Bird Technologies 429-83H-01 Series-Manual User Manual
Page 42
TX RX Systems Inc. Manual 7-9439-6 09/03/09 Page 34
8) TTA LAN port configuration information will be
displayed as well as the Change Setup Menu
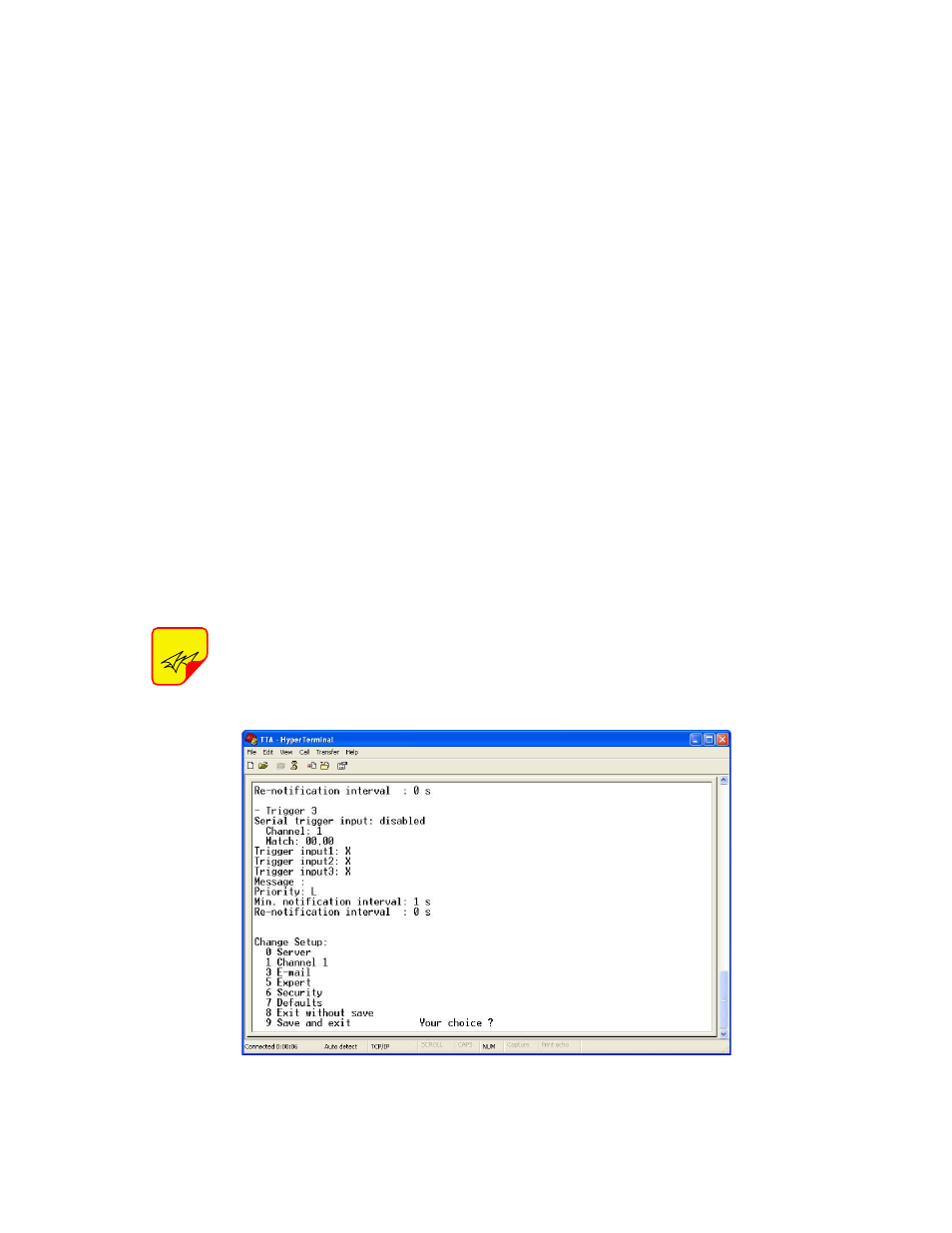
as shown in Figure A8. For Your Choice type in
“0” to select Server and press the ENTER key.
9) Enter the new IP address information that was
provided to you from your IT support personnel.
10) To finalize your selections choose (9) to save
the new information and exit the Setup Menu.
Close the HyperTerm utility program.
11) Disconnect your laptop from the TTA. Connect
your network cable (straight through type as
shown in figure A2) to the front panel LAN con-
nector. The TTA system can now be accessed
through your network the same as you would
any network connected device.
12) From your remote computer, in your web
browser’s address box type-in the new IP
address of the TTA system. The web page
interface to the TTA should appear in your
remote computer’s browser window. The first
time you launch the web page you may notice
that the JAVA applet will load first.
For a complete description of the
web based interface software
refer to the TX RX Systems Inc.
technical manual 7-9440.
TTA Network Port Security
In order to strengthen the security of the device
and protect against network intruders, the LAN port
is configured with the default security precautions
described below.
DATA ENCRYPTION
The web interface uses data encryption to protect
the data exchange between the TTA system and
the attached device. The port employs 128-bit data
encryption using the Rijndael algorithm and a spe-
cial encryption key set at the factory.
SNMP SUPPORT DISABLED
This will prevent unauthorized SNMP access. If
SNMP is required to be used for network manage-
ment, this will need to be re-enabled and setup as
desired by your network administrator
TELNET SECURITY
A factory default Telnet password has been added
to deter anyone from accessing the product
through the Telnet port without proper authoriza-
tion. It is recommended that the user concerned
with high security should change this to a pass-
word of choice. The procedure for doing this is
explained in the next section.
NOTE
Figure A8: The Change Setup Menu.
