Any allowed traffic from other zones, 1 of 2 – Avaya 3.7 User Manual
Page 306
Firewall rules template
306 Avaya VPNmanager Configuration Guide Release 3.7
●
The destination is Public and the services are FTP, SSH, Telnet, HTTP, HTTPS, POP3,
IMAP, or ICMPechorequest.
All other incoming traffic is blocked.
Outgoing traffic to the semi-private zone that is allowed includes
●
Any allowed traffic from other zones
●
VPN traffic
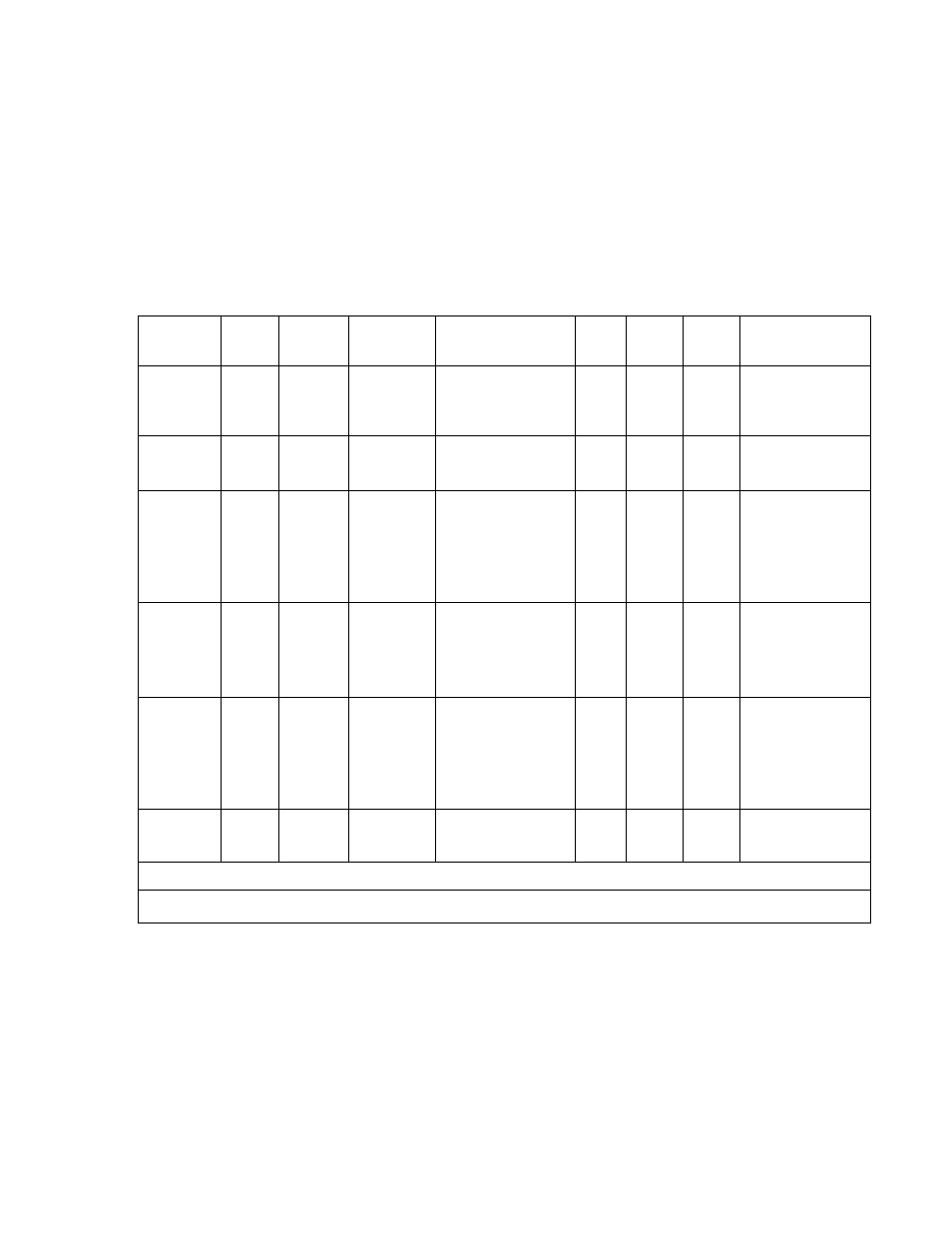
Table 37: Semi-private high security firewall rules
Rule Name
Action
Source
Destination
Service
Direc
tion
Zone
Keep
State
Keep State
InBoundSe
miPrivateV
PNAccess
Permit
Any
SemiPrivate
IP
PublicIP
IKE_IN
IPSEC_NAT_T_IN
AH/ESP
ICMPDestUnreach
In
SemiP
rivate
No
Permit incoming
VPN and ICMP
unreachable
InBoundSe
miPrivatePi
ngAccess
Permit
Any
SemiPrivate
IP
PublicIP
ICMPEchoReq(PING)
In
SemiP
rivate
Yes
Permit incoming
PING
InBoundSe
miPrivateto
DMZAcces
s
Permit
Any
DMZNet
ICMPEchoReq(PING)
FTP-Ctrl/PassiveFTP
SSH/TELNET
HTTP/HTTPS
DNS-TCP/DNS-UDP
POP3/IMAP/SMTP
NNTP
In
SemiP
rivate
Yes
Permit incoming
services to DMZNet
InBoundSe
miPrivateD
enyAccess
Deny
Any
DMZNet
PrivateNet
Manageme
ntNet
SemiPrivate
IP
Any
In
SemiP
rivate
No
Deny traffic to
PrivateNet,
ManagementNet
and DMZNet
InBoundSe
miPrivateto
PublicAcce
ss
Permit
Any
Any
ICMPEchoReq(PING)
FTP-Ctrl/PassiveFTP
SSH/TELNET
HTTP/HTTPS
DNS-TCP/DNS-UDP
POP3/IMAP/SMTP
NNTP
In
SemiP
rivate
Yes
Permit clear traffic
to Public network/
VPN traffic with
Public IP as tunnel
endpoint
InBoundSe
miPrivateBl
ockAll
Deny
Any
Any
Any
In
SemiP
rivate
No
Deny the rest of
traffic
1 of 2
