Konica Minolta BIZHUB 920 User Manual
Page 84
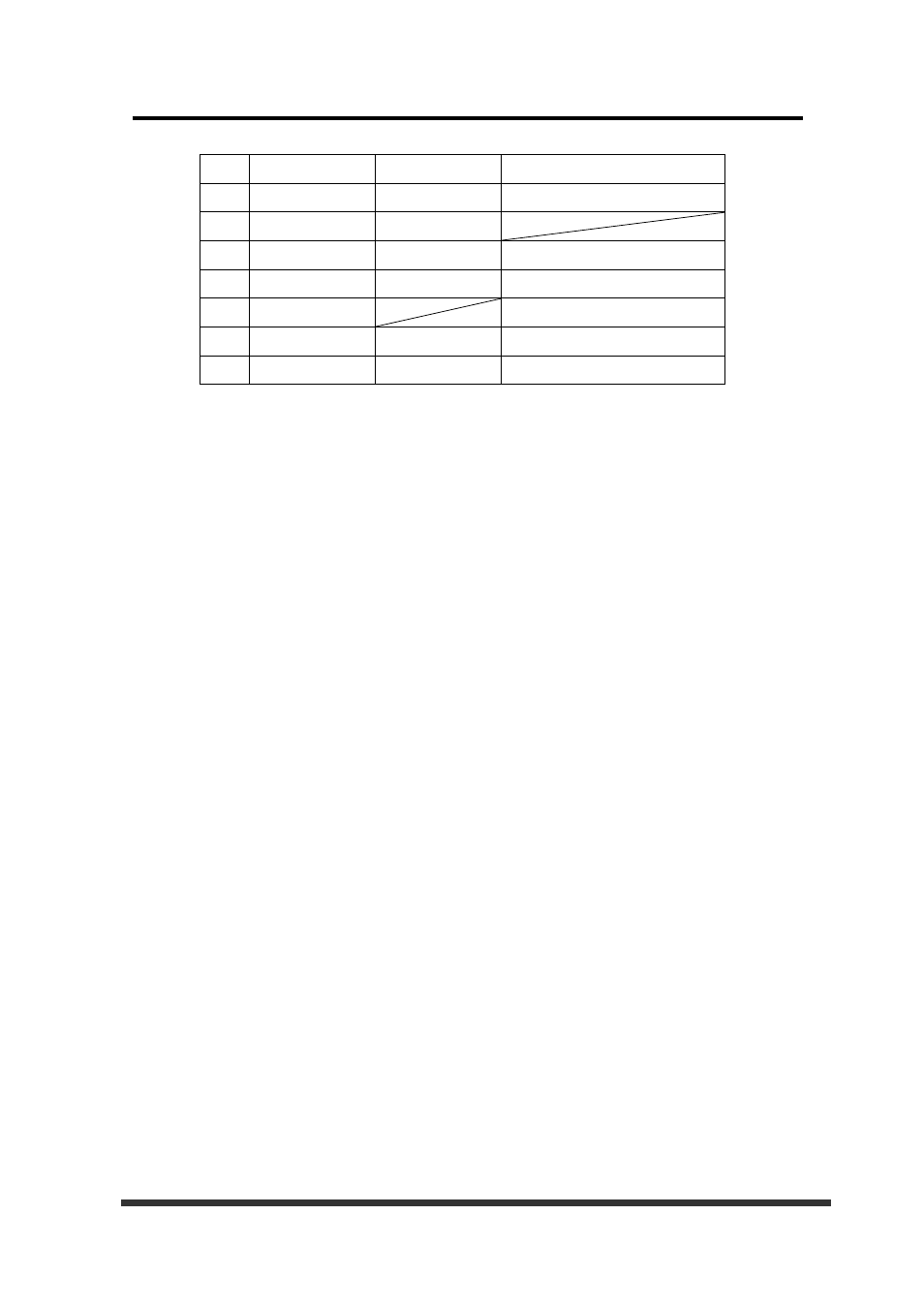
22 FMT_MSA.1 FPT_RVM.1 FMT_MOF.1
23 FMT_MSA.3 FPT_RVM.1 FMT_MOF.1
24 FMT_MOF.1 FPT_RVM.1
25 FMT_SMF.1 None
FMT_MOF.1
26 FMT_SMR.1 None
FMT_MOF.1
27 FPT_RVM.1
FMT_MOF.1
28 FPT_STM.1 None
None
29 FDP_MTD.1 FPT_RVM.1 FMT_MOF.1
When the management function and CE function of the TOE is used, the administrator and CE
execute the identification and authentication (FIA_UID.2, FIA_UAU.2, FIA_UAU.7, FIA_AFL.1).
The document data of User BOX is accessed according to the access control (FDP_ACC.1[1] [2]
and FDP_ACF.1[1][2]).
The audit data is always captured. (FAU_GEN.1 and FAU_STG.4)
Only the administrator can refer the audit data.(FAU_SAR.1, FAU_SAR.2, and FAU_STG.1)
Only the user who is applicable to each data can operate the miscellaneous TSF data and
administrator data.(FAU_SAR.2, FMT_MTD.1[1]-[5], FMT_MSA.1, FMT_MSA.3, FMT_
MOF.1, and FDP_MTD.1)
The detour is prevented because the avobe mentioned matters are certainly executed in FPT_
RVM.1.
The prevention of deactivation in TSF is realized by making the security reinforcement mode to
be valid in FMT_MOF.1.
In this TOE, the access control is only for the User BOX of HDD1.
The unauthorized subject does not exist because the access control to User BOX is limited to the
process through the operation panel. Therefore, FPT_SEP.1 is unnecessary because there is no room
for the unauthorized subject to enter.
8.2.4. Consistency of Security Function Strength to Security Objectives Policies
This TOE assumes the attack capability of general user to be low level in “2. TOE Description”,
and describes “operate from the operation panel” or “connect unauthorized reading device with
HDD” in “3. TOE Security Environment”, namely, the especially highly skilled attacker is not
Copyright© 2005 KONICA MINOLTA BUSINESS TECHNOLOGIES, INC., All Rights Reserved
