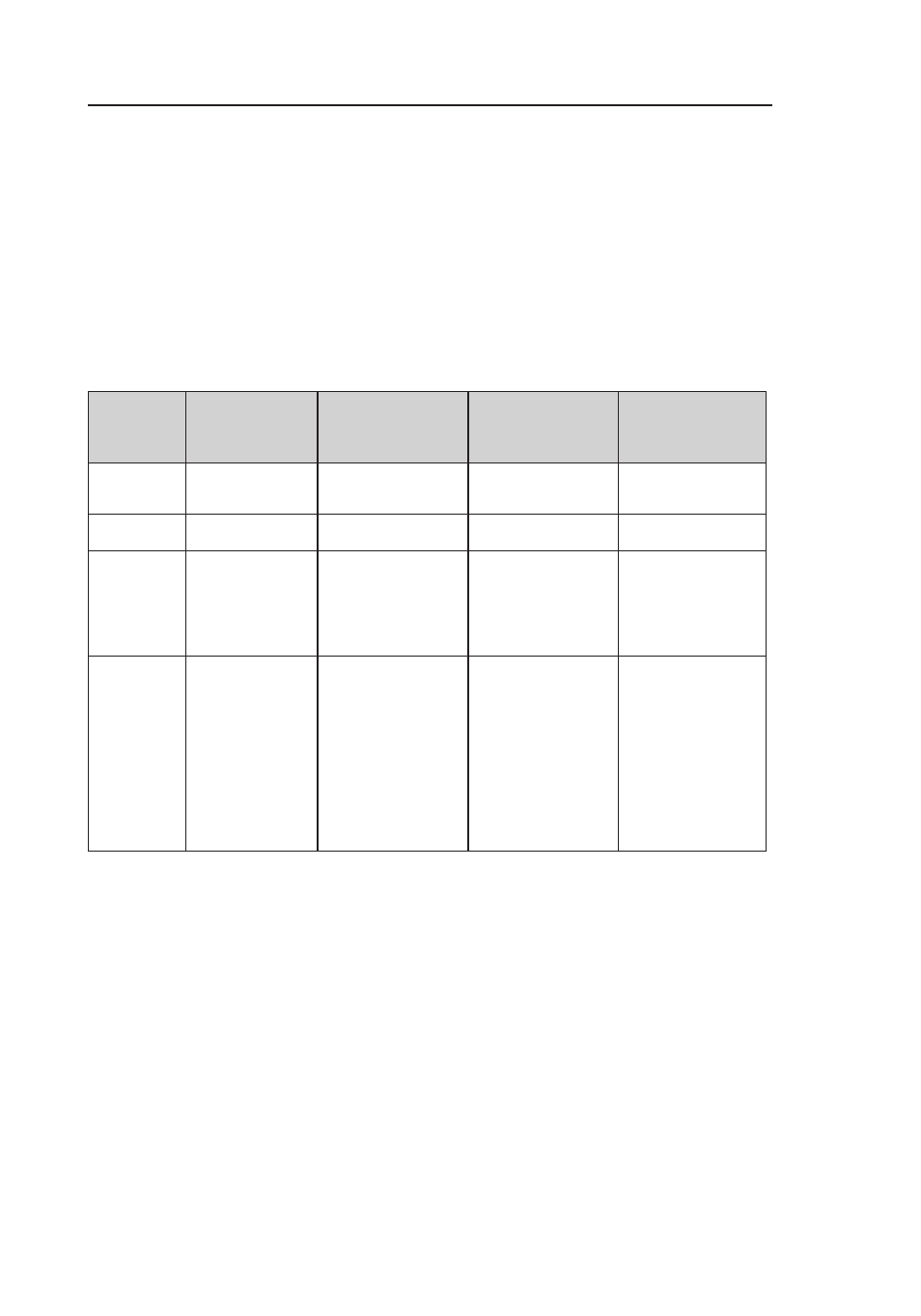
Name
64-Bit Wired
Equivalent
Privacy
128-Bit Wired
Equivalent
Privacy
Wi-Fi Protected
Access-TKIP
Wi-Fi Protected
Access 2
Acronym
64-bit WEP
128-bit WEP
WPA-TKIP/AES
(or just WPA)
WPA2-AES
(or just WPA2)
Security
Good
Better
Best
Best
Features
Static keys
Static keys
Dynamic key
encryption
and mutual
authentication
Dynamic key
encryption
and mutual
authentication
Encryption
keys based
on RC4
algorithm
(typically
40-bit keys)
More secure
than 64-bit
WEP using a
key length of
104 bits plus
24 additional
bits of system-
generated data
TKIP (Temporal
Key Integrity
Protocol)
added so
that keys are
rotated and
encryption is
strengthened
AES (Advanced
Encryption
Standard)
does not
cause any
throughput loss
Wired Equivalent Privacy (WEP)
WEP is a common protocol that adds security to all Wi-Fi-compliant
wireless products. WEP was designed to give wireless networks the
equivalent level of privacy protection as a comparable wired network.
64-Bit WEP
64-bit WEP was first introduced with 64-bit encryption, which includes
a key length of 40 bits plus 24 additional bits of system-generated data
(64 bits total). Some hardware manufacturers refer to 64-bit as 40-bit
encryption. Shortly after the technology was introduced, researchers
found that 64-bit encryption was too easy to decode.
