ZyXEL Communications 2WG User Manual
Page 46
ZyWALL 2WG Support Notes
All contents copyright (c) 2006 ZyXEL Communications Corporation.
46
4) Configure the DDNS entry under DNS-> DDNS and bind it to a WAN interface.
5) Under Gateway Policy menu, select the DDNS entry from drop-down list and use it as My Domain
Name.
6) Configure the DDNS entry in Remote Gateway Address on peer VPN gateway.
7) Both DNS and E-mail can be used as the Local ID & Peer ID for authentication.
Note: If Hi-Available (HA) for incoming VPN HA is necessary, enable the HA option while configure the
DDNS entry under DNS-> DDNS ZyWALL will update its DDNS entry with another WAN interface
when the specified WAN interface is not available. Therefore, the next coming VPN connection will go
through second WAN interface.
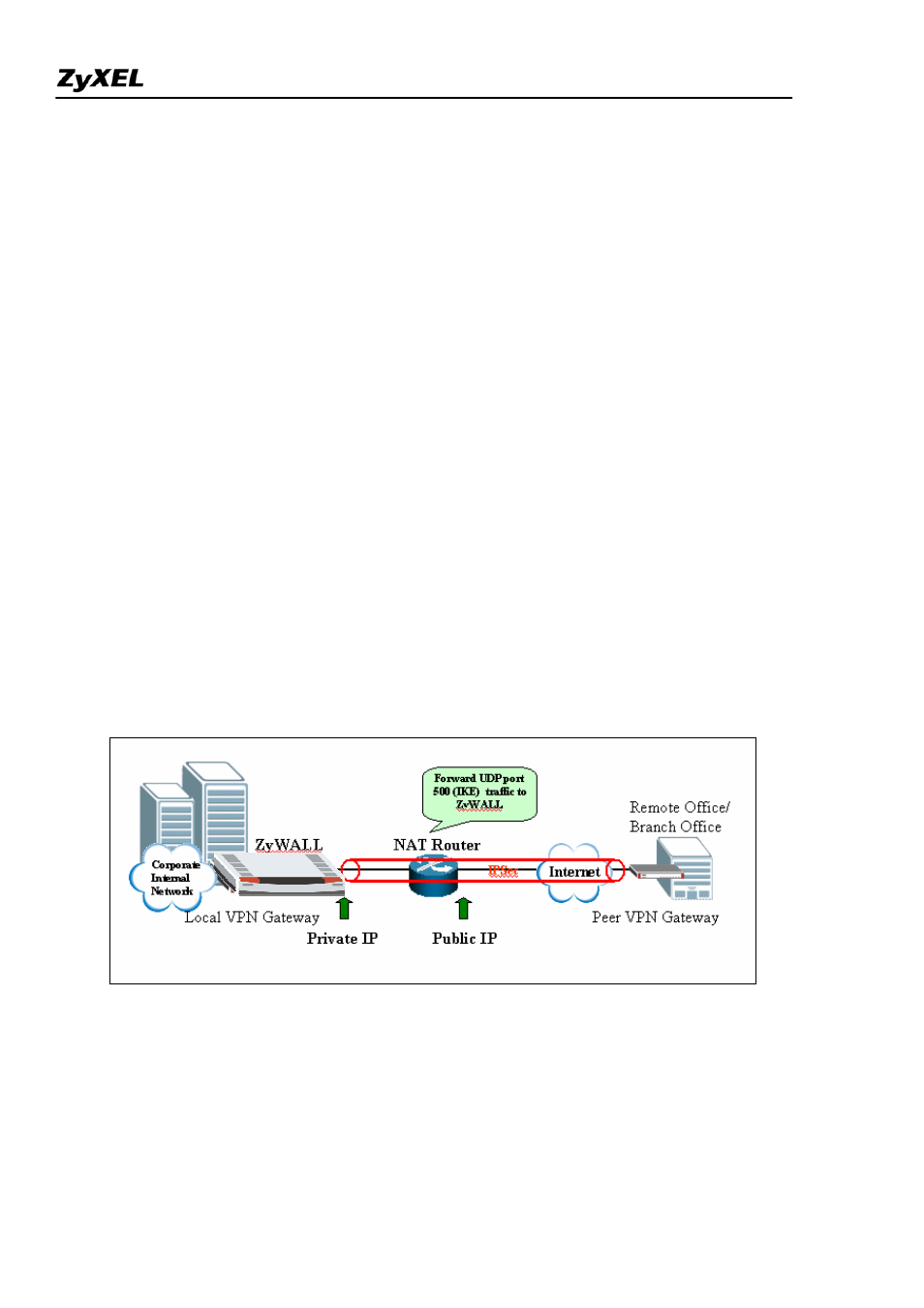
Configure ZyWALL behind NAT Router
This section describes an example configuration ZyWALL behind NAT Router (Internet Gateway).
NAT routers sit on the border between private and public (Internet) networks, converting private
addresses in each IP packet into legally registered public ones. NAT is commonly supported by Internet
access routers that sit at the network edge. However, IPSec is NAT-sensitive protocol which means
modification on IPSec traffic may cause failure of VPN connection.
By far the easiest way to combine IPSec and NAT is to completely avoid these problems by locating
IPSec endpoints in public address space. This can be accomplished in two ways:
1) Perform NAT on a device located behind IPSec gateway
2) Use an IPSec gateway for both IPSec (VPN) and NAT (Internet Access).
However, in some situation, it is inevitable to locate IPSec gateway in public IP address and it must be
