ZyXEL Communications 2WG User Manual
Page 53
ZyWALL 2WG Support Notes
All contents copyright (c) 2006 ZyXEL Communications Corporation.
53
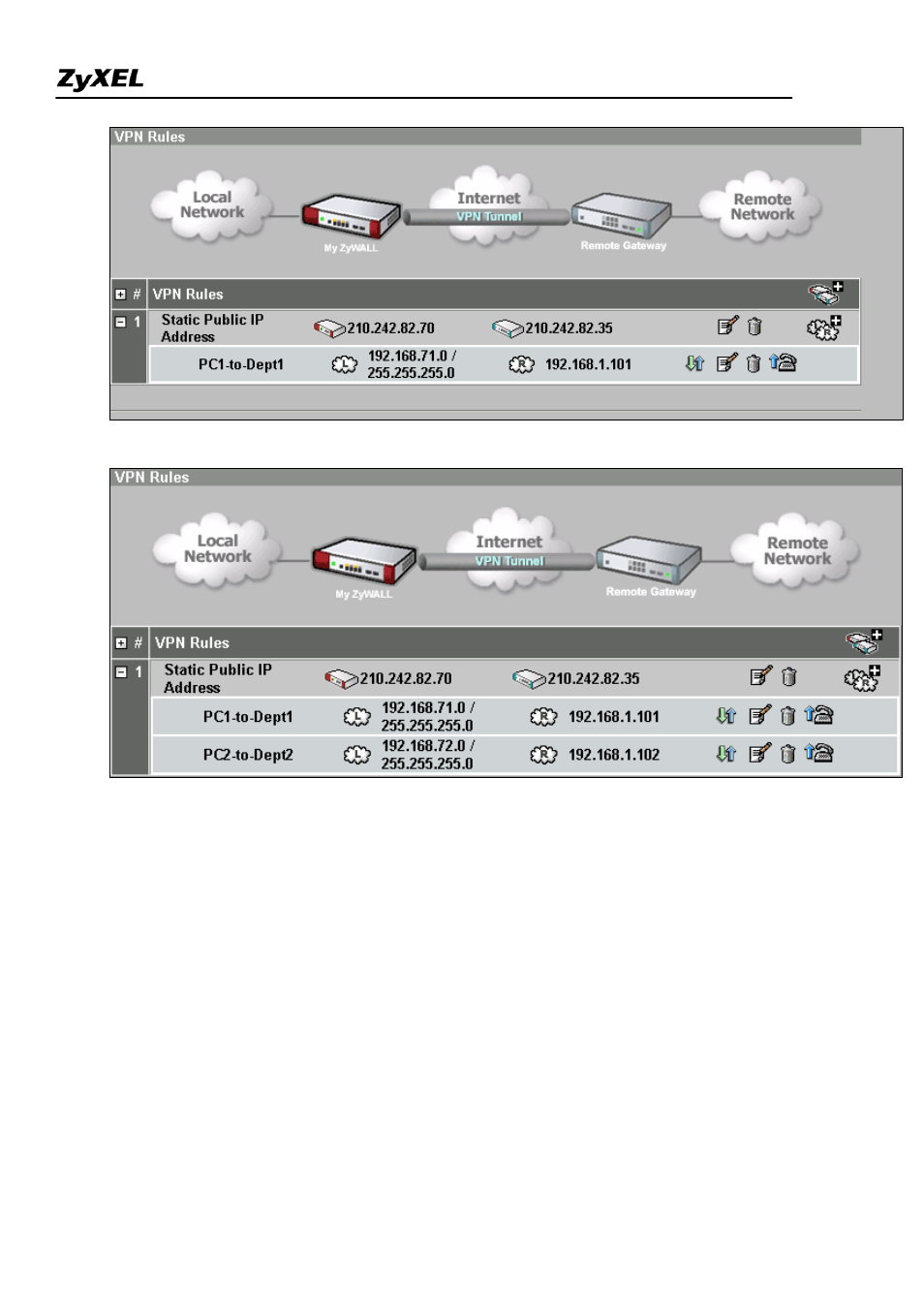
18) Follow the same procedures as step 10~16 to add 2
nd
Network Policy, PC2-to-Dept2.
Finish
Using Certificate for Device Authentication
IKE must authenticate the identities of the systems using the Diffie-Hellman algorithm. This process is
known as primary authentication. IKE can use two primary authentication methods:
1) Digital Signatures
2) Pre-shared keys
Digital signature and public-key encryption are both based on asymmetric key encryption and require a
mechanism for distributing public keys. This is usually done using security certificates and a Public Key
Infrastructure (PKI).
If certificate (Digital Signatures) is used for authentication, there are five available types of identity: IP,
